In the realm of cybersecurity, penetration testing plays a critical role in identifying vulnerabilities and securing systems. Kali Linux, a specialized Linux distribution, has become the go-to operating system for penetration testing professionals worldwide. To aid aspiring ethical hackers and security enthusiasts, we present the “Penetration Testing with Kali Linux” guide in PDF format.
This comprehensive resource provides essential knowledge, practical techniques, and command-line references to help you master the art of penetration testing using Kali Linux. Let’s dive into this guide and unlock the power of ethical hacking!
Understanding Penetration Testing:
Penetration testing, also known as ethical hacking, is the process of assessing the security of computer systems, networks, and applications by simulating real-world attacks. The “Penetration Testing with Kali Linux” guide offers a comprehensive introduction to penetration testing, covering its importance, methodologies, and legal considerations.


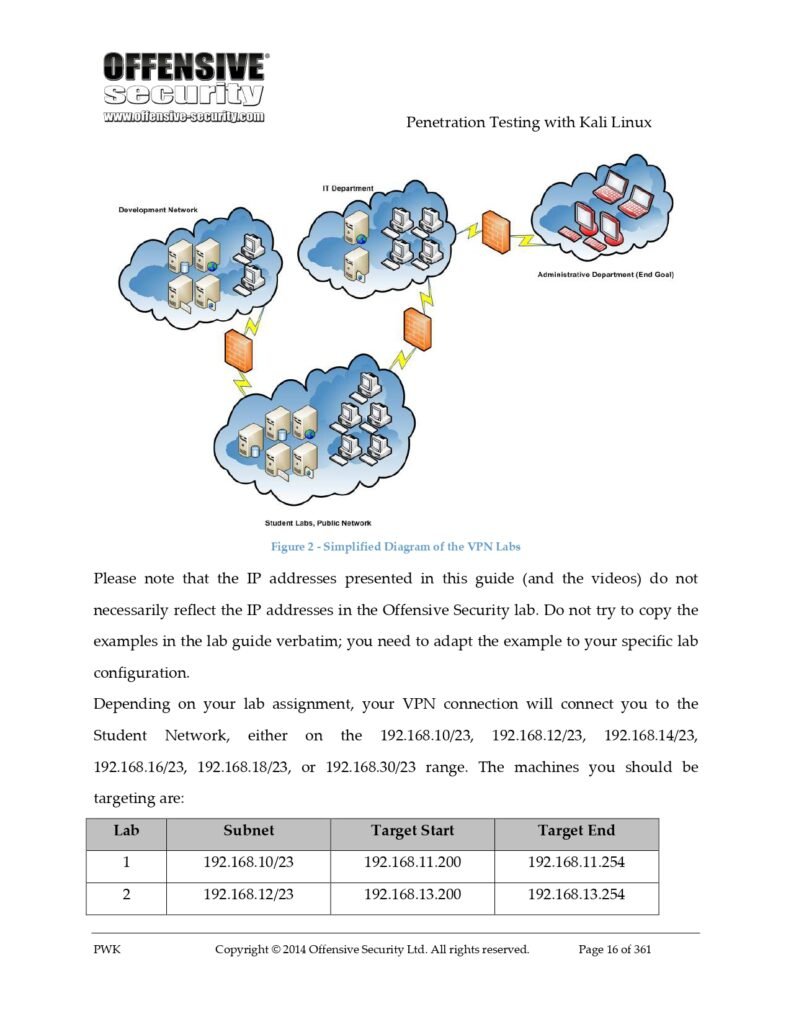
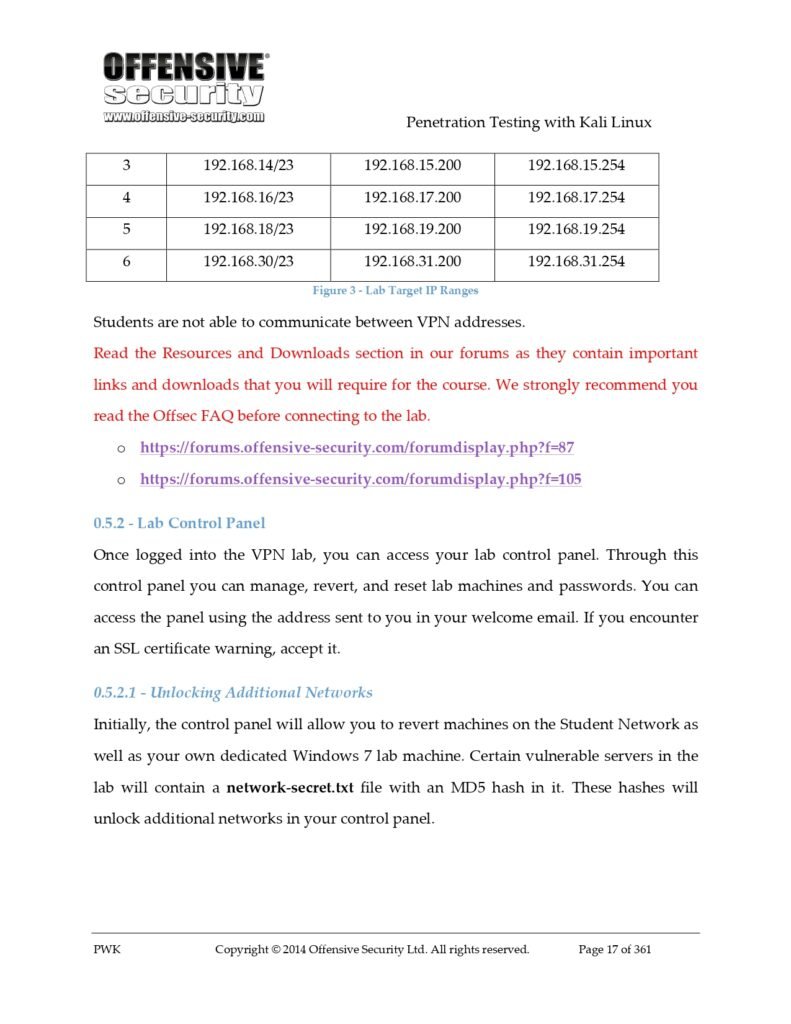


Exploring Kali Linux:
Kali Linux, developed specifically for penetration testing and digital forensics, provides a rich arsenal of tools and resources. The guide delves into the following aspects of Kali Linux:
- Penetration Testing: What You Should Know
- Getting Comfortable with Kali Linux
- The Essential Tools
- Passive Information Gathering
- Active Information Gathering
- Vulnerability Scanning
- Buffer Overflows
- Win32 Buffer Overflow Exploitation
- Linux Buffer Overflow Exploitation
- Working with Exploits
- File Transfers
- Privilege Escalation
- Client Side Attacks
- Web Application Attacks
- Password Attacks
- Port Redirection and Tunneling
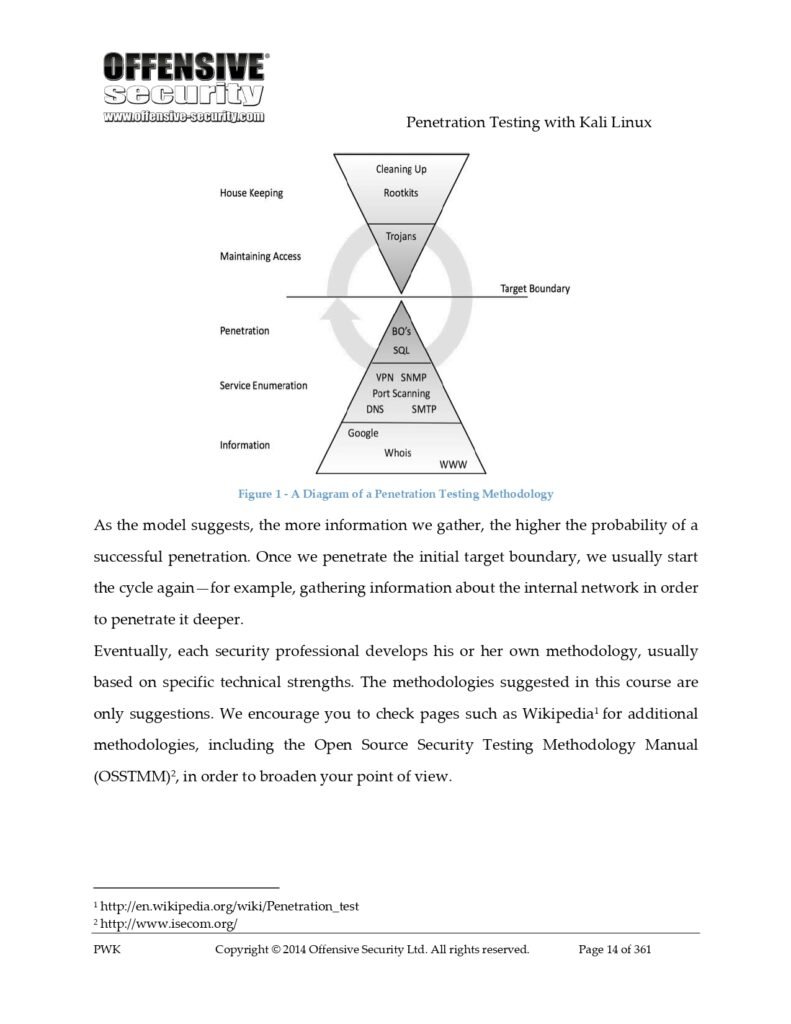
Penetration Testing Methodology:
The “Penetration Testing with Kali Linux” guide provides a structured approach to conducting effective penetration tests. Explore the following key phases of a penetration testing methodology:
a. Planning and Reconnaissance: Learn how to gather information about the target system, identify potential vulnerabilities, and develop a comprehensive testing plan.
b. Scanning and Enumeration: Utilize Kali Linux tools to scan for open ports, identify running services, and enumerate system details. Discover techniques for identifying potential entry points and weaknesses.
c. Exploitation and Post-Exploitation: Understand how to exploit vulnerabilities and gain unauthorized access to systems. Learn about privilege escalation, maintaining access, and post-exploitation activities to gather valuable information.
d. Reporting and Documentation: Master the art of documenting and reporting penetration test findings. Learn to communicate vulnerabilities, potential impact, and recommended remediation measures to stakeholders effectively.
Practical Penetration Testing Techniques:
The “Penetration Testing with Kali Linux” guide offers practical techniques to enhance your penetration testing skills using Kali Linux:
a. Web Application Testing: Discover tools and methodologies for testing web applications, including vulnerability scanning, SQL injection, cross-site scripting (XSS), and session hijacking.
b. Wireless Network Testing: Explore techniques for assessing the security of wireless networks, including capturing and analyzing network traffic, cracking WEP and WPA/WPA2 encryption, and identifying rogue access points.
c. Social Engineering: Understand the art of social engineering attacks and how to test an organization’s susceptibility to these attacks. Learn to simulate phishing, pretexting, and other social engineering techniques to evaluate human vulnerabilities.
d. Password Cracking: Explore password cracking techniques using Kali Linux tools such as John the Ripper and Hashcat. Learn about different password hashing algorithms, password policy weaknesses, and strategies for creating strong passwords.
Nu Of Pages:
300 Pages
To Download PDF:
Explore Our Linux Notes From here