In the rapidly evolving landscape of cyber threats, organizations need robust security operations to protect their digital assets. Security operations involve various processes, technologies, and strategies that enable proactive threat detection, incident response, and continuous monitoring. In this blog post, we will explore the significance of security operations and delve into Lesson 13 of Cyber Security, which focuses on this critical aspect of cybersecurity. Additionally, we will introduce the accompanying PDF resource, which provides valuable insights and practical guidance for establishing effective security operations.
The Importance of Security Operations:
Security operations encompass a range of activities aimed at protecting an organization’s information systems and data. With the increasing sophistication and frequency of cyber attacks, having a well-defined security operations function becomes crucial for identifying, mitigating, and responding to threats effectively.







Security operations enable organizations to maintain a proactive security posture, detect and respond to incidents in a timely manner, and minimize the impact of security breaches.
CS Lesson 13: Establishing Effective Security Operations
Lesson 13 of the Cyber Security curriculum delves into the key components and processes involved in establishing effective security operations. This lesson covers the following essential aspects:
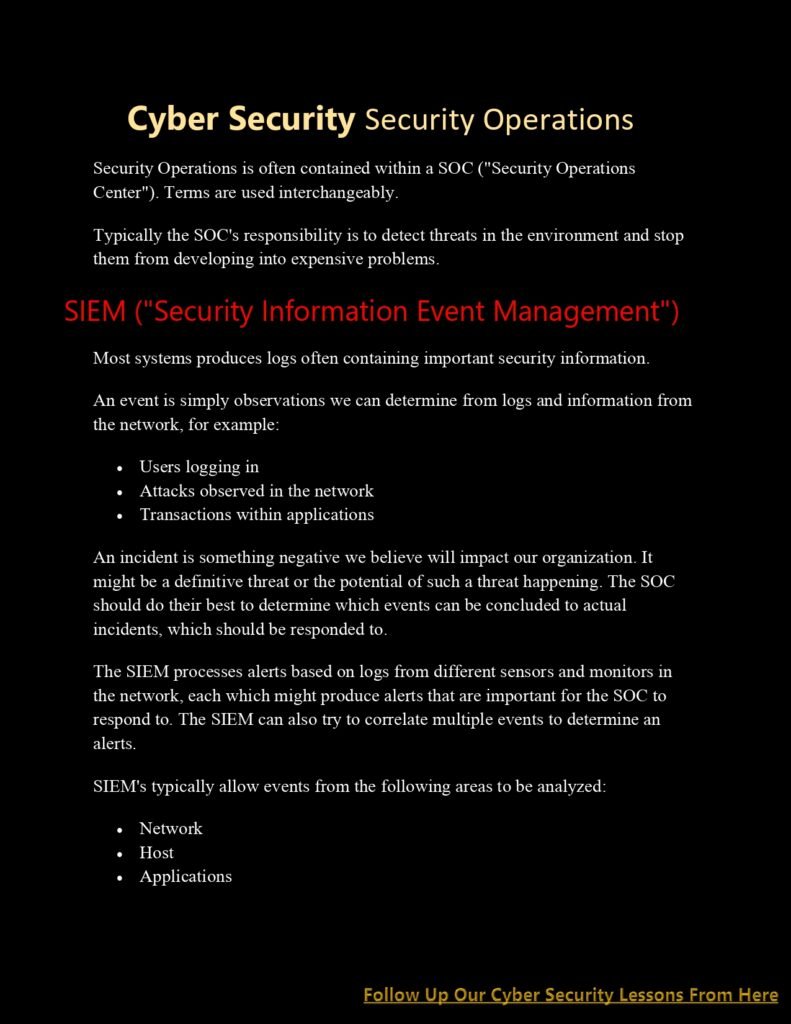
- Security Operations Center (SOC): Lesson 13 provides an overview of the Security Operations Center, which serves as the nerve center for security operations. It explores the SOC’s role in monitoring, analyzing, and responding to security incidents, as well as coordinating incident response activities.
- Threat Intelligence: The lesson emphasizes the significance of threat intelligence in security operations. It explains how threat intelligence feeds from various sources can provide valuable information about emerging threats, vulnerabilities, and adversary tactics, enabling proactive defense measures.
- Incident Response: Lesson 13 covers the incident response lifecycle, including preparation, identification, containment, eradication, and recovery. It outlines the importance of having well-defined incident response processes, incident playbooks, and incident management tools.
- Security Information and Event Management (SIEM): The lesson introduces SIEM systems, which are essential tools for centralizing, analyzing, and correlating security event data. It explores how SIEM solutions can enhance threat detection, automate incident response, and facilitate compliance monitoring.
The CS Lesson 13 PDF Resource:
The accompanying PDF resource for CS Lesson 13 provides a comprehensive guide to security operations, offering detailed explanations, practical examples, and actionable insights. It serves as a valuable reference for individuals interested in establishing or improving security operations within their organizations. The PDF covers topics such as SOC design and implementation, threat intelligence frameworks, incident response best practices, and SIEM system selection and configuration.
Furthermore, the CS Lesson 13 PDF resource includes additional references and resources for readers to explore further. These resources may include whitepapers, case studies, industry reports, and tools that provide insights into the latest trends, emerging technologies, and best practices in security operations.
Conclusion:
In conclusion, security operations play a vital role in safeguarding organizations against cyber threats. CS Lesson 13 focuses on establishing effective security operations, covering critical components such as Security Operations Centers, threat intelligence, incident response, and SIEM systems. By implementing the principles outlined in this lesson, organizations can enhance their ability to detect, respond to, and mitigate security incidents.
The accompanying PDF resource serves as a comprehensive guide, offering practical guidance and additional resources to support the establishment of robust security operations. By prioritizing security operations, organizations can strengthen their cybersecurity defenses and protect their valuable digital assets in today’s dynamic threat landscape.
Nu Of Pages:
8 Pages
Download The Lesson PDF:
Access The Others CS Lessons From Here

















