As a SOC analyst, it is crucial to have a deep understanding of network communication and the ports involved. Ports serve as endpoints in a network connection, allowing different applications and services to communicate with each other. Each port is assigned a unique number, known as a port number, which helps in identifying the specific service or application running on a device.
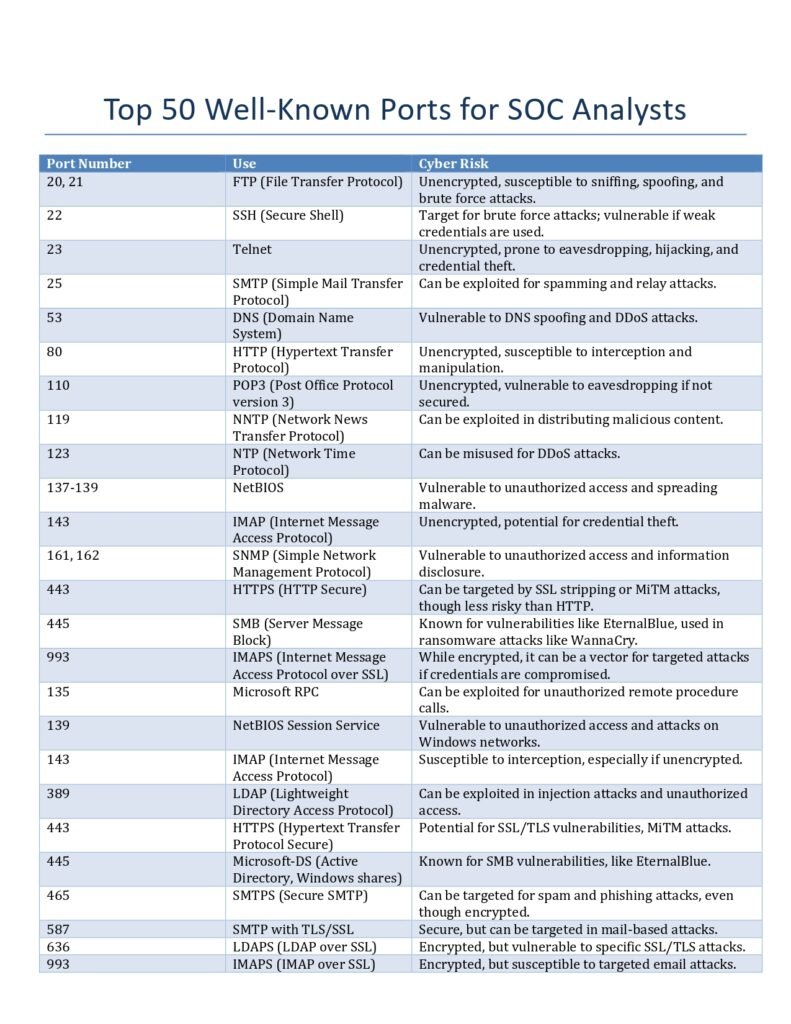
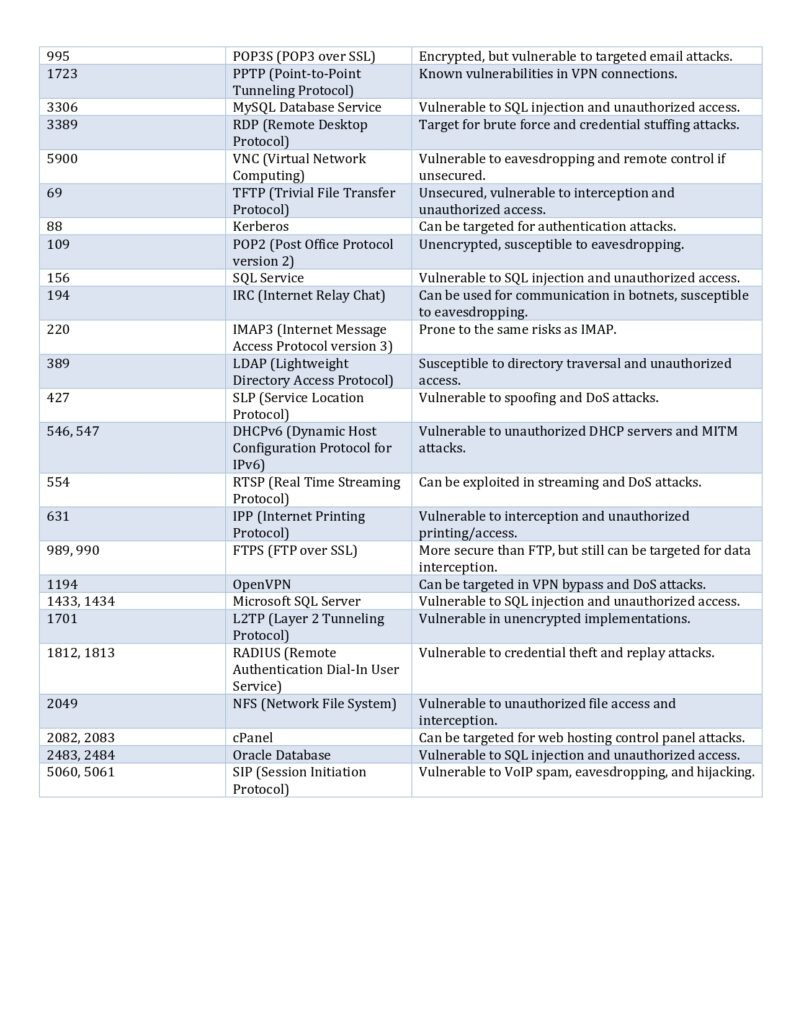
Our comprehensive guide aims to provide you with detailed information about the top 50 well-known ports that every SOC analyst should be familiar with. We have carefully curated this list based on the significance and frequency of these ports being used in network communication.
Overview Of This Notes
By familiarizing yourself with these ports, you will be able to identify and analyze network traffic effectively. This knowledge will enable you to detect potential security threats, such as unauthorized access attempts, malware infections, or data exfiltration.
Understanding the Importance of Port Analysis
In today’s digital landscape, where cyber threats are becoming increasingly sophisticated, it is crucial for SOC analysts to have a deep understanding of network traffic analysis. Port analysis plays a pivotal role in this process, as it allows analysts to gain insights into the activities occurring within a network.
Ports are virtual communication endpoints that enable data to flow between devices. Each port is associated with a specific protocol or service, and understanding the purpose of these ports is essential for effective network monitoring and threat detection.
For example, port 80 is commonly used for HTTP traffic, which is the protocol used for web browsing. By monitoring this port, SOC analysts can identify any suspicious or malicious activities related to web traffic. Similarly, port 22 is used for SSH (Secure Shell) traffic, which is often targeted by hackers attempting to gain unauthorized access to systems.
Conclusion
In conclusion, the “Top 50 Well-Known Ports for SOC Analysts PDF” guide is a comprehensive resource that equips SOC analysts with the knowledge and tools they need to effectively monitor and secure their network. With its informative content, practical examples, and analysis, this guide serves as a valuable reference for both aspiring and experienced SOC analysts.
The “Top 50 Well-Known Ports for SOC Analysts PDF” guide provides a comprehensive list of the most commonly used ports and their associated protocols. It offers detailed explanations of each port’s purpose, potential vulnerabilities, and recommended mitigation techniques. This guide is a valuable resource for both aspiring and experienced SOC analysts who want to deepen their understanding of network protocols and strengthen their ability to detect and prevent cyber threats.
Download from Link
To access the “Top 50 Well-Known Ports for SOC Analysts PDF” guide, simply click on the following link: [From here].
We recommend saving the guide to your device for easy access whenever you need to refer to it.
Thank you for visiting our website and we hope you find our guide on well-known ports for SOC analysts informative and valuable. Stay tuned for more insightful resources and guides to enhance your knowledge and skills in the field of cybersecurity.
Understanding well-known ports is crucial for SOC analysts as they play a vital role in network communication. These ports are standardized and assigned specific numbers to ensure efficient and secure data transmission. By familiarizing themselves with these well-known ports, SOC analysts can effectively monitor network traffic, identify potential threats, and respond promptly to security incidents.

















