Introduction
In the digital age, managing cybersecurity for control systems is a critical task. With increasing cyber threats targeting industrial control systems, it’s essential to have a robust strategy in place.
Our latest document, titled “Managing Cybersecurity for the Industrial Control System,” provides comprehensive guidelines and strategies to safeguard these vital systems.
Overview of the Document
This document serves as a practical guide for professionals responsible for cybersecurity in industrial environments. From understanding the basics to implementing advanced security protocols, it covers all crucial aspects.









The Content
The document is structured to offer clear, actionable advice. Key sections include risk assessment, incident response, and best practices for maintaining cybersecurity. Each section is meticulously researched to ensure relevance and effectiveness.
Table of Contents
- Context and issues surrounding industrial control system cybersecurity
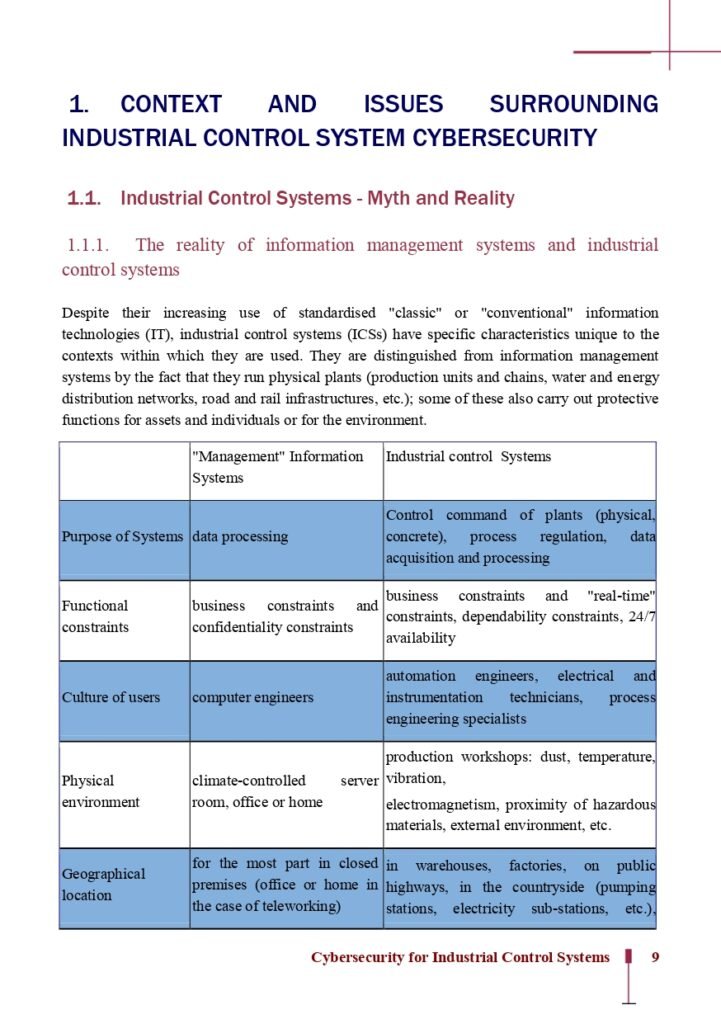
1.1. Industrial Control Systems – Myth and Reality
1.1.1. The reality of information management systems and industrial control systems
1.1.2. Some myths about industrial control systems
1.2. Issues surrounding ICS cybersecurity
1.2.1. General information about attacks
1.2.2. Human negligence
1.2.3. Vulnerabilities of Industrial Control Systems
1.2.4. Potential impacts on ICSs - Deployment Method of cybersecurity
2.1. Reminder of cybersecurity role
2.2. Key Principles of cybersecurity
2.2.1. Awareness-raising among personnel
2.2.2. Assets management and risk analysis
2.2.3. Prevention: the concept of Defence-In-Depth
2.2.4. Monitoring and detection of incidents
2.2.5. Incident handling, alert chain
2.2.6. Monitoring of threats and vulnerabilities
2.2.7. Disaster Recovery Plan and Business Continuity Plans (DRP/BCP) 20
2.3. A system-wide, structured approach
2.3.1. Willingness at every level
2.3.2. Taking account of cybersecurity in projects
2.3.3. Taking account of cybersecurity in FMECA / HAZOP
2.3.4. Taking account of cybersecurity in maintenance
2.3.5. Taking account of cybersecurity in procurement
Appendix A: Frequently encountered vulnerabilities
Appendix B: Good practices
Appendix C: Abbreviations and Acronyms
Appendix D: Bibliographical References
Why the Document
With cyber-attacks becoming more sophisticated, having access to expert advice is invaluable. This document not only explains the concepts but also provides real-world examples to illustrate the points. It’s a must-read for anyone involved in managing cybersecurity for industrial control systems.
Conclusion
Managing cybersecurity for control systems requires continuous effort and up-to-date knowledge. This document equips you with the latest information and tools needed to protect your industrial environment from cyber threats.
Download PDF
To gain a deeper understanding and implement effective cybersecurity measures for your control systems, download the full document today. Click here to download the PDF.

















