Welcome to our website! In today’s digital age, cyber security is of utmost importance. With the increasing number of cyber threats and attacks, it is crucial for individuals and organizations to have a strong understanding of cyber security fundamentals. In this post, we will introduce you to a comprehensive guide titled “Cyber Security Fundamentals PDF”. This guide is designed to provide you with the essential knowledge and skills to protect yourself and your digital assets from cyber threats.
In the following sections, we will delve into the key topics covered in the Cyber Security Fundamentals PDF. We will start by exploring the concept of cyber security and its significance in our daily lives. Understanding the basics of cyber security is essential for anyone who uses the internet, as it helps us identify potential risks and take necessary precautions to mitigate them.
Overview of the Guide
The Cyber Security Fundamentals PDF also covers the importance of strong passwords and encryption techniques. Passwords are often the first line of defense against unauthorized access, and using weak or easily guessable passwords can leave us vulnerable to attacks. The guide will provide tips and best practices for creating strong passwords and implementing encryption to safeguard our sensitive information.


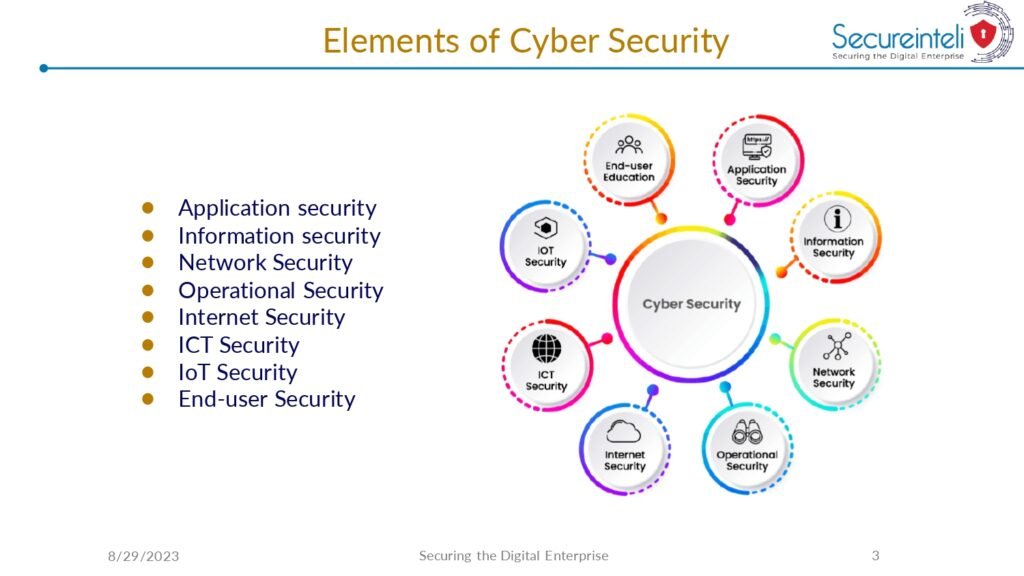
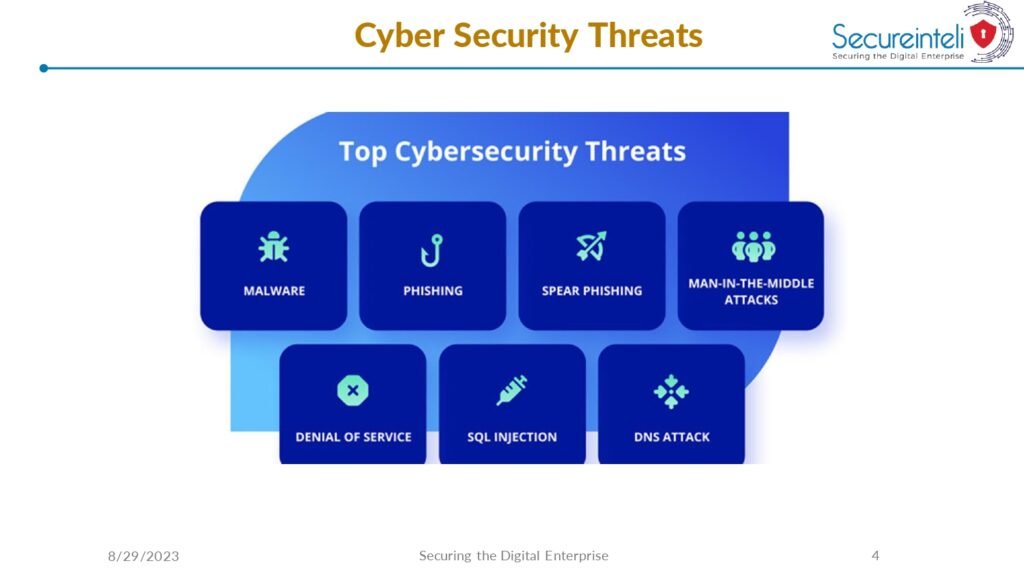



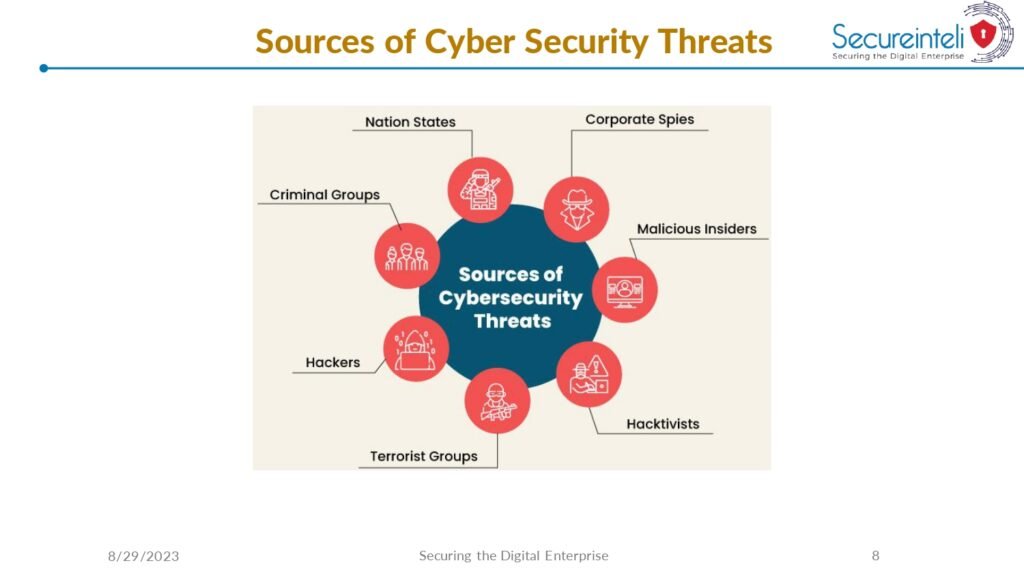


The guide also covers the essential tools and technologies used in cyber security, including firewalls, intrusion detection systems, and encryption algorithms. It provides detailed explanations of how these tools work and how they can be effectively deployed to protect against common cyber attacks.
Key Topics
Throughout the guide, several key topics are covered in detail. These topics include:
- Understanding the different types of malware and how to protect against them
- Securing your wireless networks to prevent unauthorized access
- Implementing strong passwords and two-factor authentication
- Recognizing phishing attempts and avoiding falling victim to them
- Understanding the role of encryption in securing your data
- Keeping your software and operating systems up to date
- Creating backups of your important data
- Protecting yourself from social engineering attacks
- Securing your mobile devices and protecting your personal information
- Using secure browsing practices to avoid malicious websites
By understanding and implementing these key topics, you will significantly enhance your cyber security posture and reduce the risk of falling victim to cyber attacks. In the following sections, we will delve into each topic in more detail, providing you with practical tips and strategies to effectively safeguard your digital life.
Download from Link
To access the “Cyber Security Fundamentals PDF” guide, simply click on the following link: [From here].
Once downloaded, you can save it to your device and refer to it whenever needed. We highly recommend that you take the time to read through the guide thoroughly and implement the best practices outlined within.