In the face of ever-evolving cyber threats, organizations must be prepared to effectively respond to security incidents. Cybersecurity incident response is a systematic approach that enables organizations to detect, analyze, contain, and recover from security breaches.
In this Lesson, we will explore the importance of incident response and delve into Lesson 14 of Cyber Security, which focuses on this critical aspect of cybersecurity. Additionally, we will introduce the accompanying PDF resource that provides valuable insights and practical guidance for establishing a robust incident response capability.

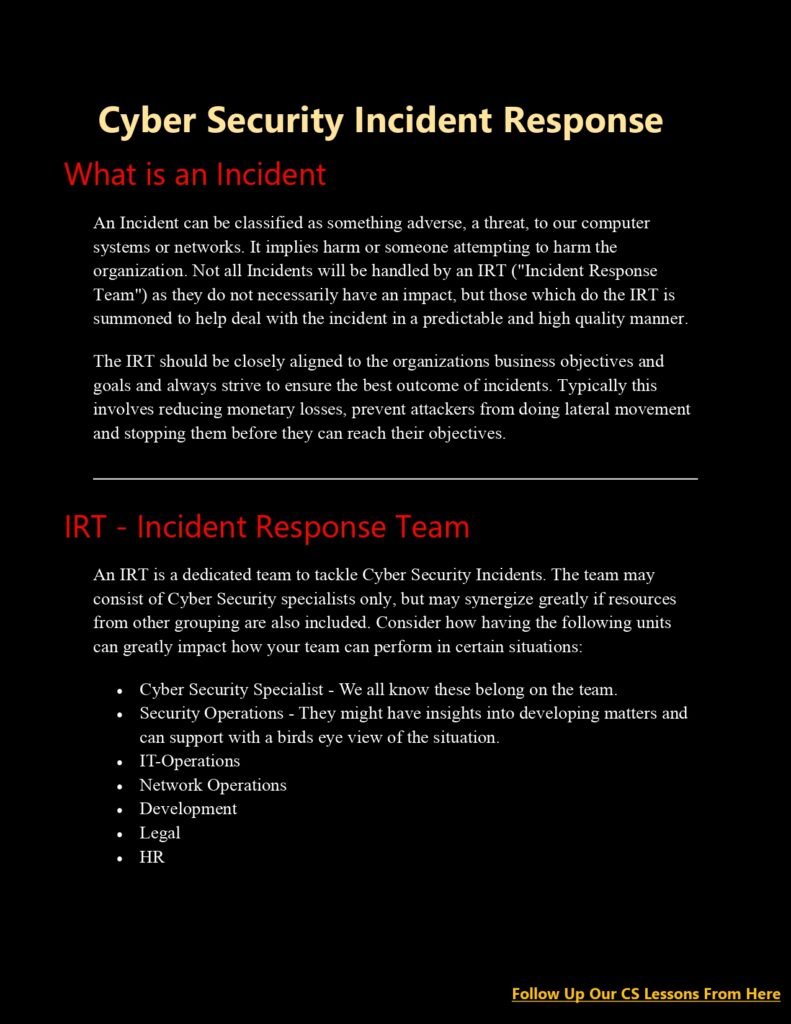



The Significance of Incident Response:
ncident response is a crucial component of an organization’s cybersecurity strategy. It allows organizations to minimize the impact of security incidents, mitigate further damage, and restore normal operations efficiently. Effective incident response helps organizations:
- Rapidly Identify and Analyze Incidents: A well-defined incident response process enables organizations to promptly detect and analyze security incidents, allowing for immediate action to mitigate the impact and prevent further compromise.
- Minimize Downtime and Financial Loss: By containing and recovering from security incidents swiftly, organizations can reduce downtime, financial loss, and reputational damage caused by prolonged disruption to business operations.
- Preserve Evidence: Incident response processes ensure that crucial evidence is collected and preserved for forensic analysis and potential legal proceedings, aiding in the identification of threat actors and the prevention of future incidents.
- Enhance Cybersecurity Posture: Learning from security incidents helps organizations identify weaknesses in their defenses and implement proactive measures to strengthen their overall cybersecurity posture.
CS Lesson 14: Establishing Effective Incident Response:
Lesson 14 of the Cyber Security curriculum focuses on establishing effective incident response capabilities. This lesson covers the following key aspects:
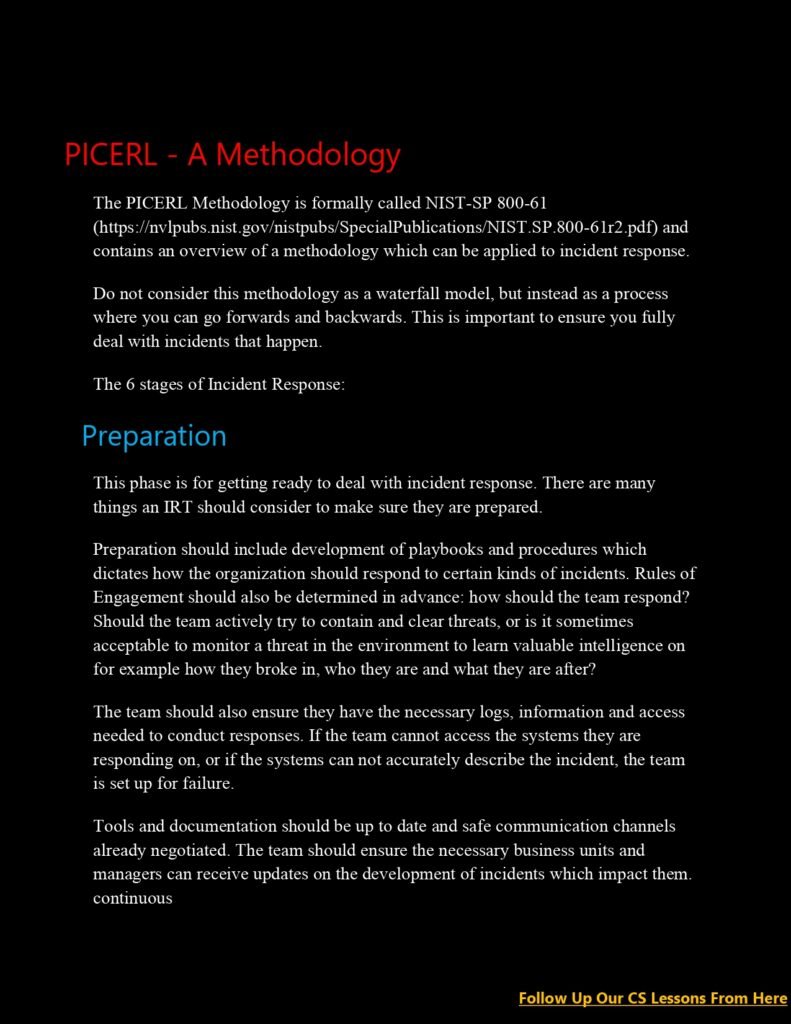
- Incident Response Lifecycle: Lesson 14 introduces the incident response lifecycle, which consists of six phases: preparation, identification, containment, eradication, recovery, and lessons learned. Each phase is explained in detail, highlighting the importance of well-defined processes and procedures.
- Incident Response Team: The lesson emphasizes the significance of establishing a dedicated incident response team responsible for coordinating and executing incident response activities. It discusses the roles and responsibilities of team members, as well as the importance of cross-functional collaboration.
- Incident Response Tools and Technologies: Lesson 14 explores various tools and technologies that support the incident response process, such as incident management systems, forensic analysis tools, and threat intelligence platforms. It provides insights into their functionalities and considerations for their selection and implementation.
- Post-Incident Analysis and Lessons Learned: The lesson discusses the importance of conducting post-incident analysis and documenting lessons learned. It emphasizes the iterative nature of incident response, where organizations continuously improve their incident response capabilities based on insights gained from previous incidents.
The CS Lesson 14 PDF Resource:
The accompanying PDF resource for CS Lesson 14 serves as a comprehensive guide to incident response, offering detailed explanations, practical examples, and actionable insights. It provides organizations and individuals with valuable information for establishing and enhancing their incident response capabilities. The PDF covers topics such as incident response planning, incident detection and analysis, containment strategies, recovery techniques, and post-incident analysis.
Furthermore, the CS Lesson 14 PDF resource includes additional references and resources that readers can explore to further expand their knowledge in incident response. These resources may include incident response frameworks, case studies, incident response playbooks, and industry guidelines.
Conclusion:
In conclusion, incident response is a critical component of an organization’s cybersecurity strategy. CS Lesson 14 focuses on establishing effective incident response capabilities, covering the incident response lifecycle, incident response team structure, tools and technologies, and post-incident analysis. By implementing the principles outlined in this lesson, organizations can enhance their ability to detect, respond to, and recover from security incidents.
The accompanying PDF resource serves as a valuable reference, providing practical guidance and additional resources to support the establishment of a robust incident response capability. By prioritizing incident response, organizations can effectively mitigate the impact of security incidents and protect their digital assets in today’s dynamic threat landscape.
Nu Of Pages:
6 Pages
Download The Lesson PDF:
Access The Others CS Lessons From Here

















