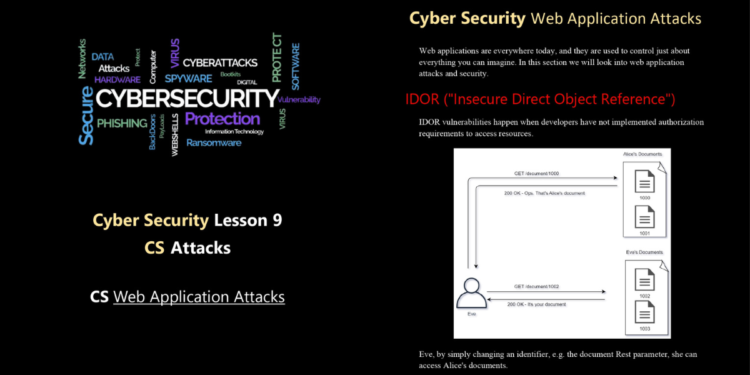
Web applications have become integral to our digital lives, facilitating online transactions, communication, and data sharing. However, they also present a lucrative target for cyber attackers. Web application attacks can compromise sensitive data, lead to financial losses, and damage an organization’s reputation.
To effectively protect web applications, it is crucial to understand the common attack vectors and implement robust security measures. In this blog post, we introduce the “Cyber Security Web Application Attacks: Safeguarding Your Web Presence with the CS Lesson 9 PDF Guide.”
This comprehensive guide serves as a valuable resource to enhance your knowledge of web application attacks, drawing insights from CS Lesson 9.
Let’s explore the world of web application security and equip ourselves to counter evolving cyber threats.







Understanding Web Application Attacks:
“Cyber Security Web Application Attacks: CS Lesson 9 PDF Guide” provides an in-depth exploration of web application attacks, covering the following key topics:
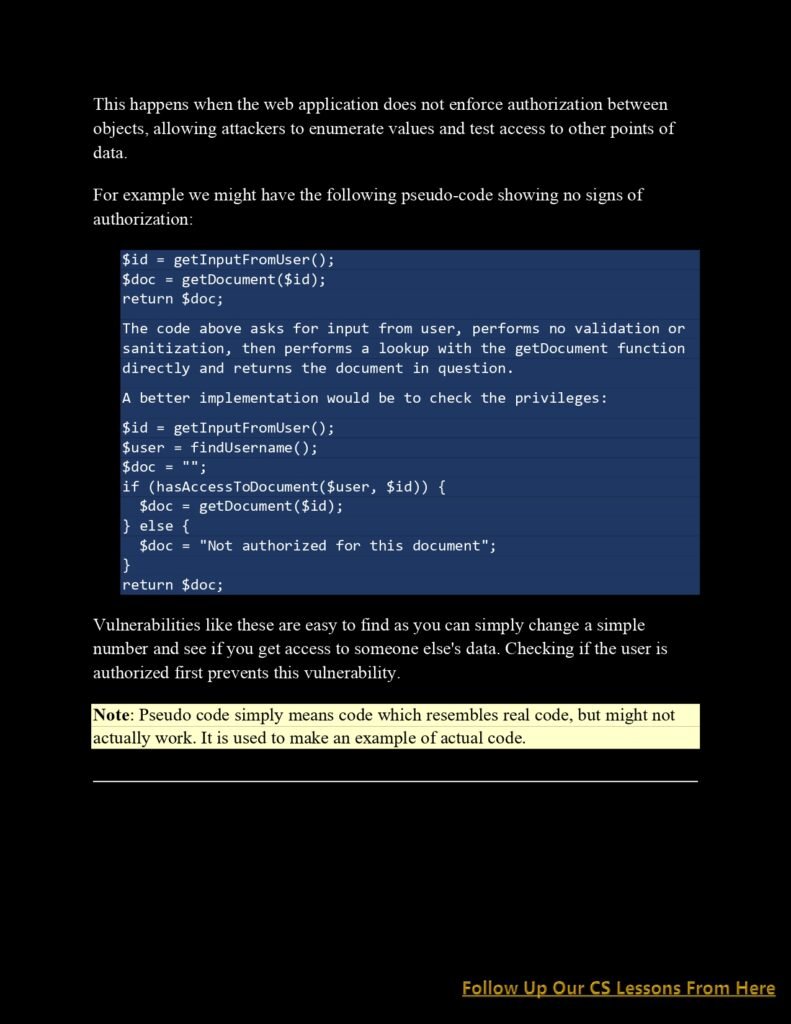
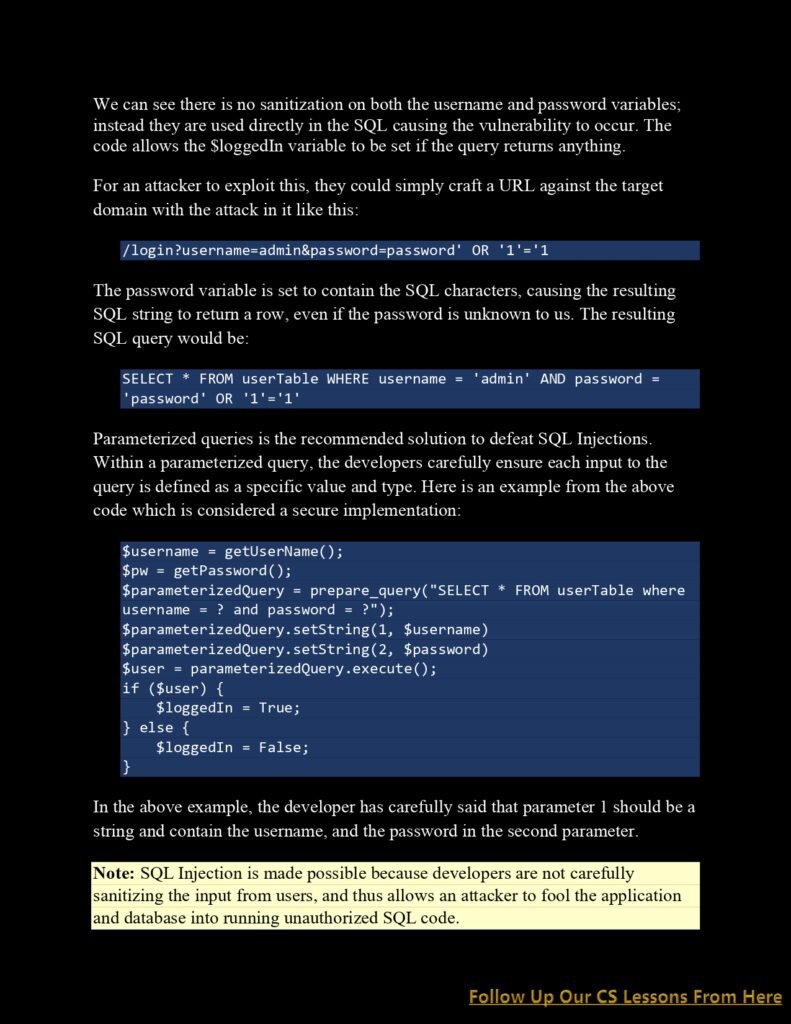
a. Injection Attacks: Gain insights into injection attacks such as SQL injection, command injection, and cross-site scripting (XSS). Understand how attackers exploit vulnerabilities in input validation and execution mechanisms to execute malicious code and gain unauthorized access.
b. Cross-Site Request Forgery (CSRF): Explore CSRF attacks and their potential impact on web applications. Learn about techniques to prevent CSRF attacks, including anti-CSRF tokens and secure coding practices.
c. Session Hijacking and Session Fixation: Understand how attackers can compromise user sessions through hijacking and fixation techniques. Discover the importance of secure session management, including session encryption, expiration, and randomization.
Web Application Security Best Practices:
“Cyber Security Web Application Attacks: CS Lesson 9 PDF Guide” offers practical guidance on securing web applications. The guide includes:
a. Input Validation and Output Encoding: Learn about the significance of input validation and output encoding in preventing injection attacks and protecting against code execution vulnerabilities. Understand how to implement secure coding practices to validate and sanitize user inputs.
b. Secure Authentication and Authorization: Discover essential techniques for secure authentication and authorization, including strong password policies, multi-factor authentication (MFA), and role-based access control (RBAC). Understand how to mitigate common authentication vulnerabilities such as brute-force attacks and credential stuffing.
c. Web Application Firewalls (WAFs): Explore the role of WAFs in detecting and mitigating web application attacks. Learn how to configure WAFs to analyze incoming traffic, identify malicious patterns, and apply security rules to protect web applications.
Benefits of the PDF Guide:
“Cyber Security Web Application Attacks: CS Lesson 9 PDF Guide” offers several benefits to individuals seeking to enhance their understanding of web application attacks and security best practices:
a. Comprehensive Resource: The guide serves as a comprehensive resource, covering essential web application attack types and providing practical guidance on securing web applications effectively.
b. Portability and Accessibility: The PDF format allows you to access the guide on multiple devices, making it convenient to learn about web application attacks and security measures anytime and anywhere.
c. Offline Availability: Once downloaded, the PDF guide becomes an offline resource, ensuring that you have access to vital web application security information even without an internet connection.
Conclusion:
“Cyber Security Web Application Attacks: Safeguarding Your Web Presence with the CS Lesson 9 PDF Guide” equips you with the essential knowledge required to understand and defend against web application attacks. By providing an in-depth exploration of web application attack techniques and security best practices, this guide empowers you to proactively protect your web applications from evolving cyber threats.
Download “Cyber Security Web Application Attacks: CS Lesson 9 PDF Guide” and embark on your journey to mastering web application security. Whether you’re a web developer, security professional, or an enthusiast seeking to enhance your knowledge, this guide will support you at every step.
With the insights and best practices provided in the guide, you can fortify the security of your web applications, detect and mitigate common vulnerabilities, and ensure the confidentiality and integrity of your data. Embrace “Cyber Security Web Application Attacks: CS Lesson 9 PDF Guide” and take a significant stride towards a resilient and secure web presence.
Download “Cyber Security Web Application Attacks: CS Lesson 9 PDF Guide” and equip yourself with the knowledge to protect your web applications effectively. Let’s prioritize a comprehensive understanding of web application attack techniques and implement robust security measures to defend against evolving cyber threats.
Nu Of Pages:
10 Pages
Download The Lesson PDF:
Access The Others CS Lessons From Here