DLP, or Data Leakage Prevention, is a crucial aspect of information security in today’s digital age. With the increasing number of data breaches and cyber threats, organizations must take proactive measures to protect their sensitive data from unauthorized access or leakage.
At its core, DLP refers to the set of tools, technologies, and practices that aim to prevent the unauthorized transmission or disclosure of sensitive information. This can include personal identifiable information (PII), financial data, intellectual property, or any other information that could cause harm if it falls into the wrong hands.
Overview of the Guide
The consequences of a data breach can be severe, ranging from financial losses and reputational damage to legal and regulatory penalties. Therefore, implementing an effective DLP strategy is essential for organizations to safeguard their data and maintain trust with their customers and stakeholders.



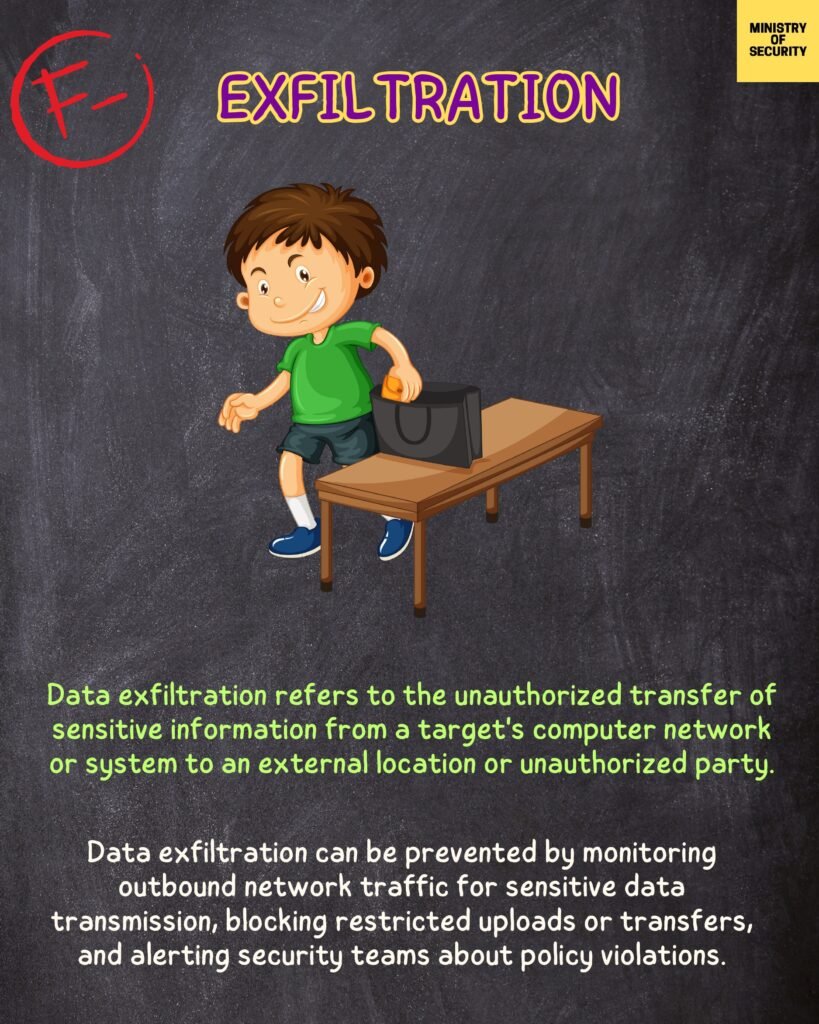






Our Playbook for DLP is designed to guide you through the process of implementing a robust DLP program within your organization. Whether you are a small business or a large enterprise, our playbook will provide you with practical insights, best practices, and step-by-step instructions to help you navigate the complex world of data leakage prevention.
In this guide, we will cover various aspects of DLP, including:
- The importance of DLP in today’s digital landscape
- The key components of a DLP program
- Common challenges and pitfalls in DLP implementation
- Best practices for developing DLP policies and procedures
- Choosing the right DLP solution for your organization
- Monitoring and auditing DLP activities
- Training and awareness programs for employees
- Measuring the effectiveness of your DLP program
By the end of this guide, you will have a comprehensive understanding of DLP and be equipped with the knowledge and tools to implement an effective data leakage prevention strategy in your organization.
The Content of the Guide
The Playbook for Data Leakage Prevention (DLP) guide covers a wide range of topics related to data security and protection. Here is a brief overview of what you can expect to find in the guide:
1. Understanding Data Leakage Prevention
In this section, we will provide an in-depth explanation of what data leakage prevention is and why it is crucial for organizations of all sizes. We will explore the different types of data leakage, such as accidental data leakage through email or file sharing, as well as intentional data theft by malicious insiders or external hackers. Additionally, we will delve into the potential consequences of a data breach, including financial losses, damage to reputation, legal implications, and regulatory compliance issues.
2. Assessing Your Data Security Needs
Before implementing any DLP measures, it is essential to assess your organization’s data security needs. This section will guide you through the process of identifying your most valuable and sensitive data, such as customer information, intellectual property, or trade secrets. We will help you understand the potential risks associated with each type of data and evaluate the impact of a data breach on your business operations. By conducting a thorough assessment, you will gain insights into the specific vulnerabilities your organization faces and be better equipped to prioritize your data protection efforts.
3. Developing a DLP Strategy
Once you have assessed your data security needs, it is time to develop a comprehensive DLP strategy. This section will walk you through the key steps involved in creating a robust DLP plan. We will provide guidance on policy development, including defining acceptable use policies, data classification, and access controls. Furthermore, we will help you conduct a risk assessment to identify potential threats and vulnerabilities, enabling you to prioritize your security measures effectively. Finally, we will provide implementation guidelines, including recommendations for deploying DLP technologies and establishing incident response procedures.
4. Implementing DLP Technologies
In this section, we will explore the various technologies available for implementing DLP measures. We will discuss the pros and cons of different solutions, such as data loss prevention software, encryption, access controls, and employee training. We will delve into the technical aspects of each technology, explaining how they work and their effectiveness in preventing data leakage. Additionally, we will provide practical guidance on selecting the right DLP solution for your organization based on your specific requirements, budget constraints, and existing IT infrastructure.
5. Monitoring and Incident Response
Monitoring is a critical aspect of any DLP strategy. This section will explain the importance of continuous monitoring and provide guidance on setting up an effective incident response plan. We will discuss the various monitoring techniques and tools available, such as network traffic analysis, data loss prevention software, and user behavior analytics. Additionally, we will emphasize the importance of employee awareness and training in preventing data leakage, as well as the role of incident response teams in quickly identifying and mitigating data breaches. By implementing robust monitoring and incident response processes, you can detect and respond to data leakage incidents promptly, minimizing the potential damage to your organization.
Key Topics
The Playbook for Data Leakage Prevention (DLP) guide covers several key topics, including:
- Data leakage prevention strategies
- Identifying sensitive data
- Developing DLP policies
- Implementing DLP technologies
- Employee training and awareness
- Monitoring and incident response
- Integration with cloud services
- Regulatory compliance
- Encryption and data protection
- Third-party risk management
- Data classification and labeling
- Insider threat detection
- Endpoint security
Overall, the Playbook for Data Leakage Prevention (DLP) guide provides a comprehensive overview of key topics and best practices for organizations looking to implement and strengthen their data leakage prevention efforts. By addressing these topics in a holistic manner, organizations can enhance their data protection capabilities and mitigate the risks associated with data leakage incidents.
Download from Link
To access our Playbook for Data Leakage Prevention (DLP) guide, please click on the following link: [From link].
We hope you find this guide informative and useful in your journey towards securing your organization’s data.

















