In this digital age, where cyber threats are becoming increasingly sophisticated, it is crucial for organizations and individuals to prioritize cybersecurity. One of the most effective ways to identify vulnerabilities in a system is through penetration testing.
In this Lesson, we will delve into the topic of Cyber Security Penetration Testing, specifically focusing on Lesson 11, which covers important concepts and techniques. Additionally, we will provide an overview of the accompanying PDF resource that can serve as a valuable reference for individuals interested in enhancing their knowledge in this field.
Understanding Penetration Testing:
Penetration testing, often referred to as ethical hacking, is a systematic and controlled process of evaluating the security of a computer system, network, or application by simulating an attack. The objective of penetration testing is to identify vulnerabilities and weaknesses that malicious hackers could exploit. It is a crucial component of an organization’s overall security strategy, helping to identify potential risks and allowing for the implementation of appropriate security measures.

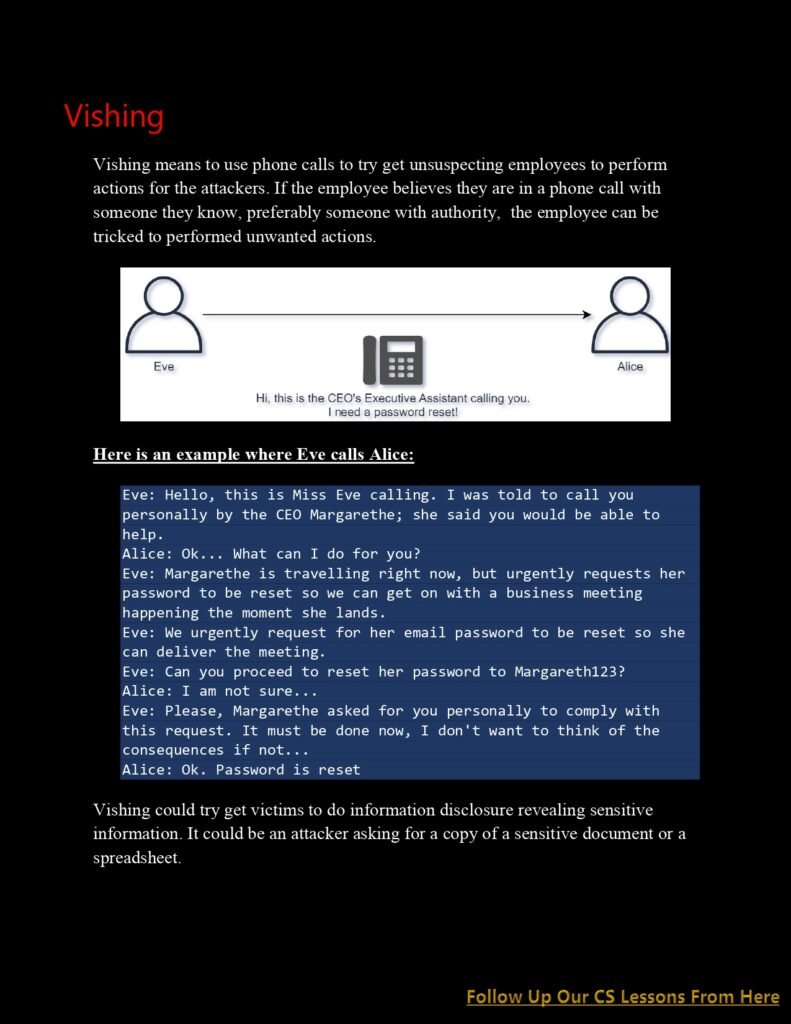
CS Lesson 11: Key Concepts and Techniques:
Lesson 11 of Cyber Security Penetration Testing delves into several important concepts and techniques that are essential for conducting effective penetration tests. Some of the key topics covered in this lesson include:
- Information Gathering: This phase involves collecting as much information as possible about the target system or network, including open ports, services running, and potential vulnerabilities. Various tools and techniques, such as port scanning, network mapping, and reconnaissance, are explored in detail.
- Scanning and Enumeration: Once information gathering is complete, the next step is to scan the target system for vulnerabilities. This phase involves identifying open ports, services, and potential entry points. Enumeration techniques are used to gather further information about the target, such as user accounts, shares, and system configurations.
- Exploitation: In this phase, penetration testers attempt to exploit the identified vulnerabilities to gain unauthorized access to the target system or network. The goal is to determine the extent to which an attacker could compromise the system’s security.
- Post-Exploitation: After successful exploitation, penetration testers focus on maintaining access to the target system and escalating privileges. This phase involves exploring the compromised system, identifying sensitive data, and potentially pivoting to other systems within the network.
The CS Lesson 11 PDF Resource:
The accompanying PDF resource for CS Lesson 11 provides a comprehensive overview of the concepts and techniques discussed in the lesson. It serves as a valuable reference for individuals wishing to deepen their understanding of penetration testing. The PDF contains detailed explanations, step-by-step instructions, and practical examples, making it an excellent learning tool for both beginners and experienced professionals.
Furthermore, the CS Lesson 11 PDF resource includes additional resources and references that readers can explore to further expand their knowledge in the field of penetration testing. These resources may include books, websites, online courses, and tools that can aid in developing practical skills and staying updated with the latest trends and techniques.
Conclusion:
In conclusion, Cyber Security Penetration Testing is a critical aspect of maintaining a robust security posture in the face of ever-evolving cyber threats. CS Lesson 11 provides a comprehensive exploration of key concepts and techniques involved in penetration testing, equipping individuals with the necessary knowledge and skills to identify vulnerabilities and protect their systems effectively.
The accompanying PDF resource serves as an invaluable reference material, providing further insights and facilitating continuous learning in this dynamic field. By staying proactive and prioritizing cybersecurity, organizations and individuals can mitigate risks, safeguard their digital assets, and contribute to a safer online environment.
Nu Of Pages:
7 Pages
Download The Lesson PDF:
Access The Others CS Lessons From Here

















