As the digital landscape continues to expand, so does the complexity and sophistication of cyber threats. Organizations of all sizes and industries are facing an increasing number of cyber attacks, ranging from data breaches to ransomware and beyond. In order to effectively protect their assets and mitigate risks, businesses need to stay ahead of these threats by adopting a proactive approach to cybersecurity.
Threat intelligence plays a crucial role in this proactive approach. It involves gathering, analyzing, and interpreting information about potential threats and their actors, allowing organizations to anticipate and respond to cyber attacks more effectively. By understanding the motivations, tactics, and techniques of threat actors, businesses can make informed decisions about their security measures and allocate resources more efficiently.
Overview Of This Guide
The guide begins by explaining the fundamental concepts of threat intelligence, including what it is and why it is crucial in today’s digital landscape. It goes on to highlight the benefits of adopting a proactive approach to cybersecurity, such as the ability to detect and mitigate potential threats before they can cause significant damage.
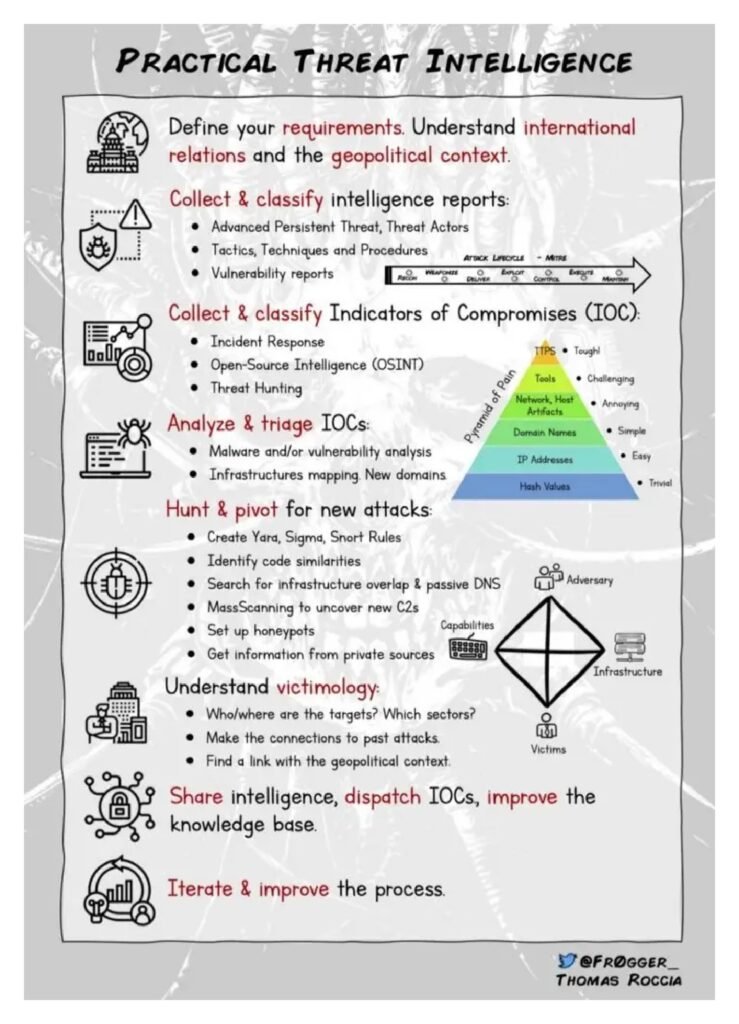
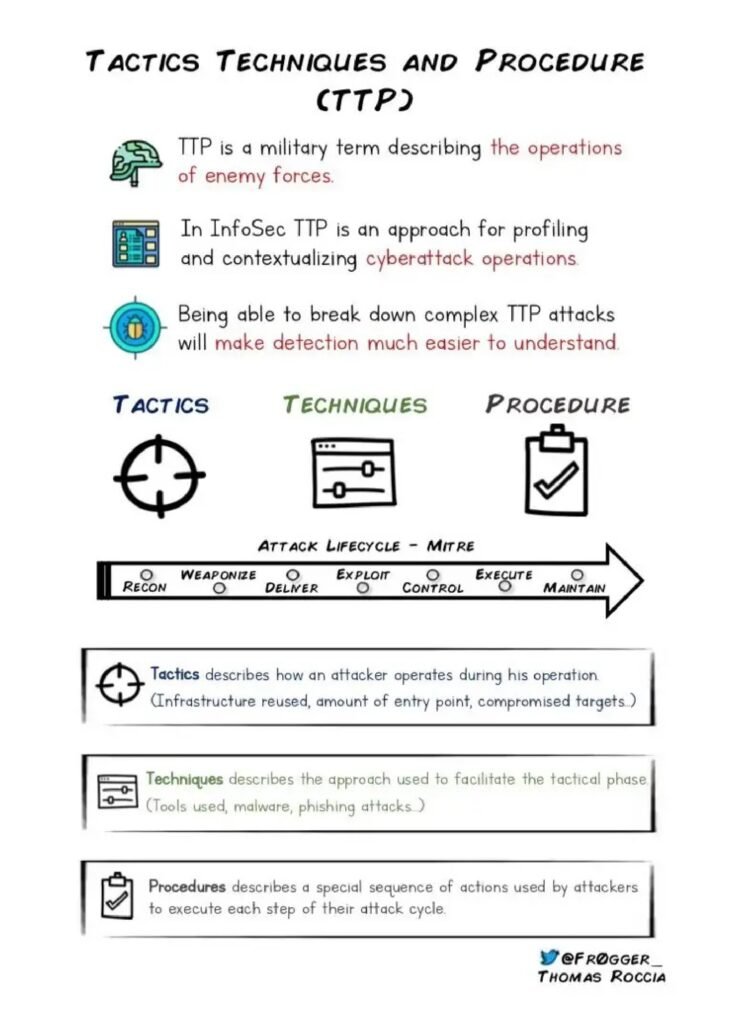
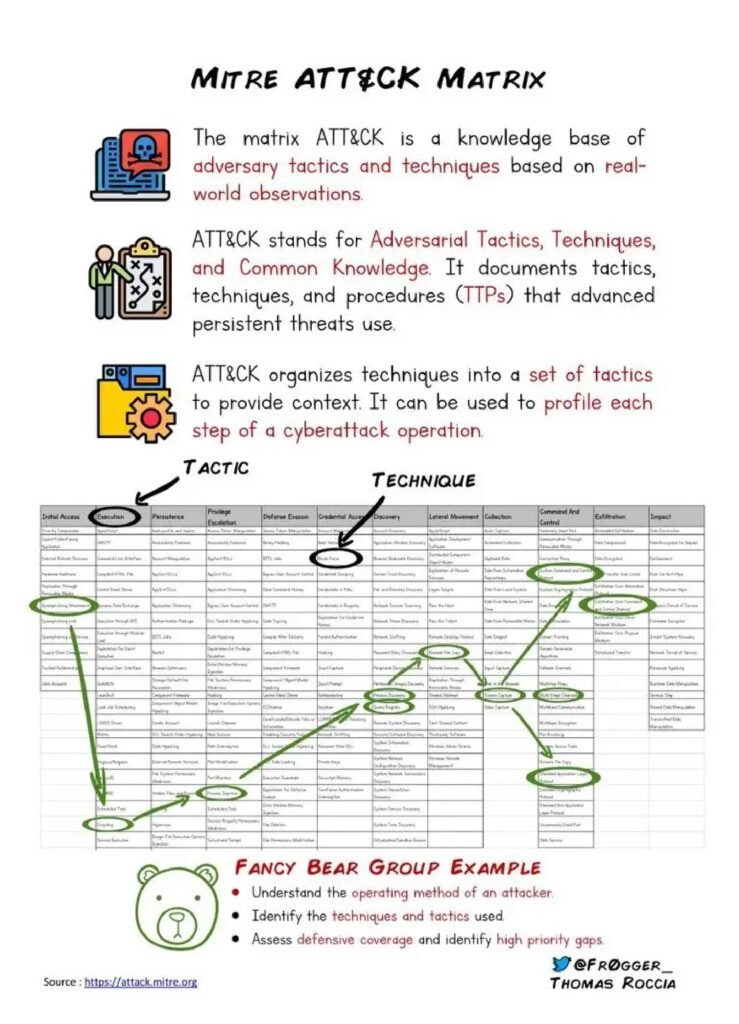
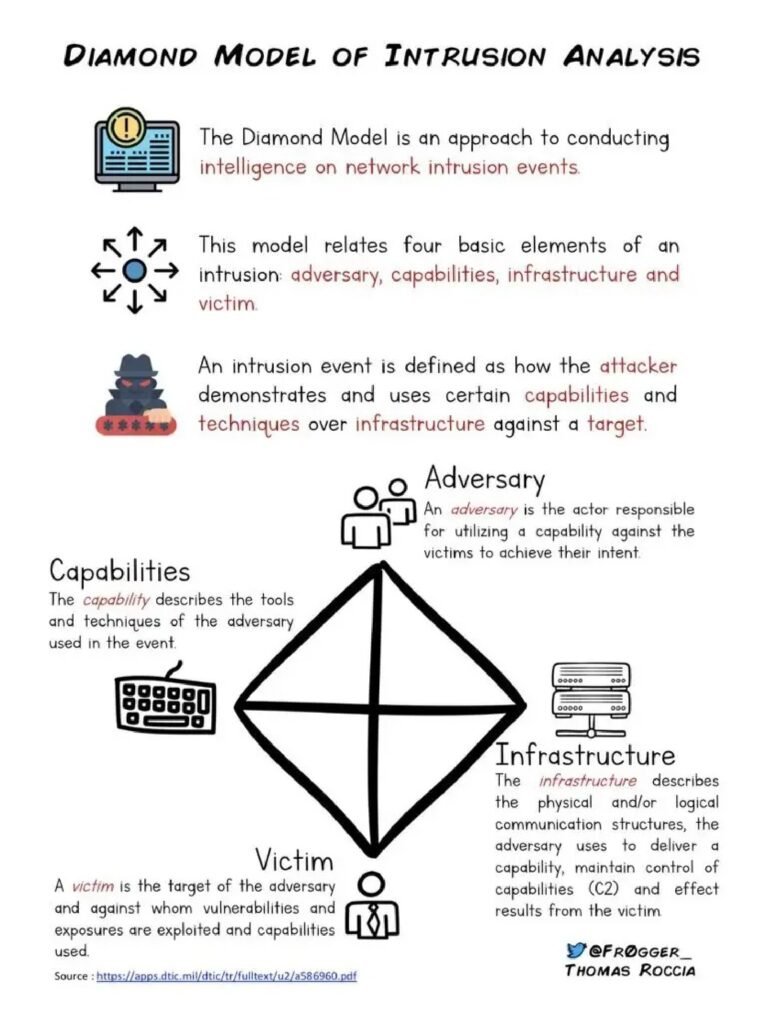
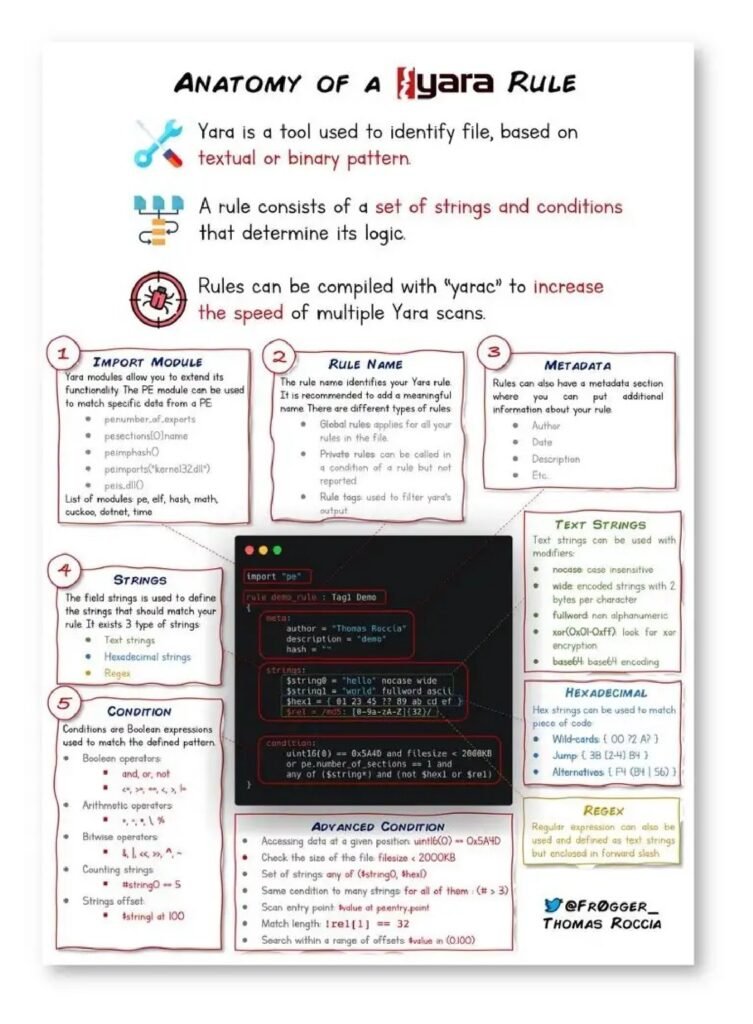
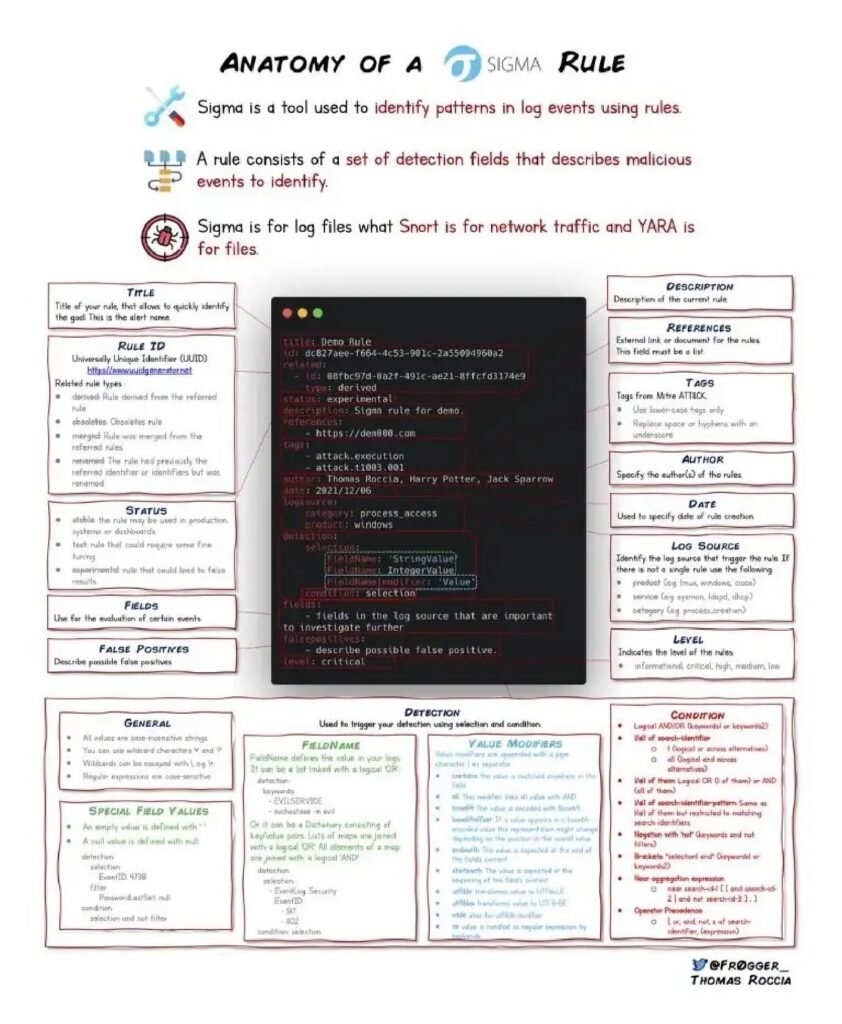
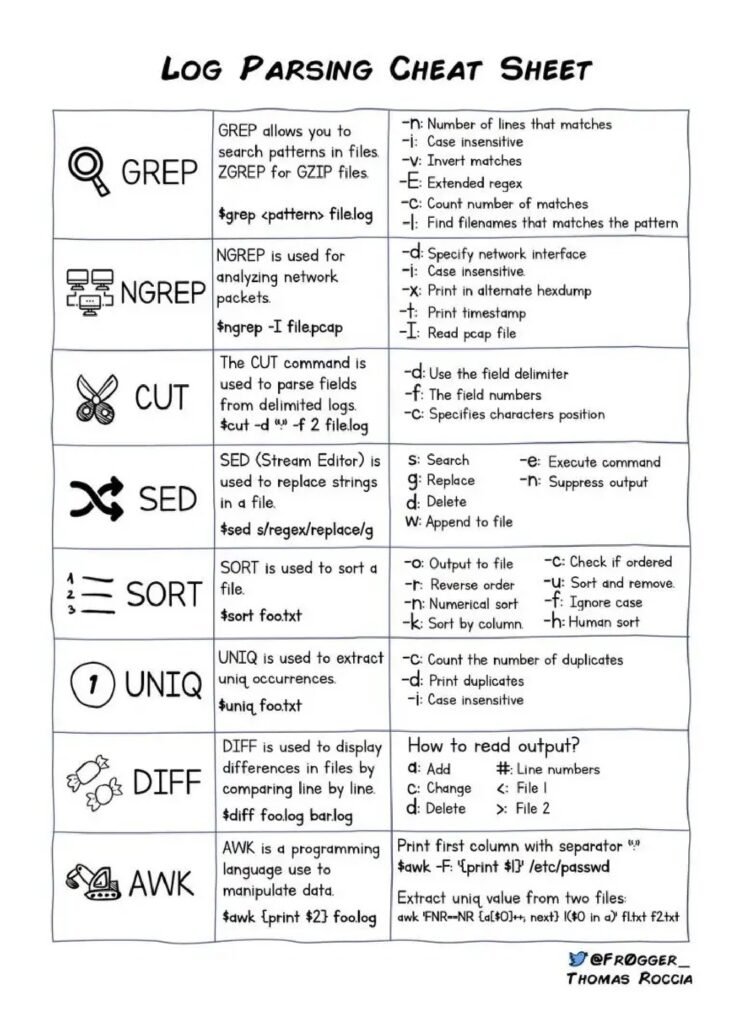

However, threat intelligence is not just limited to large enterprises or government agencies. Small and medium-sized businesses can also benefit from incorporating threat intelligence into their cybersecurity strategy. In fact, these organizations are often targeted by cybercriminals due to their perceived vulnerabilities and lack of robust security measures.
Threat Intelligence Automation
In this section, we dive into the world of threat intelligence automation. We discuss the advantages of automating certain aspects of threat intelligence, such as data collection, analysis, and dissemination. We explore the different tools and technologies available for automating threat intelligence processes and provide practical tips for implementing automation effectively.
Threat Intelligence in Incident Response
Here, we explore the role of threat intelligence in incident response. We discuss how threat intelligence can enhance incident detection, response, and recovery efforts. We provide guidance on integrating threat intelligence into incident response workflows and highlight best practices for leveraging threat intelligence during a security incident.
Threat Intelligence for Risk Management
In this section, we examine the relationship between threat intelligence and risk management. We discuss how threat intelligence can help organizations identify and prioritize potential risks, as well as inform risk mitigation strategies. We provide practical examples of how threat intelligence can be used to enhance risk management processes and improve overall security posture.
Emerging Trends in Threat Intelligence
Here, we take a look at the latest trends and developments in the field of threat intelligence. We explore emerging technologies, techniques, and methodologies that are shaping the future of threat intelligence. We discuss the potential impact of these trends on organizations and offer insights into how to stay ahead of the curve.
Conclusion
In the final section of our guide, we wrap up the key takeaways and provide a summary of the main points covered throughout the guide. We offer final thoughts on the importance of threat intelligence in today’s cybersecurity landscape and provide additional resources for further exploration.
By the end of this guide, you will have a comprehensive understanding of threat intelligence and its practical applications. You will be equipped with the knowledge and tools necessary to implement and leverage threat intelligence effectively within your organization, enhancing your overall security posture and resilience against cyber threats.
Key Topics
Throughout the guide, we cover several key topics that are crucial for a comprehensive understanding of practical threat intelligence. Some of these topics include:
- Common threat intelligence terminology
- Threat intelligence lifecycle
- Open-source intelligence (OSINT)
- Vulnerability management
- Incident response and threat hunting
- Machine learning and artificial intelligence in threat intelligence
- Dark web monitoring and analysis
- Threat intelligence sharing and collaboration
- Threat intelligence platforms and tools
- Threat intelligence in cloud environments
- Threat intelligence for critical infrastructure protection
- Threat intelligence for financial institutions
- Threat intelligence for government agencies
- Threat intelligence for healthcare organizations
- Threat intelligence for e-commerce businesses
- Threat intelligence for educational institutions
- Threat intelligence for small and medium-sized enterprises (SMEs)
- Threat intelligence for the energy sector
- Threat intelligence for the transportation industry
- Threat intelligence for the telecommunications sector
- Threat intelligence for the retail industry
- Threat intelligence for the manufacturing sector
Each of these topics provides valuable insights into different aspects of threat intelligence and how it can be applied in various industries and environments. By exploring these topics in detail, readers will gain a comprehensive understanding of the practical applications of threat intelligence and its potential impact on cybersecurity.
Download from Link
To access our practical threat intelligence guide, simply click on the following link: Download the Practical Threat Intelligence Guide.
We recommend saving the guide on your device for easy access and reference.

















