Introduction
Welcome to our comprehensive guide on OWASP API Security Top 10. In this guide, we will provide you with valuable insights into the key security risks associated with APIs and how to mitigate them effectively. APIs (Application Programming Interfaces) have become a crucial component of modern software development, enabling different applications to communicate and share data. However, with this increased connectivity comes the risk of potential vulnerabilities and security breaches. This guide aims to equip developers, security professionals, and anyone interested in API security with the necessary knowledge to protect their systems and data.
Overview of the Guide
The OWASP API Security Top 10 PDF is a comprehensive document that highlights the most critical security risks faced by APIs. It offers a detailed analysis of each risk, along with recommended best practices to address them. This guide is an essential resource for organizations that want to ensure the security and integrity of their APIs.
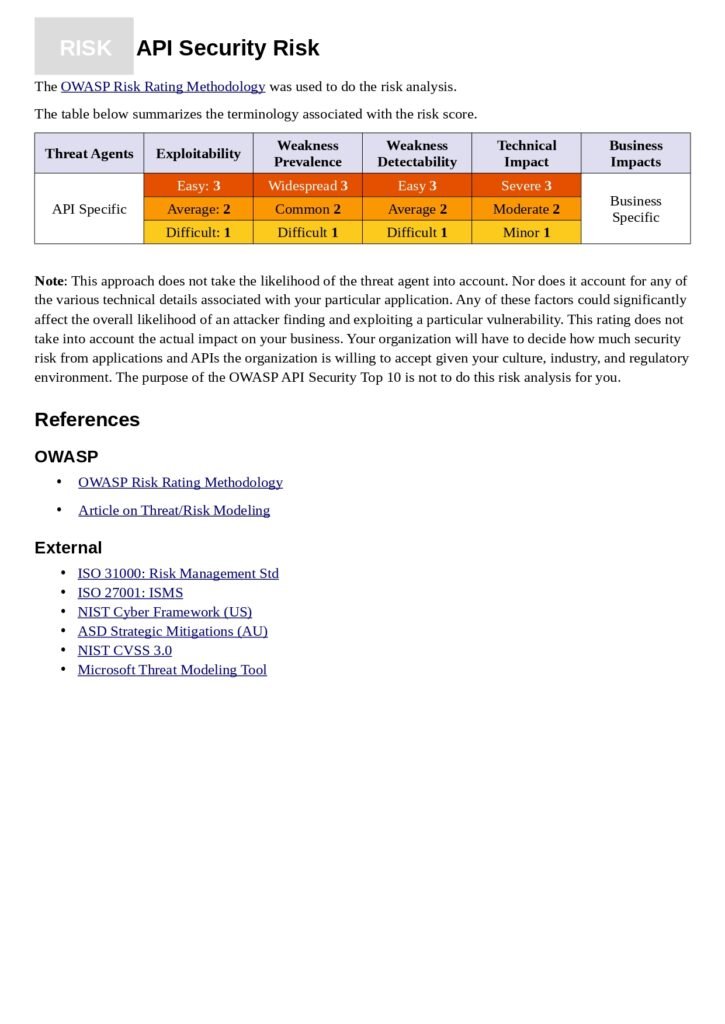
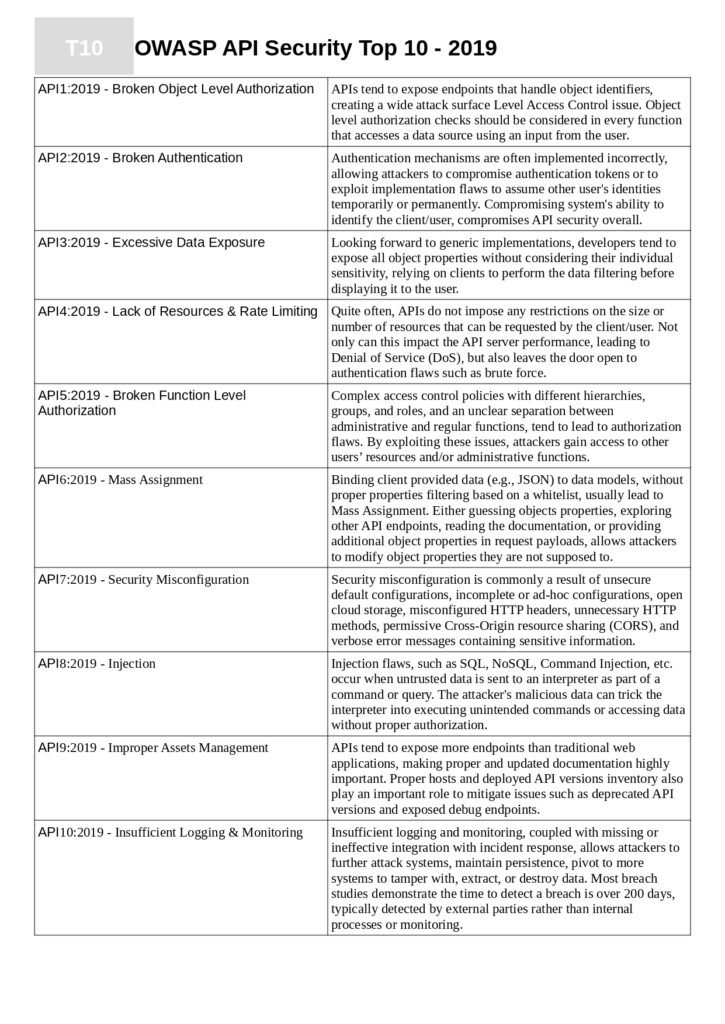

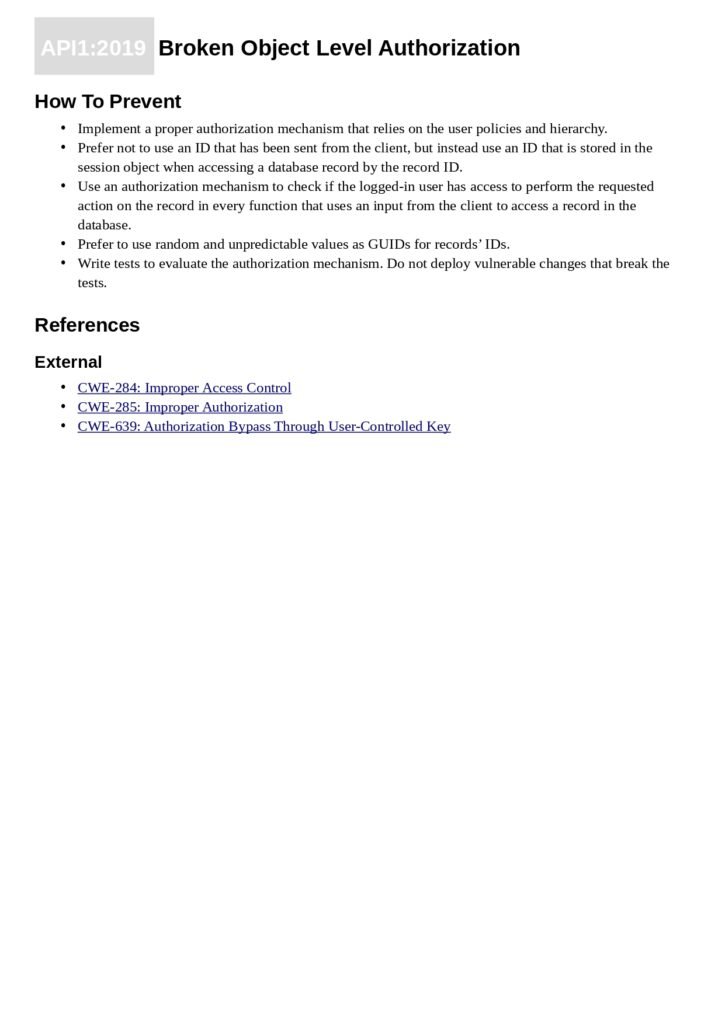


The Content of the Guide
The guide is divided into ten sections, each focusing on a specific security risk associated with APIs. These risks have been identified and prioritized based on real-world data and expert analysis. The content covers a wide range of topics, including:
- API Injection
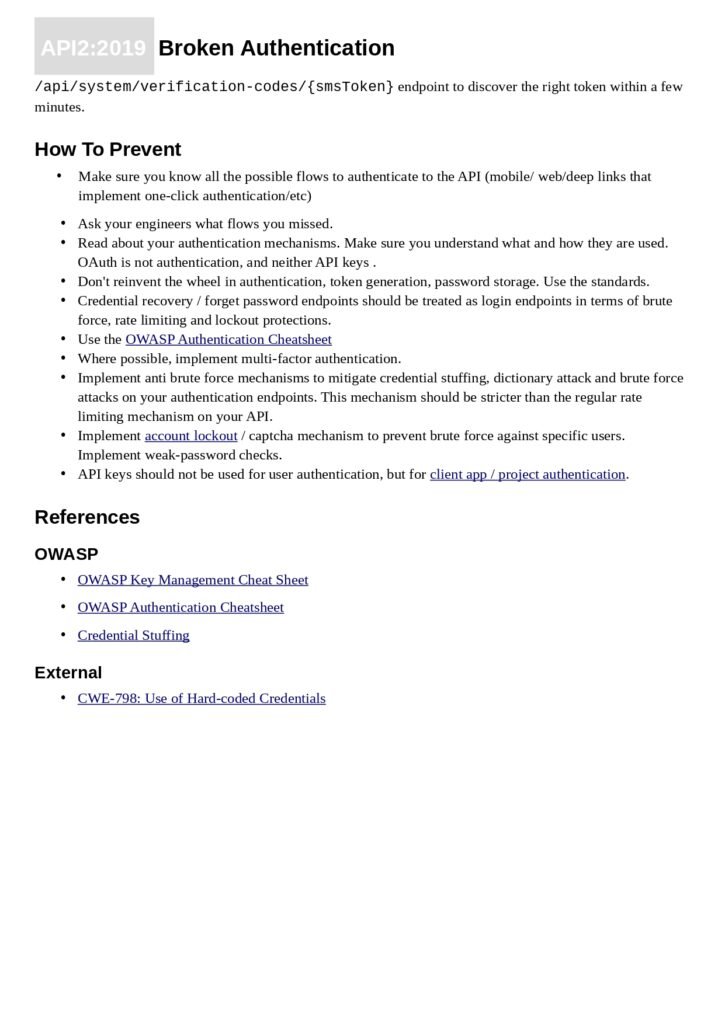
- Broken Object Level Authorization
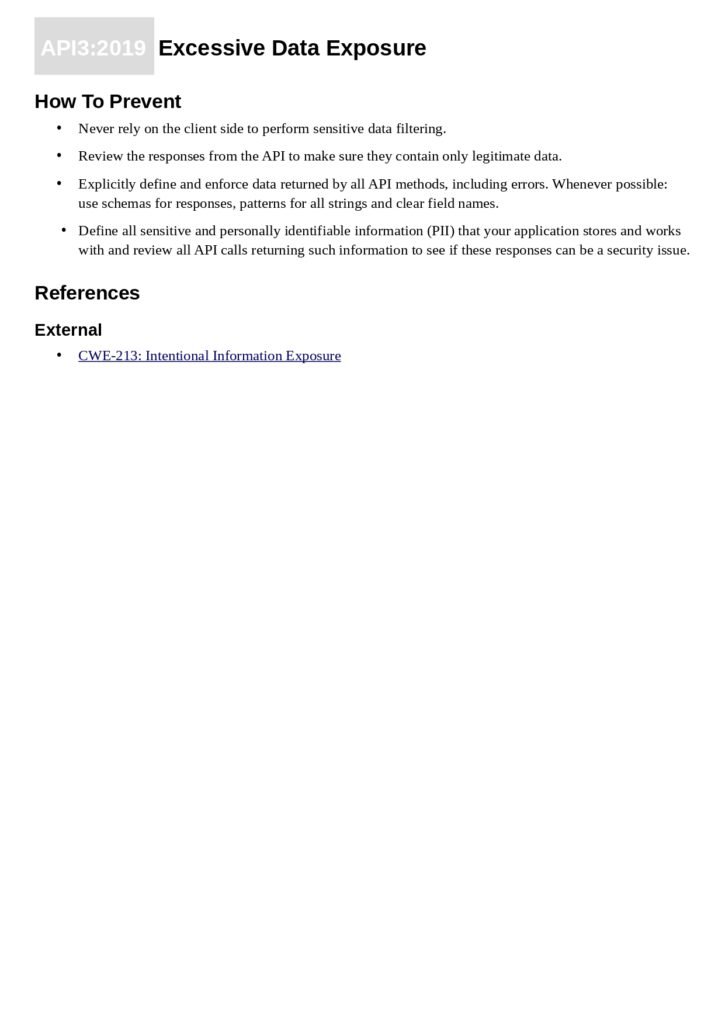
- Excessive Data Exposure
- Lack of Resources and Rate Limiting
- Broken Function Level Authorization
- Mass Assignment
- Security Misconfiguration
- Injection Attacks
- Improper Assets Management
- Insufficient Logging and Monitoring
Each section provides a detailed explanation of the risk, its potential impact, and practical steps to mitigate it. By following the recommendations outlined in this guide, organizations can significantly enhance the security posture of their APIs.
Key Topics
The guide covers a wide range of key topics related to API security. Some of the important areas discussed include:
- Understanding the anatomy of an API security breach
- Identifying common vulnerabilities and attack vectors
- Implementing secure coding practices for API development
- Utilizing authentication and authorization mechanisms effectively
- Implementing proper input validation and output encoding
- Securing sensitive data transmission
- Implementing effective logging and monitoring strategies
Conclusion
API security is a critical aspect of any modern software ecosystem. By understanding the risks and implementing the recommended best practices outlined in the OWASP API Security Top 10 guide, organizations can significantly reduce the likelihood of security breaches and protect their valuable data. It is crucial for developers, security professionals, and decision-makers to stay updated with the latest security trends and ensure that their APIs are designed and implemented securely.
Number of Pages (31 Pages)
The OWASP API Security Top 10 PDF guide consists of 31 pages packed with valuable information and practical insights. It covers a wide range of topics and provides in-depth analysis of each security risk. Whether you are a beginner or an experienced professional, this guide is an invaluable resource for enhancing your understanding of API security.
Download From Link
To download the OWASP API Security Top 10 PDF guide, please visit the following link: [download link here]. We encourage you to share this guide with your colleagues and peers to spread awareness about the importance of API security.
Thank you for choosing our guide as your resource for understanding and implementing API security best practices. We hope this guide proves to be a valuable asset in your journey towards securing your APIs and protecting your organization from potential security threats.