Web application security is a critical aspect of the digital landscape. As technology continues to advance, so do the threats that target web applications. Cybercriminals are constantly evolving their tactics to exploit vulnerabilities in web applications and gain unauthorized access to sensitive information. It is, therefore, imperative for organizations to understand the common vulnerabilities that exist and take proactive measures to protect their web applications.
The OWASP (Open Web Application Security Project) Top 10 vulnerabilities list is a widely recognized industry standard that outlines the most critical security risks faced by web applications. It is regularly updated by a community of security experts who analyze real-world data, trends, and emerging threats. The OWASP Top 10 serves as a valuable resource for organizations to prioritize their security efforts and focus on the vulnerabilities that pose the greatest risk.
In this guide, we will delve into each of the OWASP Top 10 vulnerabilities in detail, providing you with a comprehensive understanding of their impact and the techniques used by attackers to exploit them. We will also discuss best practices and mitigation strategies that can be implemented to safeguard your web applications against these vulnerabilities.
Overview Of This Guide



Our goal is to empower developers and security professionals with the knowledge and tools they need to build secure web applications. By understanding the common vulnerabilities and adopting security best practices, you can significantly reduce the risk of your web applications falling victim to cyberattacks.
Throughout this guide, we will provide practical examples, code snippets, and real-world scenarios to illustrate the concepts and techniques discussed. We encourage you to actively engage with the material, ask questions, and experiment with the suggested mitigation strategies in a controlled environment.
The Content of the Guide
Our guide covers each of the OWASP Top 10 vulnerabilities in detail, offering a comprehensive understanding of the risks involved and how to address them. The vulnerabilities covered in the guide are:
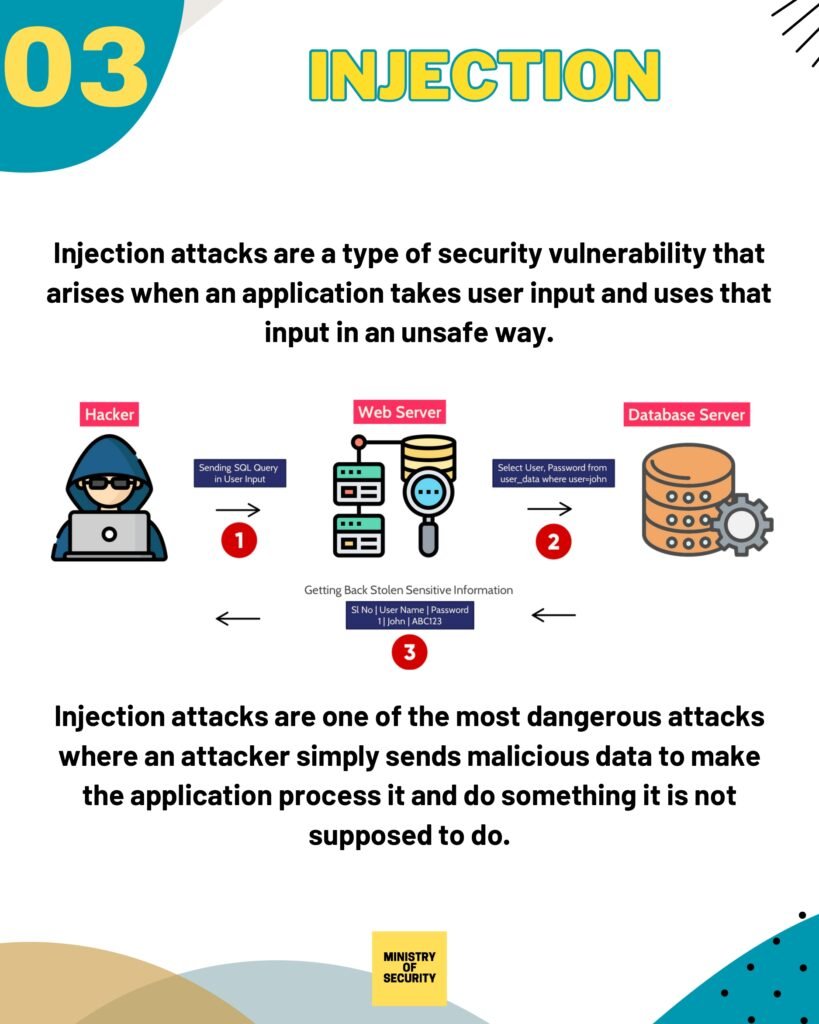
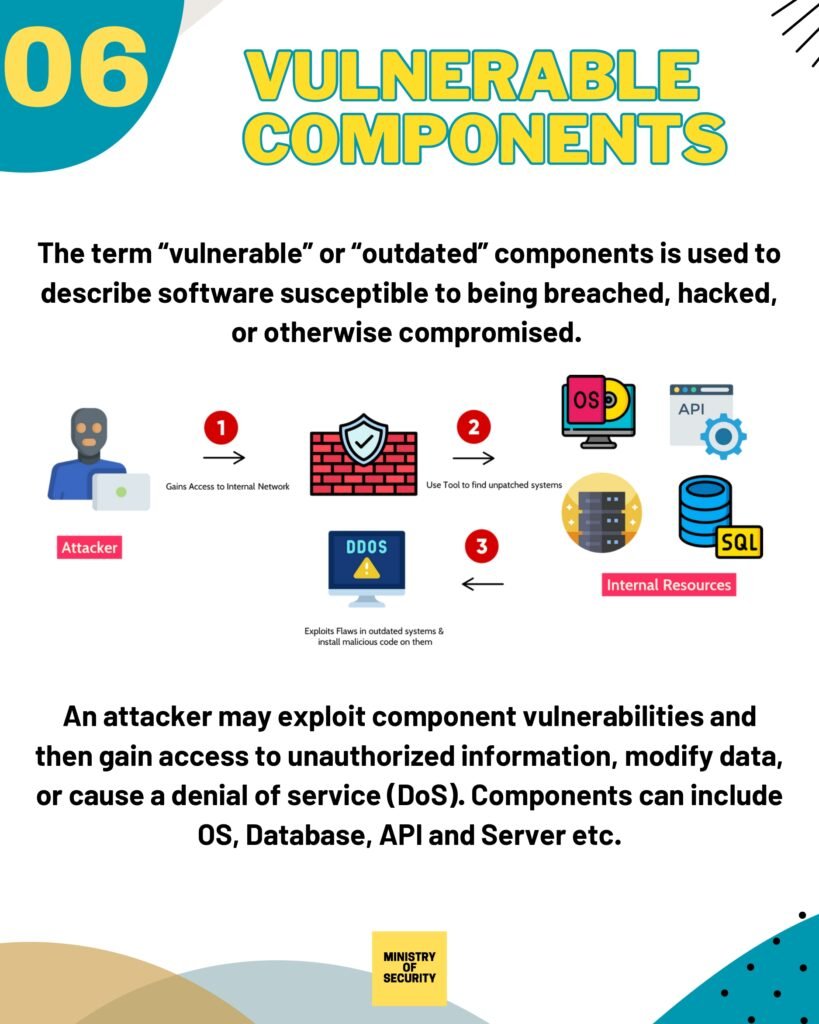
- Injection
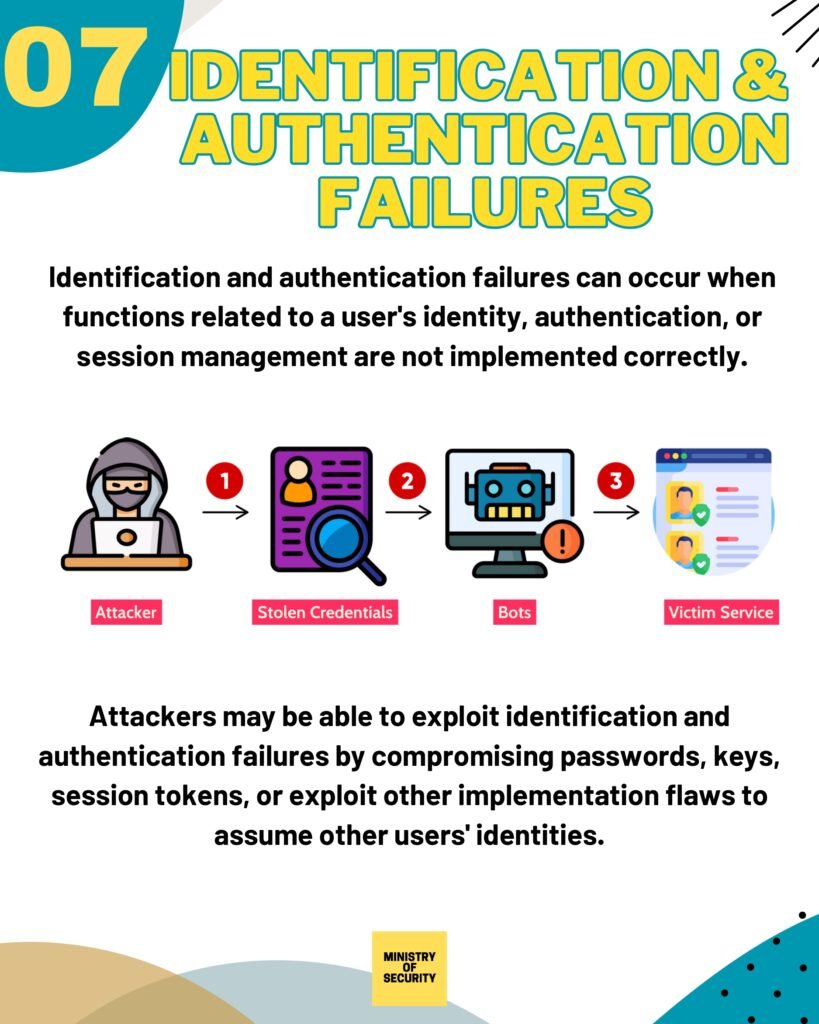
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
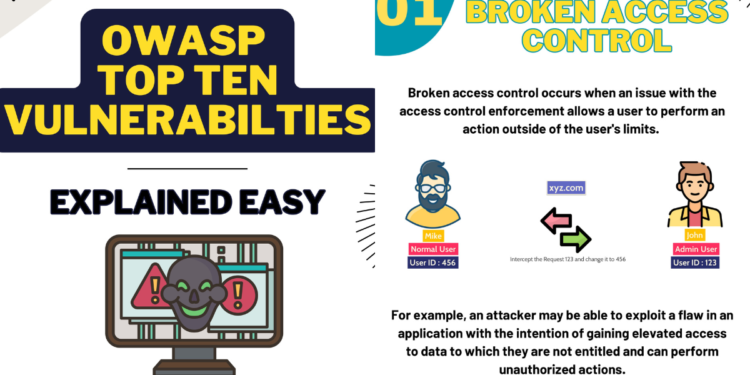
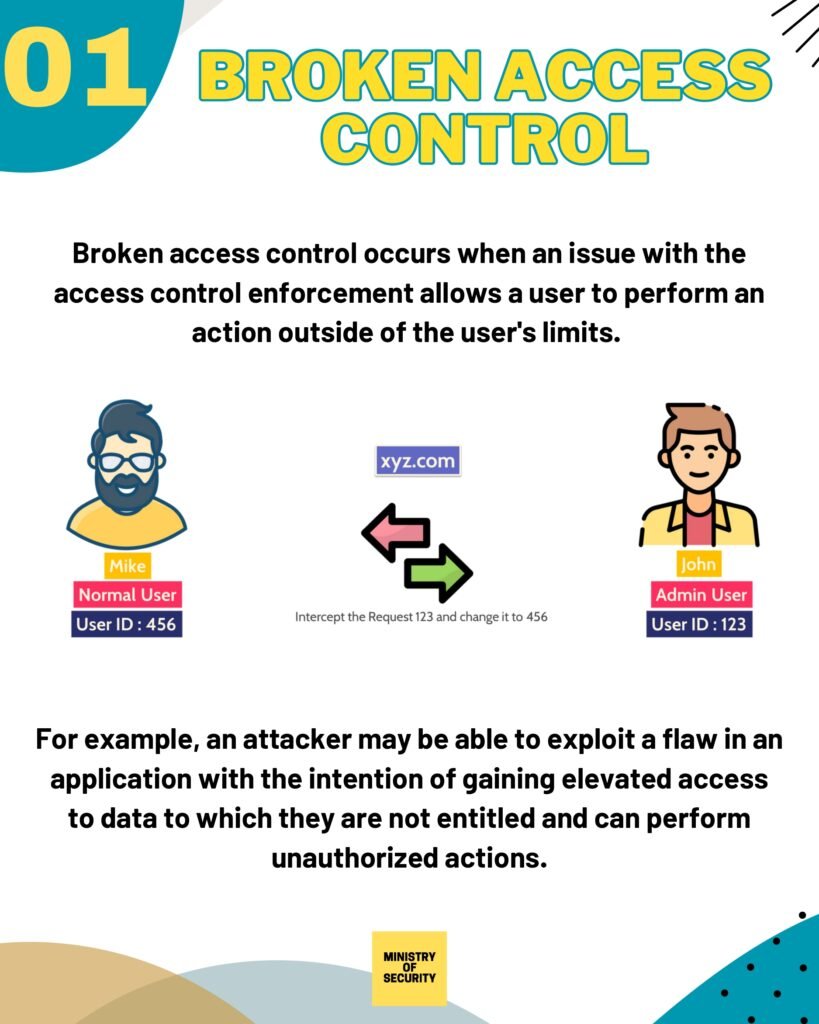
- Broken Access Control
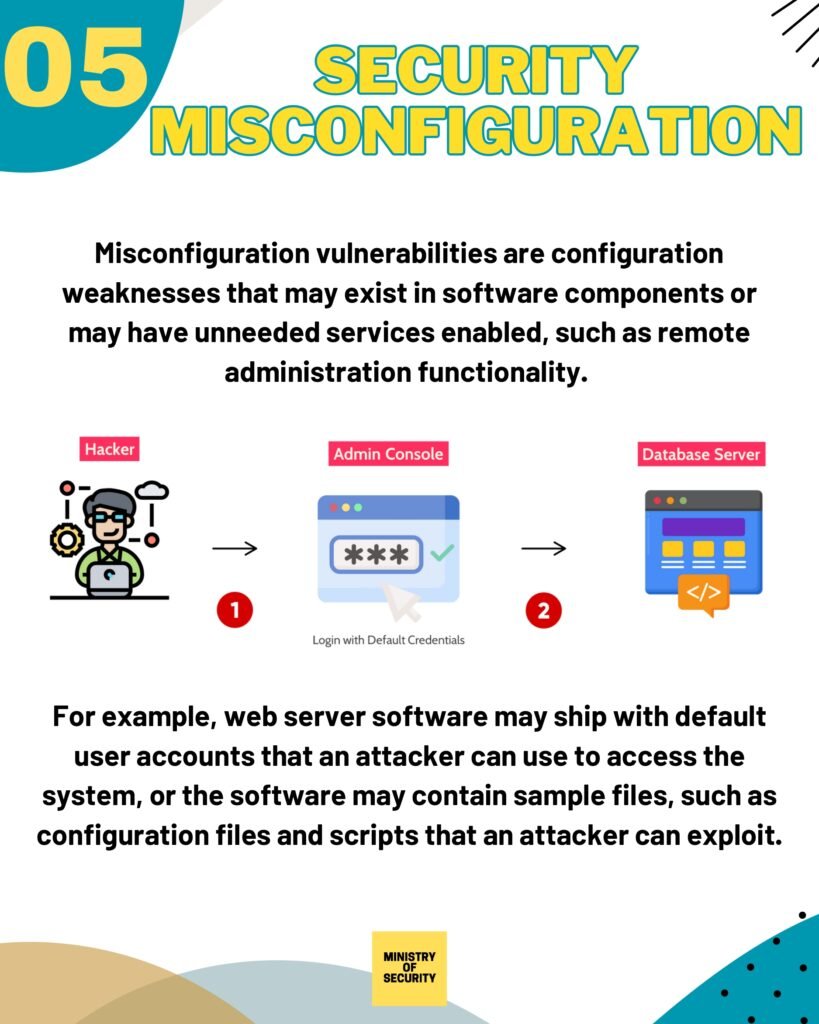
- Security Misconfiguration
- Cross-Site Scripting (XSS)
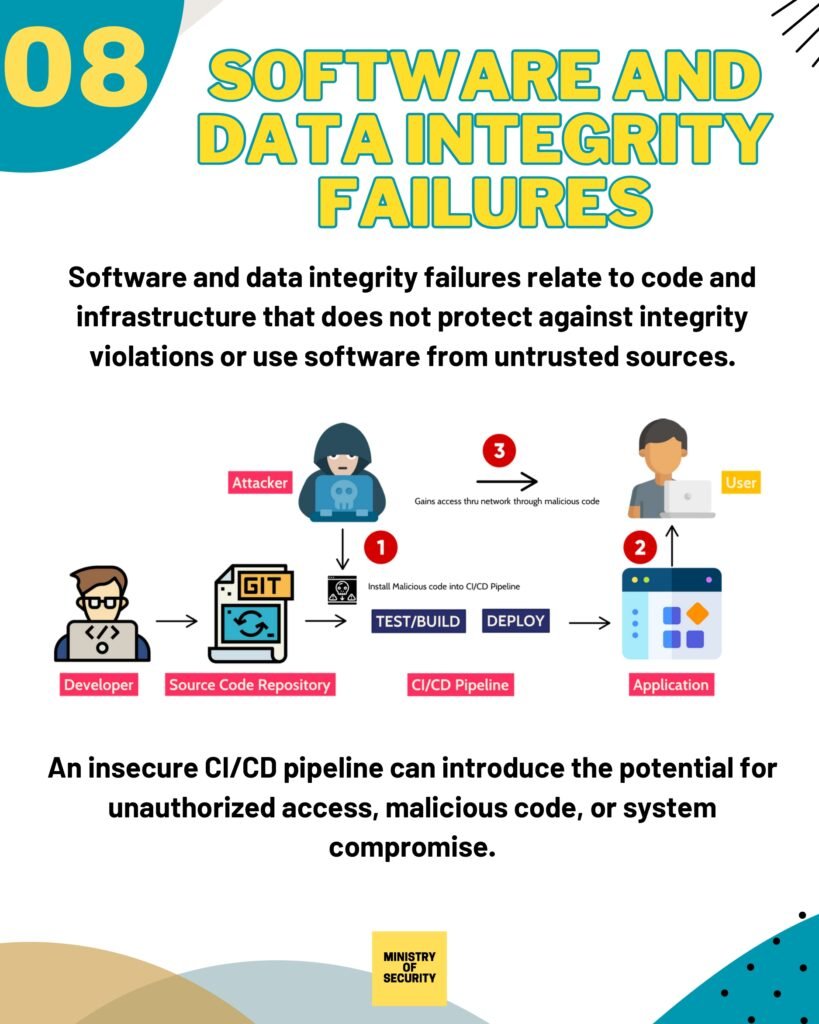
- Insecure Deserialization
- Using Components with Known Vulnerabilities
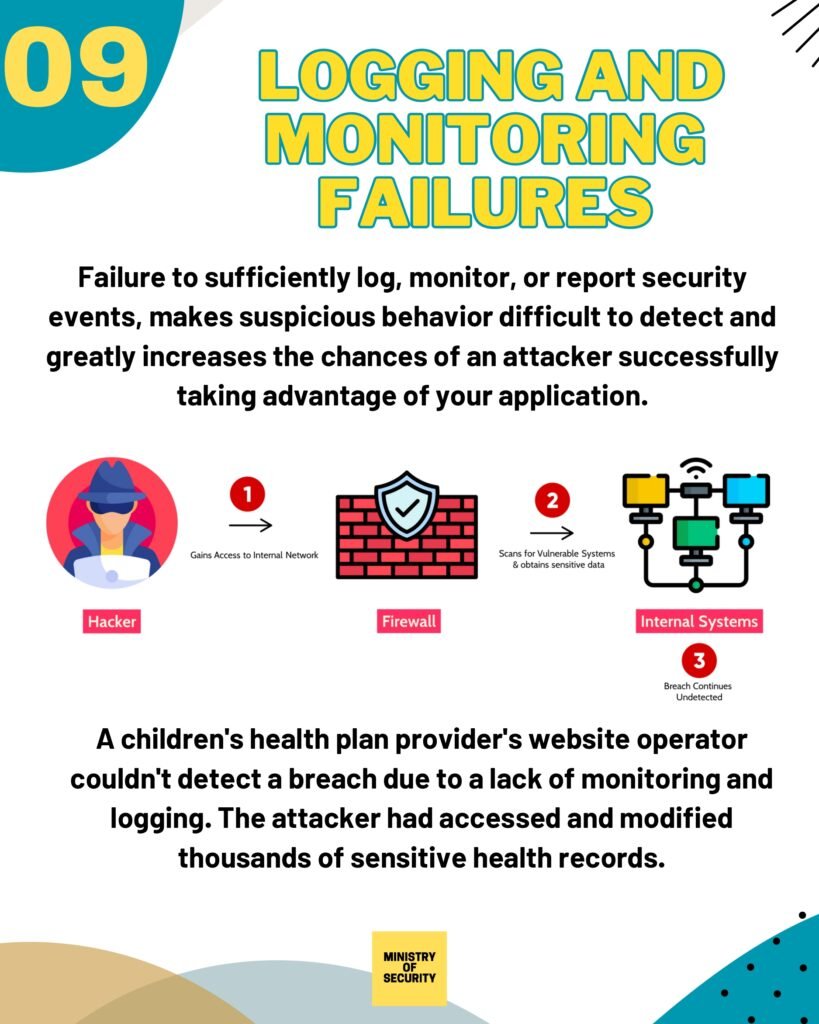
- Insufficient Logging and Monitoring
For each vulnerability, we provide a detailed explanation of how it works, the potential impact it can have on your web application, and practical steps to mitigate the risks. Our aim is to empower you with the knowledge and tools necessary to protect your applications from these common security pitfalls.
The guide covers a wide range of topics related to web application security, including:
- Common web application vulnerabilities and how to mitigate them
- Secure coding practices and frameworks
- Authentication and access control
- Data validation and input sanitization
- Secure session management
- Secure communication and encryption
- Security testing and vulnerability assessments
- Incident response and recovery
By following the recommendations and guidelines outlined in this guide, you can significantly enhance the security posture of your web applications and protect sensitive data from unauthorized access. Additionally, implementing robust security measures can help build trust and confidence among your users, leading to increased customer satisfaction and loyalty.
Download from Link
To access the full guide, simply click on the following link: Download Guide. This comprehensive guide will provide you with valuable insights and practical tips on web application security. Whether you are a developer, a security professional, or a business owner, understanding and implementing web application security best practices is crucial in today’s digital landscape.
Web application security refers to the measures taken to protect web applications from various threats, such as unauthorized access, data breaches, and malicious attacks. With the increasing reliance on web applications for various purposes, including e-commerce, online banking, and communication, it is essential to ensure that these applications are secure and resilient against potential vulnerabilities.