In the ever-evolving landscape of cyber threats, having a comprehensive understanding of the network layer is crucial for effective cyber security. The network layer serves as a critical component in the transmission of data and communication between devices.
To help you delve deeper into this essential area, we present “Cyber Security In-Depth: Exploring the Network Layer with CS Lesson 3 PDF Guide.” This comprehensive guide serves as your next step in enhancing your knowledge of cyber security, focusing specifically on the intricacies of the network layer.
Let’s embark on a journey to strengthen our understanding of network security and fortify our cyber defenses.


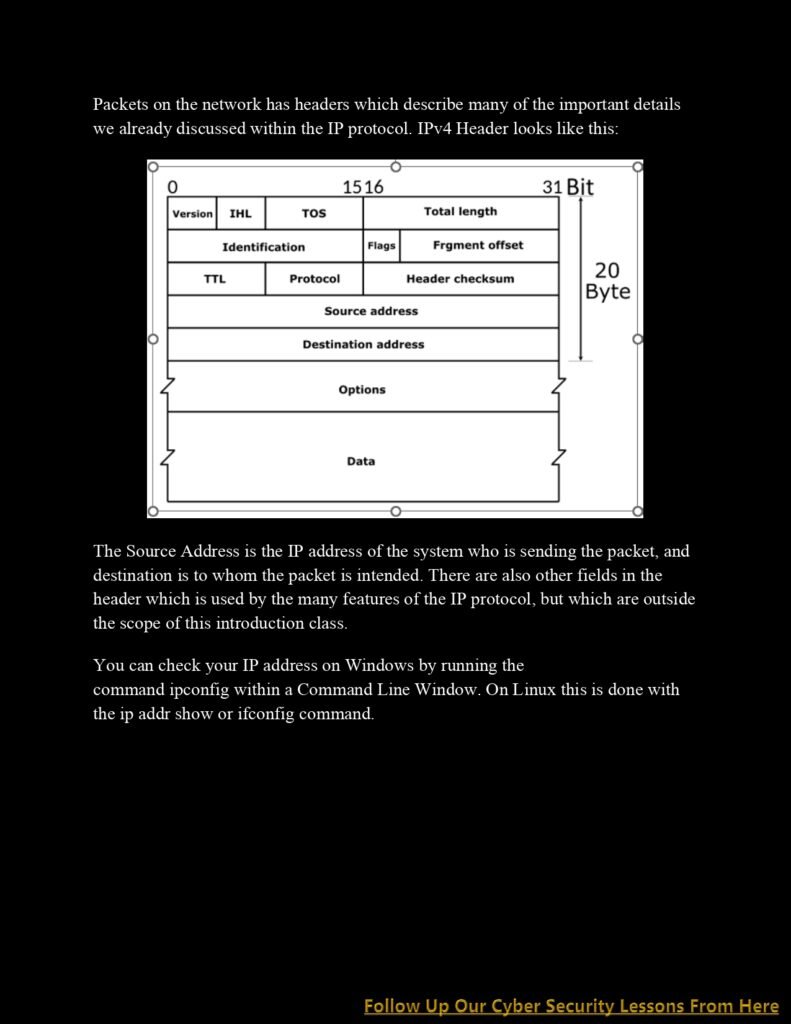
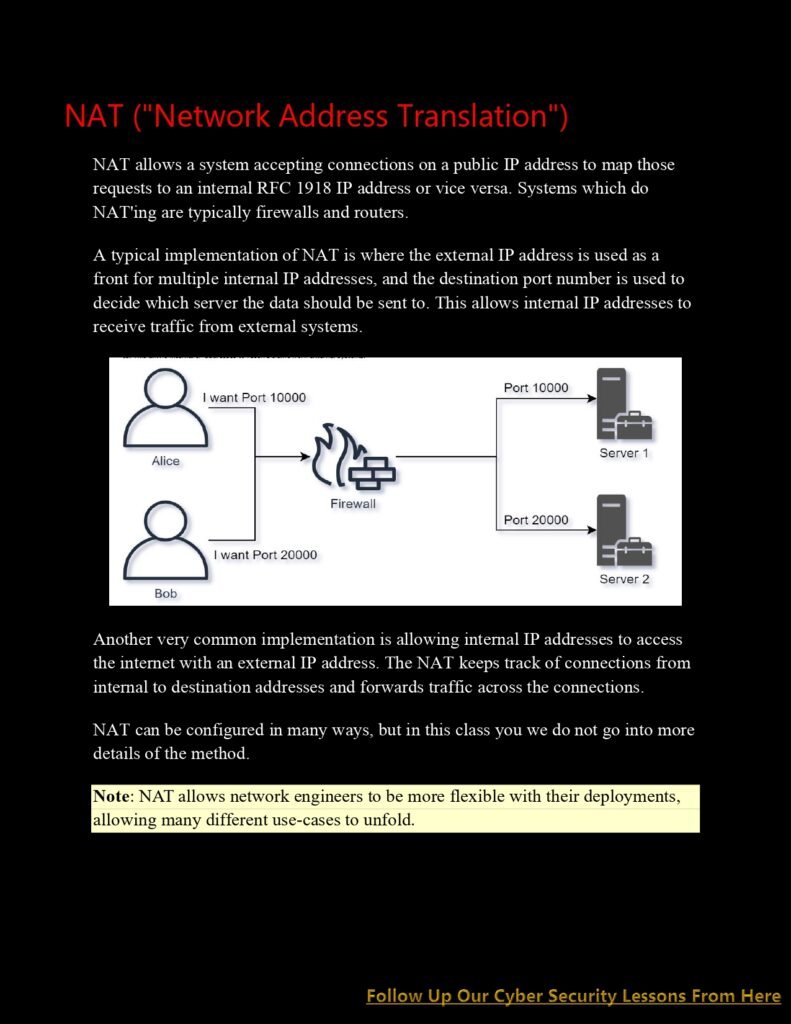



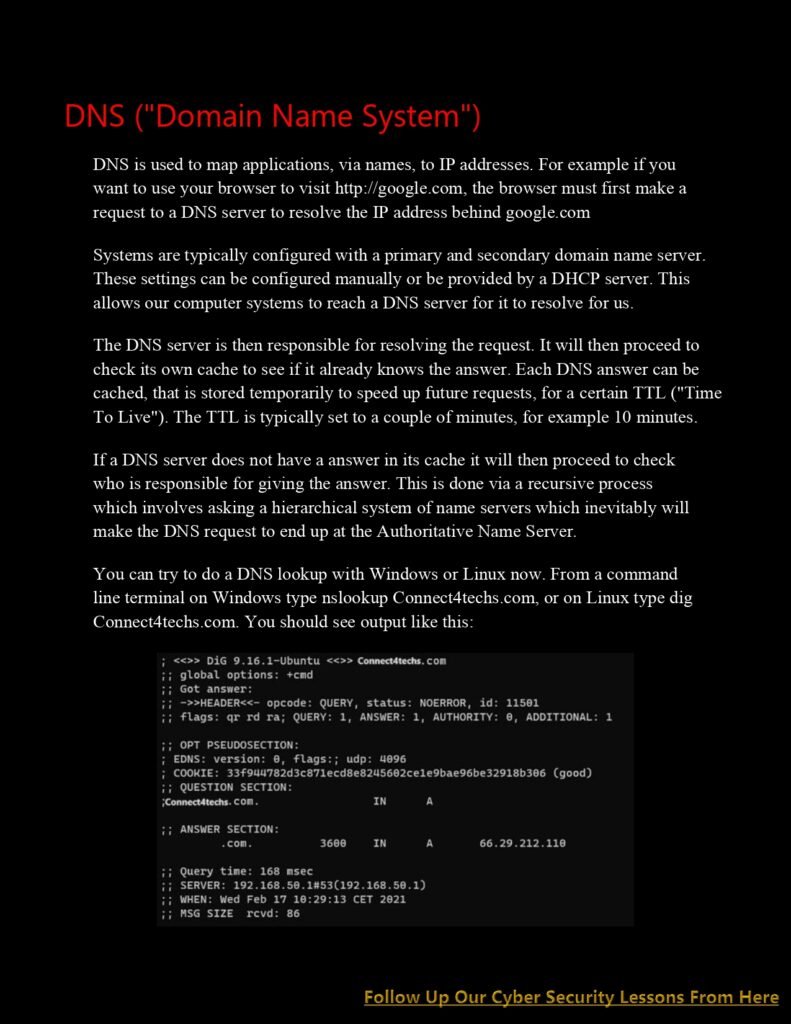

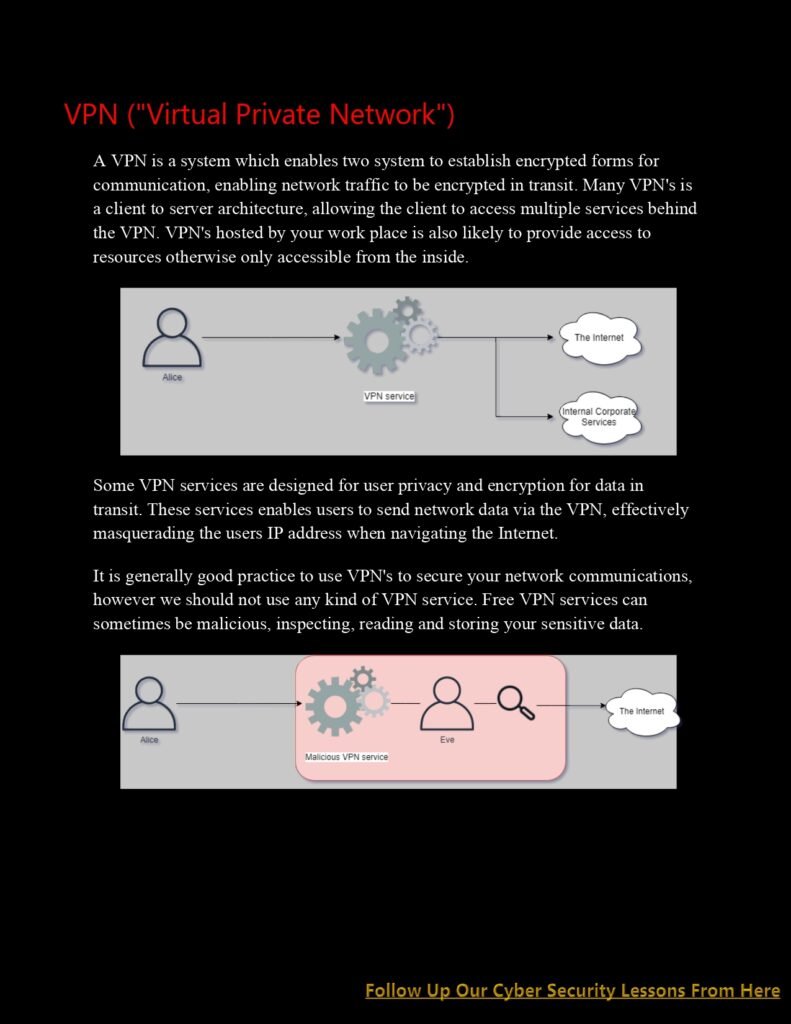
Uncovering Network Layer Essentials:
“Cyber Security In-Depth: CS Lesson 3 PDF Guide” provides an in-depth exploration of the network layer, covering the following key topics:
a. IP Addressing and Subnetting: Understand the structure and purpose of IP addresses and subnetting. Learn how to effectively allocate IP addresses, subnet networks, and manage IP routing.
b. Routing Protocols: Explore common routing protocols, such as Border Gateway Protocol (BGP), Open Shortest Path First (OSPF), and Routing Information Protocol (RIP). Gain insights into their functionalities and security considerations.
c. Network Address Translation (NAT): Discover how NAT enables the translation of private IP addresses to public IP addresses and facilitates communication between different network domains. Understand its impact on network security and best practices for its implementation.
Strengthening Network Layer Security:
“Cyber Security In-Depth: CS Lesson 3 PDF Guide” offers practical guidance on enhancing network layer security. The guide includes:
a. Access Control Lists (ACLs): Learn how to configure and implement ACLs to control network traffic and enforce security policies. Understand the importance of granular access control and the implications of misconfigured ACLs.
b. Virtual Private Networks (VPNs): Explore the concept of VPNs and their role in establishing secure and private communication channels over public networks. Understand different VPN protocols and considerations for deploying and managing VPN solutions.
c. Intrusion Detection and Prevention Systems (IDS/IPS): Gain insights into IDS/IPS technologies and their significance in monitoring and protecting the network layer. Learn about different detection methods and best practices for configuring and managing these systems.
Benefits of the PDF Guide:
“Cyber Security In-Depth: CS Lesson 3 PDF Guide” offers several benefits to individuals seeking to deepen their understanding of the network layer in the context of cyber security:
a. Comprehensive Resource: The guide serves as a comprehensive resource, covering essential network layer concepts and their relevance to cyber security. It provides a solid foundation for individuals looking to strengthen their network security expertise.
b. Portability and Accessibility: The PDF format allows you to access the guide on multiple devices, making it convenient to learn about network layer intricacies and cyber security anytime, anywhere.
c. Offline Availability: Once downloaded, the PDF guide becomes an offline resource, ensuring that you have access to vital network layer and cyber security information even without an internet connection.
Conclusion:
“Cyber Security In-Depth: Exploring the Network Layer with CS Lesson 3 PDF Guide” equips you with the essential knowledge required to strengthen your network layer security expertise. By providing an in-depth exploration of network layer essentials and practical guidance on network security, this guide empowers you to effectively safeguard your digital infrastructure.
Download “Cyber Security In-Depth: CS Lesson 3 PDF Guide” and embark on your journey to mastering the network layer in the context of cyber security. Whether you’re an aspiring cyber security professional or a network administrator seeking to enhance your knowledge, this guide will support you at every step.
By implementing the best practices outlined in the guide, you can fortify the security of your network layer, mitigate risks, and defend against sophisticated cyber threats. Embrace “Cyber Security In-Depth: CS Lesson 3 PDF Guide” and take a significant stride towards enhancing your cyber security defenses.
Download “Cyber Security In-Depth: CS Lesson 3 PDF Guide” and equip yourself with the knowledge to secure your network layer effectively. Let’s prioritize a comprehensive understanding of the network layer in the context of cyber security and stay ahead of emerging threats.
Nu Of Pages:
10 Pages
Download The Lesson PDF:
Access The Others CS Lessons From Here

















