Penetration testing is a proactive approach to cybersecurity that involves simulating real-world attacks on a network or system to uncover any weaknesses or vulnerabilities. By conducting these tests, organizations can identify potential entry points that attackers could exploit and take appropriate measures to strengthen their defenses.
There are numerous penetration testing tools available in the market, each with its own unique features and capabilities. In this guide, we will explore the top 25 tools that are widely used by cybersecurity professionals and ethical hackers to perform comprehensive penetration tests.
Overview Of This Guide
These tools can be categorized into various types based on their functionality. Some tools are designed for network scanning and reconnaissance, while others focus on vulnerability assessment, exploitation, or post-exploitation activities. Regardless of their specific purpose, all these tools play a crucial role in helping organizations identify and mitigate potential security risks.
Throughout this guide, we will provide detailed information about each tool, including its key features, supported platforms, and use cases. We will also discuss the advantages and limitations of each tool, allowing you to make an informed decision when selecting the right tool for your penetration testing needs.
The Content of the Guide
The guide is divided into four main sections, each covering different aspects of penetration testing tools:
1. Introduction to Penetration Testing
This section provides an overview of penetration testing, its importance, and the different types of tests that can be conducted. It also highlights the benefits of using penetration testing tools and the key considerations to keep in mind.
2. Choosing the Right Penetration Testing Tools
In this section, we discuss the factors to consider when selecting the right penetration testing tools for your needs. We explore the different categories of tools available and provide insights on how to evaluate their features and capabilities. This includes considerations such as the type of testing you need to perform, the level of expertise required, and the compatibility of the tools with your existing systems and infrastructure. By understanding these factors, you can make an informed decision and choose the tools that best suit your requirements.
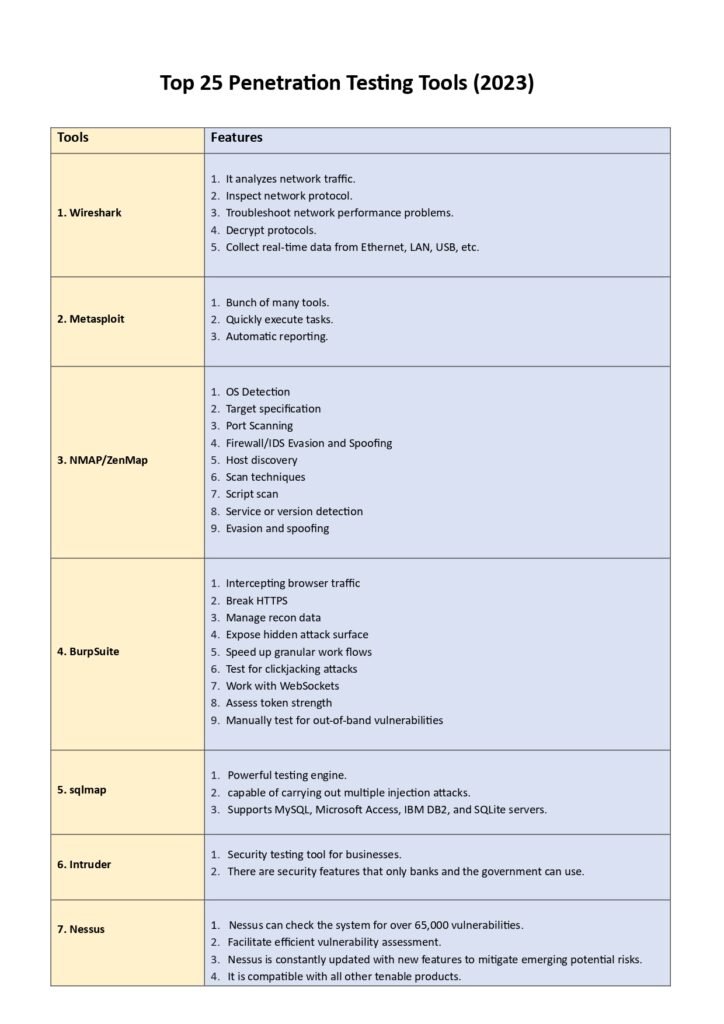
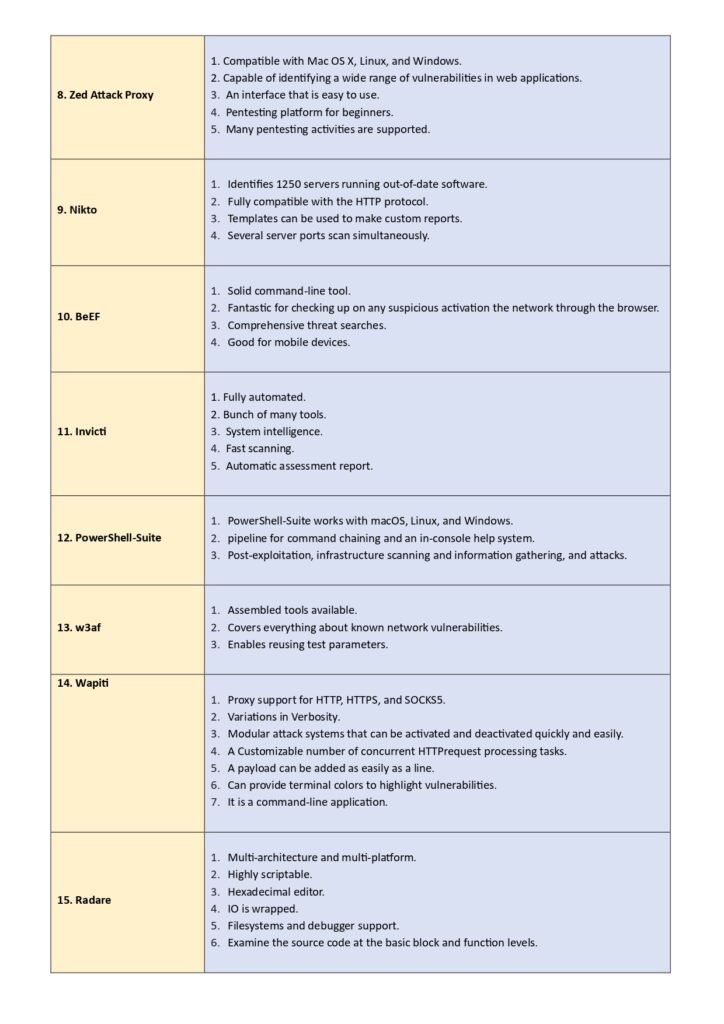
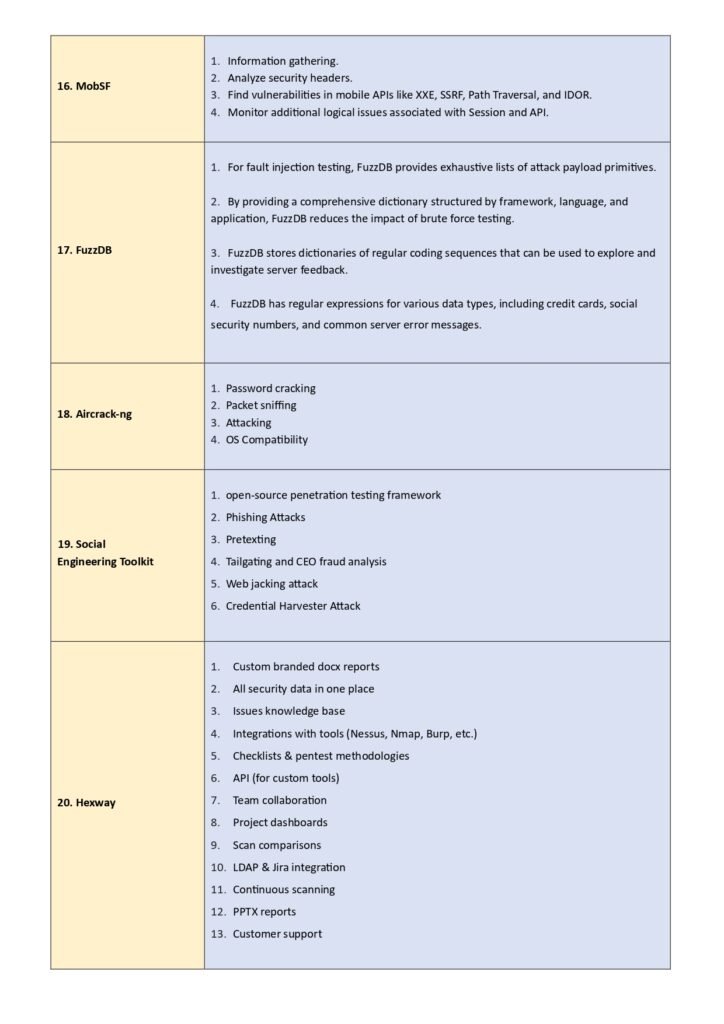
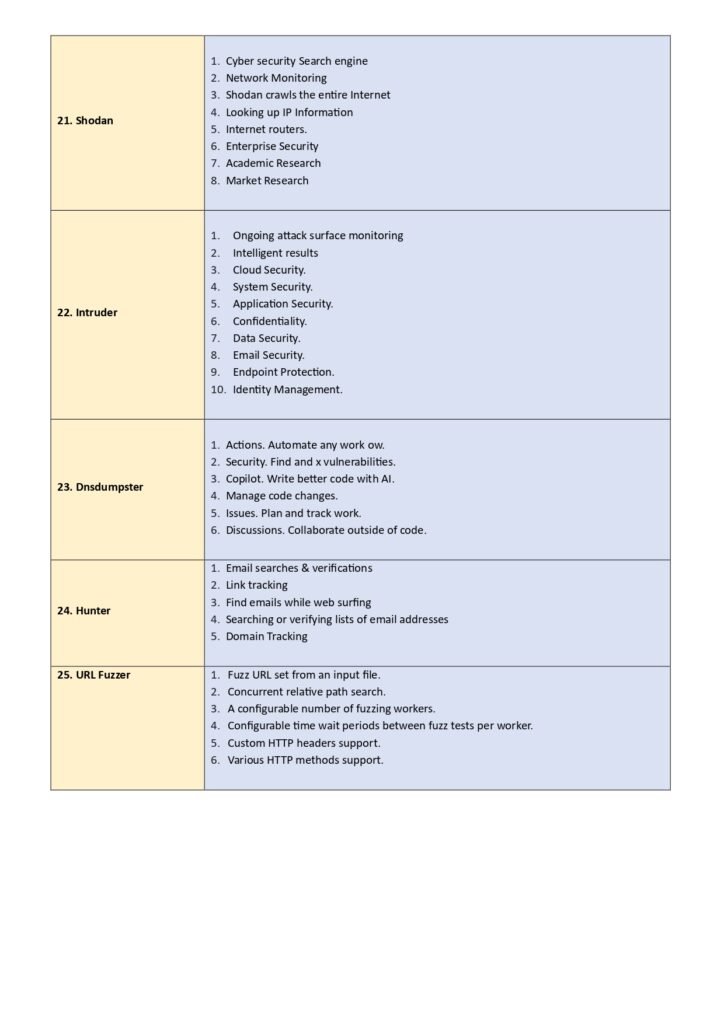
3. Top 25 Penetration Testing Tools
Here, we dive into the main content of the guide, where we present a detailed overview of the top 25 penetration testing tools. Each tool is accompanied by a brief description, key features, and use cases. We also highlight the pros and cons of each tool to help you make an informed decision. The tools included in this section are widely recognized and used by professionals in the field, making them a valuable resource for anyone looking to enhance their penetration testing capabilities. Whether you are a beginner or an experienced practitioner, this section will provide you with a comprehensive list of tools to consider.
4. Best Practices and Tips for Effective Penetration Testing
In the final section of the guide, we share best practices and tips to ensure the success of your penetration testing efforts. We cover topics such as planning and scoping, conducting tests, analyzing results, and reporting findings. These insights will help you maximize the value of your penetration testing activities. Additionally, we provide guidance on how to establish a robust testing methodology, ensuring that your tests are thorough and comprehensive. By following these best practices, you can improve the effectiveness of your penetration testing and enhance the security of your systems.
Download from Link
To access the full guide and explore the top 25 penetration testing tools, please click here to download the PDF.
Once you have downloaded the PDF, you will have access to a comprehensive guide that will walk you through the world of penetration testing. This guide is designed to provide you with a deep understanding of the tools and techniques used in this field, allowing you to enhance your cybersecurity skills and stay one step ahead of potential threats.

















