In this guide, we will delve into the world of dynamic malware analysis, exploring the techniques and tools used to analyze and understand malicious software. Malware, short for malicious software, is a term used to describe any software designed to harm or exploit computer systems. It can take various forms, such as viruses, worms, Trojans, ransomware, and spyware.
The field of malware analysis plays a crucial role in the cybersecurity industry. By studying malware, analysts can gain insights into the tactics, techniques, and procedures (TTPs) employed by cybercriminals. This knowledge is then used to develop effective defense mechanisms and protect computer systems from future attacks.
Overview of the Guide
Dynamic malware analysis is one of the fundamental approaches used in analyzing malicious software. Unlike static analysis, which focuses on examining the code and structure of malware without executing it, dynamic analysis involves running malware in a controlled environment to observe its behavior and gather information about its capabilities.

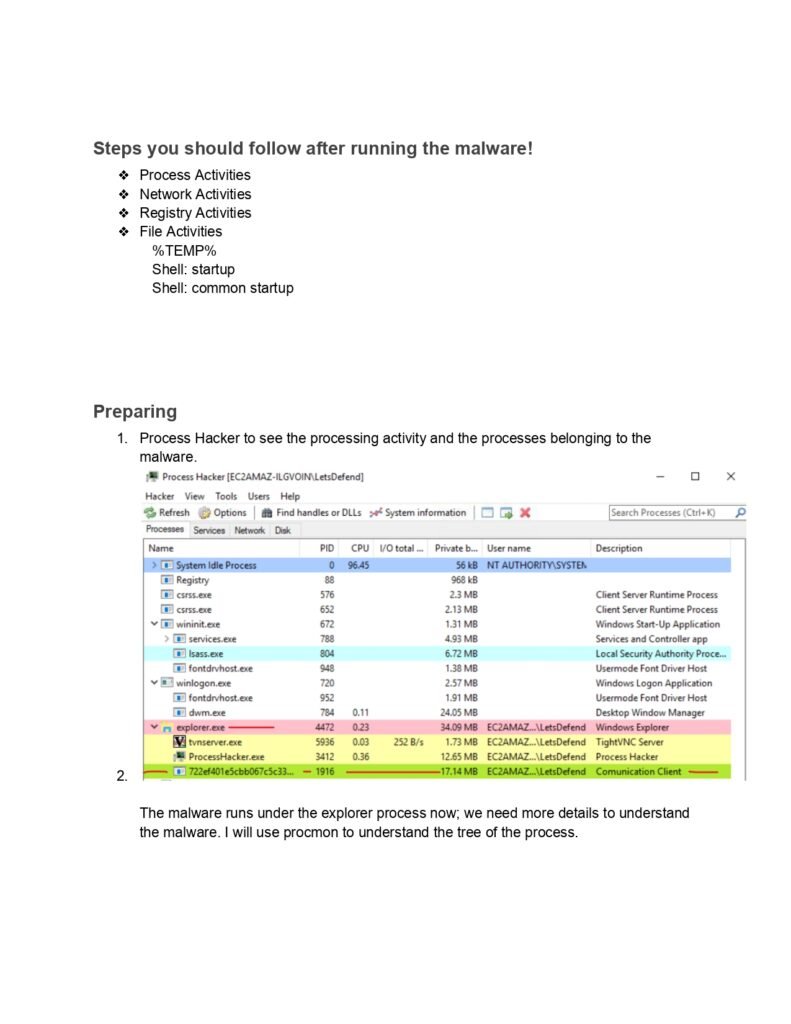
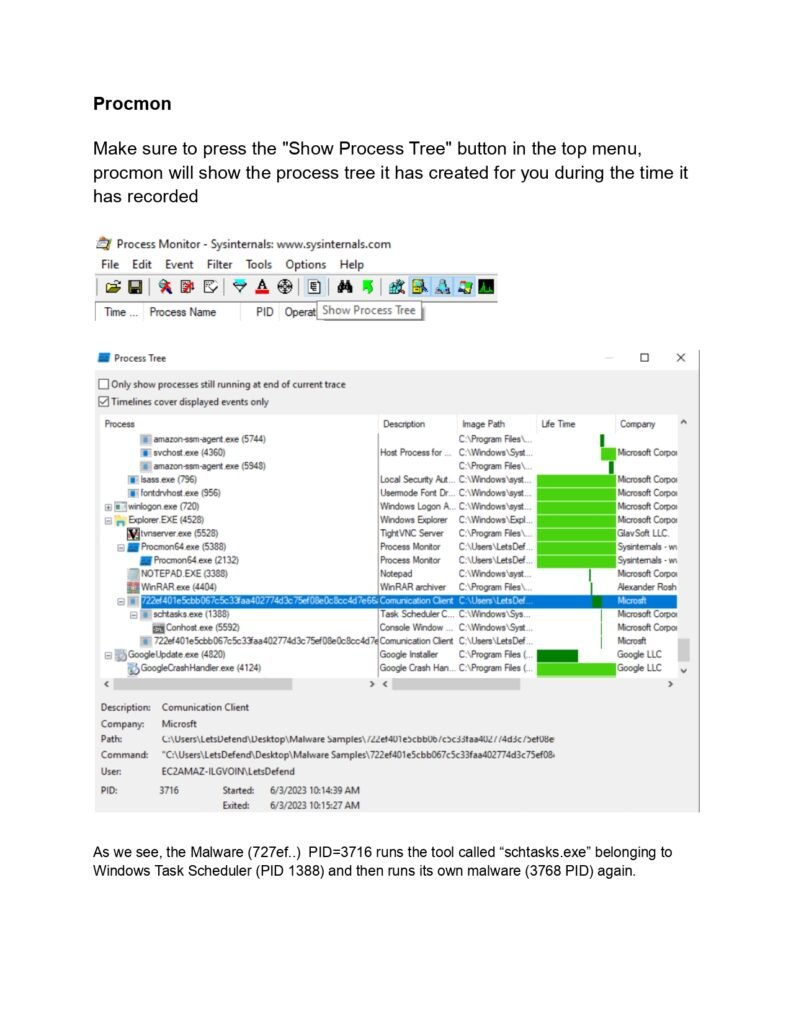
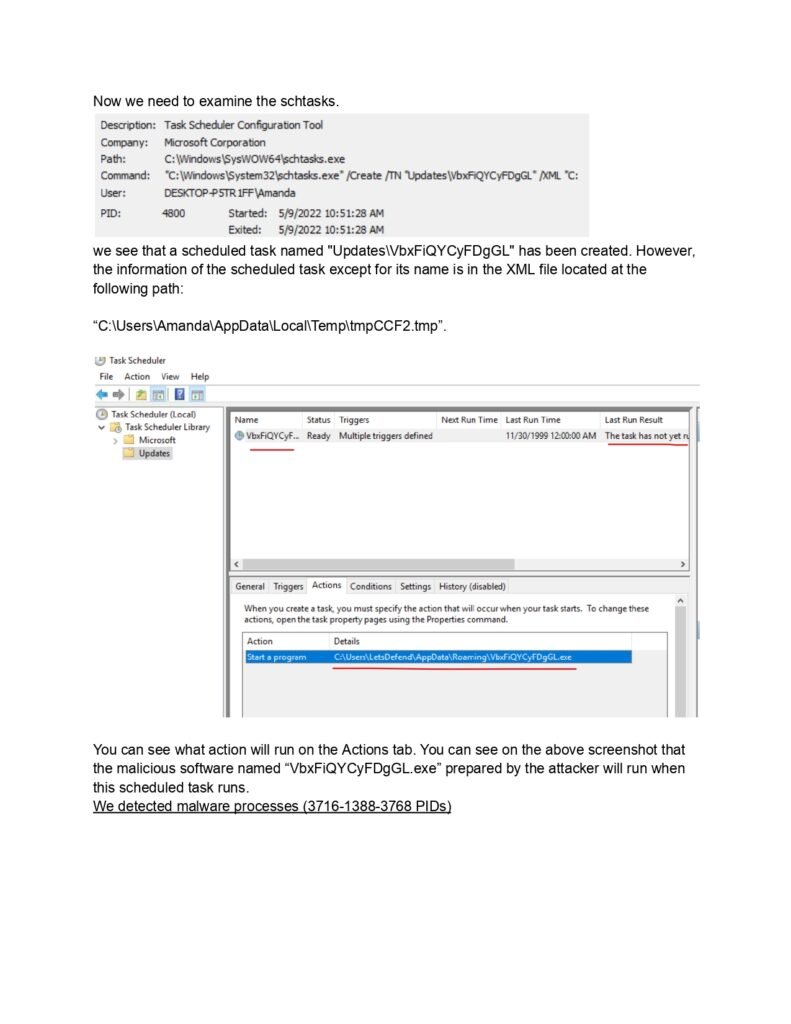
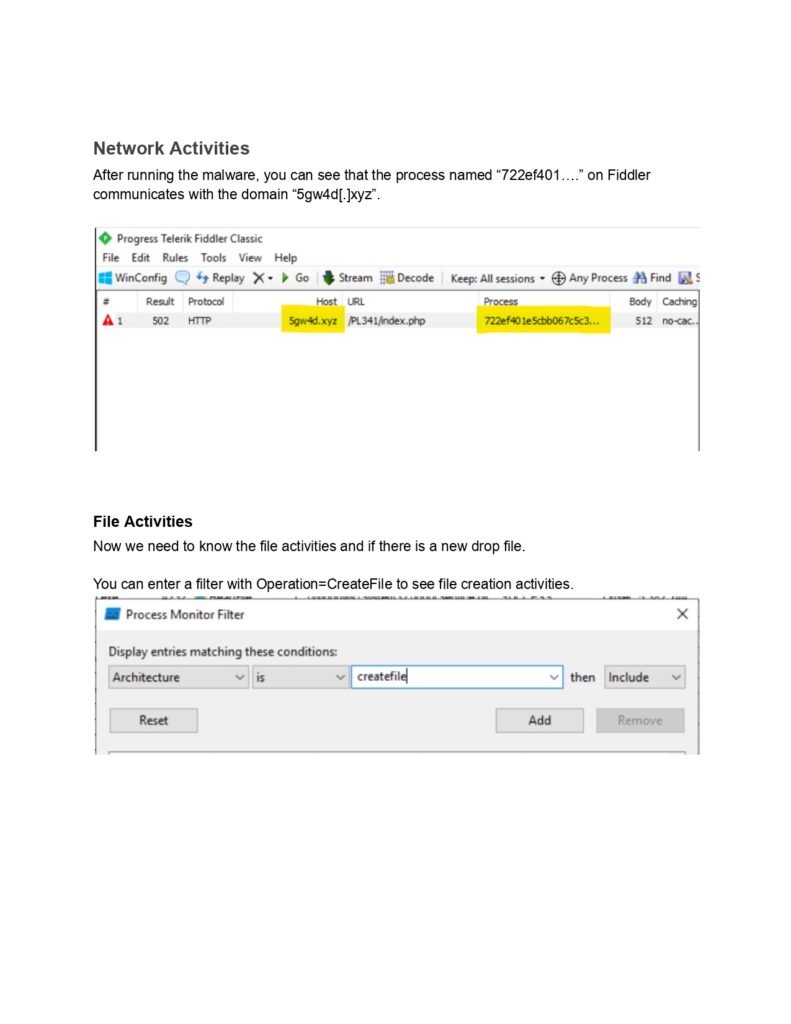

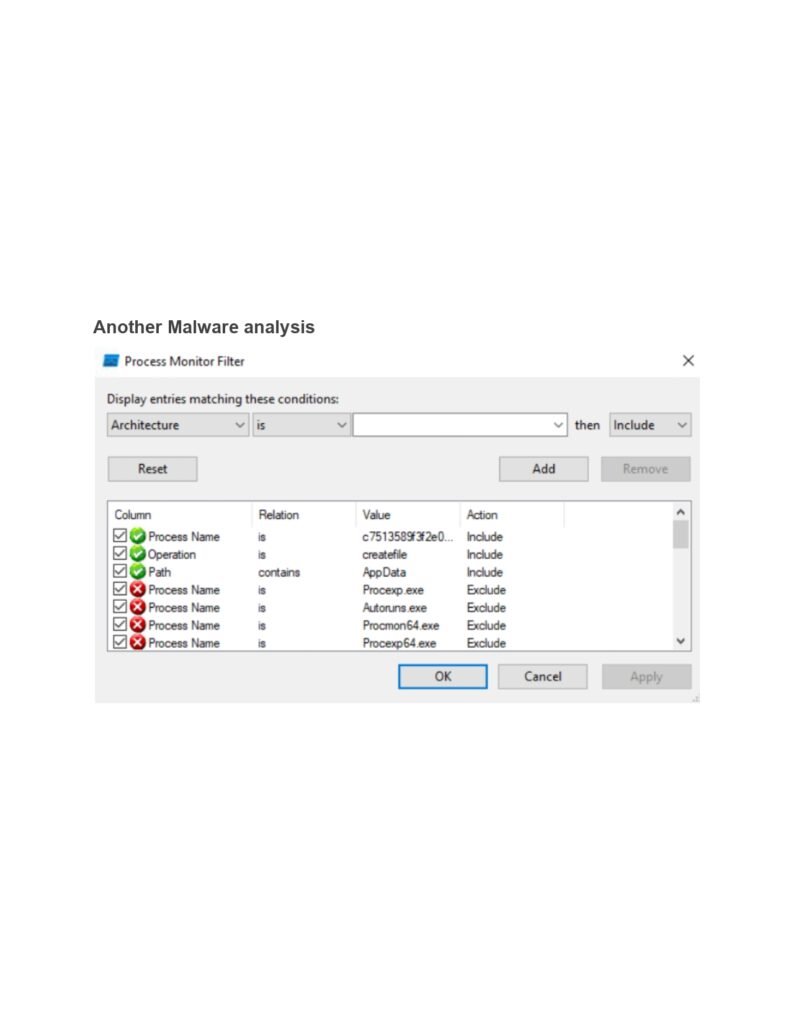


Throughout this guide, we will cover a wide range of topics related to dynamic malware analysis. We will start by exploring the different types of malware and their characteristics. Understanding the various forms of malware is crucial for effective analysis, as different malware types may exhibit unique behaviors and require specific analysis techniques.
The Content of the Guide
Our guide is divided into several sections, each focusing on a specific aspect of dynamic malware analysis. Here is a brief overview of what you can expect:
1. Understanding Malware
In this section, we will start by providing a solid foundation on malware, its types, and how it can affect your systems. It is essential to have a good understanding of malware before diving into the analysis process.
2. Setting Up a Safe Environment
Before you can analyze malware, you need to create a controlled environment that isolates the malware from your production systems. We will guide you through the process of setting up a safe environment using virtual machines or sandboxing tools.
3. Collecting Malware Samples
Having access to real-world malware samples is crucial for effective analysis. We will discuss various sources for obtaining malware samples and best practices for handling and storing them securely.
4. Executing Malware
This section will cover the techniques and tools used to execute malware samples in a controlled environment. We will explore different approaches, such as using virtual machines, emulators, or sandboxing tools, to observe the behavior of malware without compromising your systems.
5. Monitoring and Analyzing Behavior
Once the malware is executed, it is essential to monitor its behavior and analyze the actions it performs. We will introduce you to various tools and techniques for monitoring network traffic, system calls, and file system changes to gain insights into the malware’s capabilities.
6. Extracting Indicators of Compromise
Identifying the indicators of compromise (IOCs) is crucial for detecting and mitigating the impact of malware. We will show you how to extract IOCs from the analysis results and use them to enhance your security defenses.
7. Reporting and Documentation
After analyzing malware, it is important to document your findings and share them with relevant stakeholders. We will guide you on how to create comprehensive reports that capture the key details of the analysis process and provide actionable insights.
Throughout the guide, we will provide step-by-step instructions, real-world examples, and practical tips to help you become proficient in dynamic malware analysis. Whether you are a beginner or an experienced cybersecurity professional, this guide will equip you with the knowledge and skills needed to effectively analyze and mitigate the impact of malware on your systems.
Key Topics
Throughout the guide, we will cover a wide range of topics related to dynamic malware analysis. Some of the key areas we will explore include:
- Malware types and their characteristics: We will delve into different types of malware such as viruses, worms, trojans, ransomware, and spyware. Understanding their characteristics will help analysts identify and analyze them effectively.
- Virtual machine and sandboxing technologies: Virtual machines and sandboxes provide controlled environments for analyzing malware. We will discuss various virtualization techniques and sandboxing tools that can be used to execute malware safely.
- Behavioral analysis techniques: This section will cover techniques for observing and analyzing the behavior of malware. We will explore methods such as dynamic analysis, runtime monitoring, and code instrumentation to gain insights into the actions performed by malware.
- Network traffic analysis: Analyzing the network traffic generated by malware can provide valuable information about its communication with command and control servers, data exfiltration, and other malicious activities. We will discuss tools and techniques for capturing and analyzing network traffic.
- System call monitoring: Monitoring system calls made by malware during execution can help identify its interactions with the operating system and detect any suspicious or malicious behavior. We will explore techniques for monitoring and analyzing system calls.
- File system analysis: Malware often interacts with the file system to perform various activities such as dropping files, modifying existing files, or encrypting data. We will cover techniques for analyzing file system changes caused by malware.
- Indicators of compromise (IOCs): IOCs are artifacts or patterns that indicate the presence of malware. We will discuss different types of IOCs, including file-based IOCs, network-based IOCs, and behavioral IOCs, and how to use them in malware analysis.
- Reporting and documentation best practices: Effective reporting and documentation are essential for sharing findings and collaborating with other analysts. We will provide guidelines and best practices for documenting the analysis process and presenting the results in a clear and concise manner.
Each page of the guide is designed to provide you with valuable insights and practical knowledge. The first page introduces you to the fundamentals of dynamic malware analysis, explaining the importance of this technique in today’s ever-evolving threat landscape. It delves into the different types of malware and the potential risks they pose to individuals and organizations.
Download from Link
To access the full guide on dynamic malware analysis in PDF format, please click on the following link: [From here].
We hope you find this guide informative and valuable in your journey to combat malware effectively.