In today’s interconnected world, network attacks pose a significant threat to individuals, organizations, and critical infrastructure. Cyber criminals are constantly evolving their tactics to exploit vulnerabilities in networks and compromise sensitive information. To effectively defend against these threats, it is essential to understand the various types of network attacks and the countermeasures available.
In this Lesson, we introduce the “Cyber Security Network Attacks: Defending Against Evolving Threats with the CS Lesson 8 PDF Guide.” This comprehensive guide serves as a valuable resource to enhance your knowledge of network attacks, drawing insights from CS Lesson 8.
Let’s delve into the world of network security and equip ourselves to safeguard against evolving cyber threats.



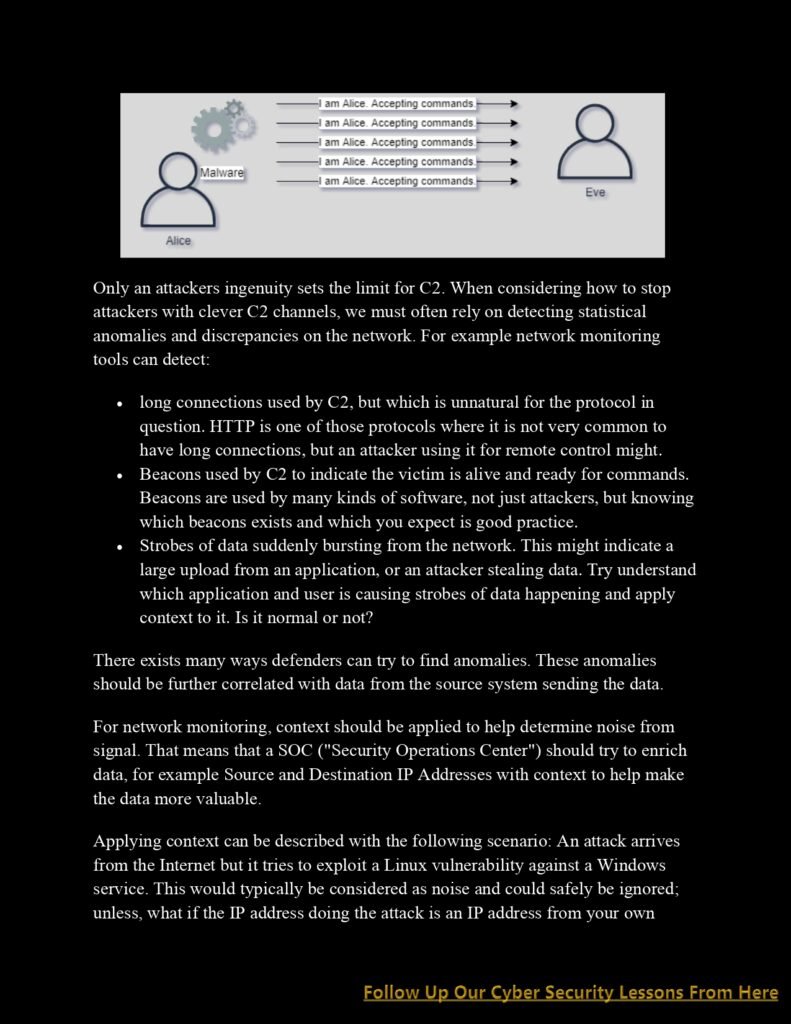
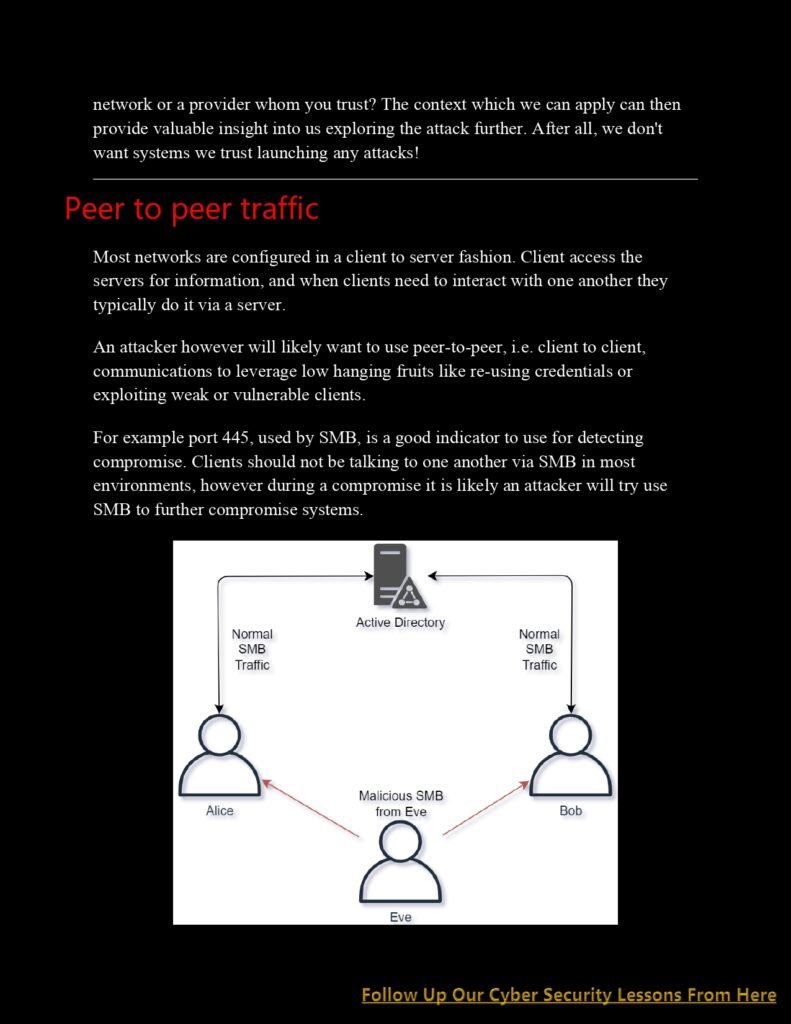

Understanding Network Attacks:
“Cyber Security Network Attacks: CS Lesson 8 PDF Guide” provides an in-depth exploration of network attacks, covering the following key topics:
a. Common Network Attack Techniques: Gain insights into various network attack techniques, including but not limited to, Denial of Service (DoS) attacks, Man-in-the-Middle (MitM) attacks, Phishing, Spoofing, and Distributed Denial of Service (DDoS) attacks. Understand how these attacks are executed, their impacts, and the methods to detect and mitigate them.
b. Social Engineering Attacks: Explore the realm of social engineering attacks that exploit human vulnerabilities to gain unauthorized access. Learn about techniques such as phishing, pretexting, baiting, and tailgating, and understand how to educate users and implement security awareness programs to mitigate these risks.
c. Network Intrusion: Understand the techniques used by attackers to gain unauthorized access to networks. Learn about common attack vectors such as brute-force attacks, password cracking, and network eavesdropping. Discover effective strategies to secure network perimeters and prevent unauthorized access.
Defense Mechanisms and Countermeasures:
“Cyber Security Network Attacks: CS Lesson 8 PDF Guide” offers practical guidance on defending against network attacks. The guide includes:
a. Intrusion Detection and Prevention Systems (IDS/IPS): Understand the role of IDS and IPS in network security. Learn how these systems detect and respond to network attacks by analyzing network traffic patterns and applying security policies.
b. Firewalls and Network Segmentation: Explore the importance of firewalls in securing network boundaries and regulating incoming and outgoing traffic. Understand network segmentation techniques to isolate critical assets and limit the impact of potential attacks.
c. Encryption and Virtual Private Networks (VPNs): Discover the significance of encryption and VPNs in securing network communications. Learn how to implement secure encryption protocols and establish secure communication channels to protect sensitive data.
Benefits of the PDF Guide:
“Cyber Security Network Attacks: CS Lesson 8 PDF Guide” offers several benefits to individuals seeking to enhance their understanding of network attacks and defense mechanisms:
a. Comprehensive Resource: The guide serves as a comprehensive resource, covering essential network attack types and their countermeasures. It provides a solid foundation for individuals looking to strengthen their knowledge and expertise in this area.
b. Portability and Accessibility: The PDF format allows you to access the guide on multiple devices, making it convenient to learn about network attacks and defense mechanisms anytime and anywhere.
c. Offline Availability: Once downloaded, the PDF guide becomes an offline resource, ensuring that you have access to vital network security information even without an internet connection.
Conclusion:
“Cyber Security Network Attacks: Defending Against Evolving Threats with the CS Lesson 8 PDF Guide” equips you with the essential knowledge required to enhance your understanding of network attacks and strengthen your network defenses. By providing an in-depth exploration of network attack techniques and the corresponding countermeasures, this guide empowers you to proactively defend against evolving cyber threats.
Download “Cyber Security Network Attacks: CS Lesson 8 PDF Guide” and embark on your journey to mastering network security. Whether you’re a network administrator, security professional, or an enthusiast seeking to enhance your knowledge, this guide will support you at every step.
With the insights and defense mechanisms provided in the guide, you can fortify the security of your networks, detect and mitigate network attacks, and protect your valuable data and assets. Embrace “Cyber Security Network Attacks: CS Lesson 8 PDF Guide” and take a significant stride towards a resilient and secure network environment.
Download “Cyber Security Network Attacks: CS Lesson 8 PDF Guide” and equip yourself with the knowledge to defend against network attacks effectively. Let’s prioritize a comprehensive understanding of network attack techniques and stay ahead of emerging cyber threats.
Nu Of Pages:
11 Pages
Download The Lesson PDF:
Access The Others CS Lessons From Here

















