In today’s digital age, Wi-Fi has become an integral part of our lives. Whether it’s at home, in the office, or at a coffee shop, we rely on Wi-Fi networks for seamless connectivity and access to the internet. However, with the increasing reliance on Wi-Fi, the risks associated with cyber security have also grown.
Cybercriminals are constantly devising new and sophisticated techniques to exploit vulnerabilities in Wi-Fi networks. In this blog post, we will delve into the world of Wi-Fi attacks and explore some essential lessons in cyber security.
Understanding Wi-Fi Networks:
To comprehend Wi-Fi attacks, it is crucial to have a basic understanding of how these networks function. Wi-Fi networks operate on radio waves, allowing devices to communicate wirelessly. They rely on a protocol called the IEEE 802.11 standard, which defines how data is transmitted and received. This knowledge lays the foundation for understanding potential vulnerabilities.



Common Wi-Fi Attacks:
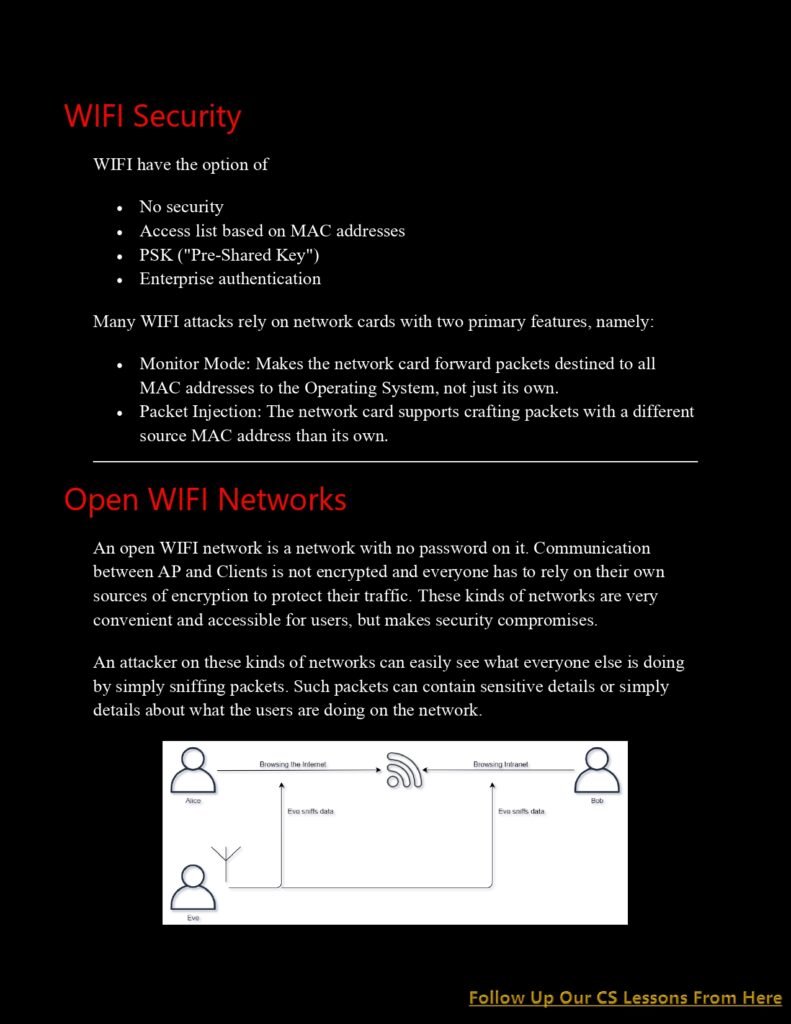
- Man-in-the-Middle (MitM) Attacks: In this type of attack, an attacker intercepts the communication between two devices on a Wi-Fi network. By doing so, they can eavesdrop on sensitive information or even modify the data
- Rogue Access Points: Cybercriminals can set up rogue access points to mimic legitimate Wi-Fi networks. Unsuspecting users may connect to these fake networks, unknowingly exposing their data to the attacker. Rogue access points are often used to launch various other attacks, such as phishing or credential theft.
- Evil Twin Attacks: Similar to rogue access points, evil twin attacks involve the creation of a fake Wi-Fi network. However, in this case, the attacker’s network has the same name (SSID) as a legitimate network, tricking users into connecting to it. Once connected, the attacker can intercept data or launch further attacks.
Protecting Against Wi-Fi Attacks:
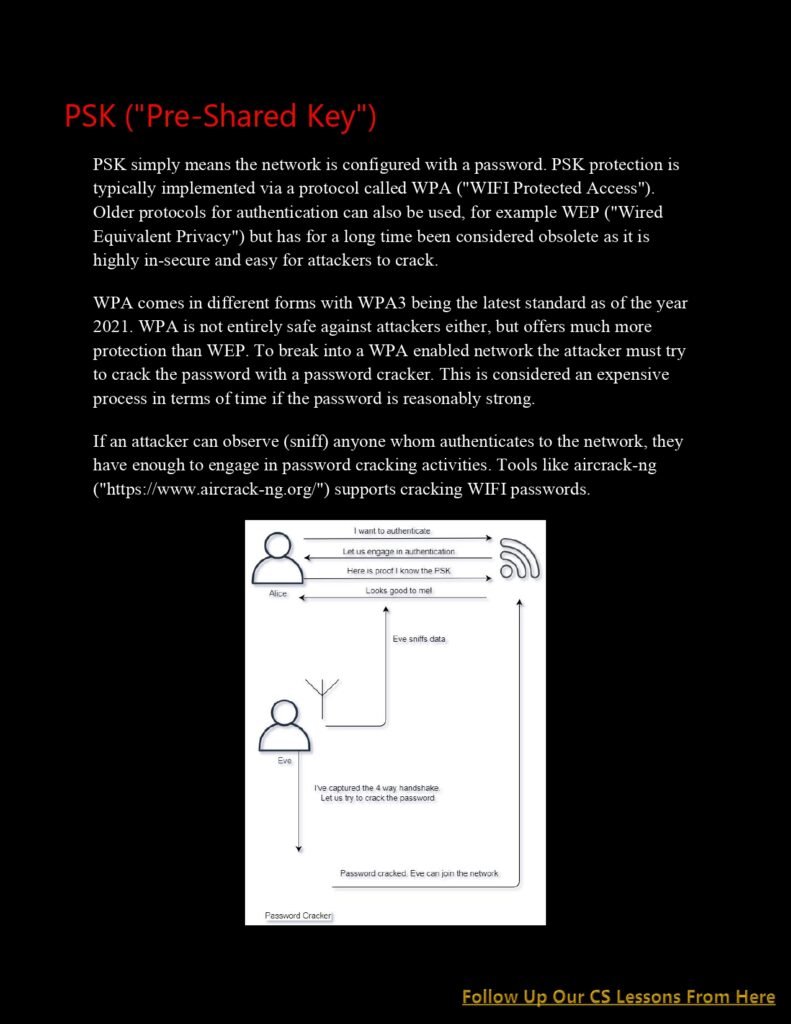
- Strong Encryption: Ensure that your Wi-Fi network is encrypted using the latest security protocols, such as WPA3. Encryption adds an extra layer of protection by encoding the data transmitted over the network, making it difficult for attackers to decipher.
- Two-Factor Authentication (2FA): Implement 2FA wherever possible, especially for sensitive accounts. This adds an extra authentication step, making it harder for attackers to gain unauthorized access even if they manage to infiltrate your Wi-Fi network.
- Regular Software Updates: Keep your Wi-Fi routers and connected devices up to date with the latest firmware and security patches. Manufacturers often release updates to address known vulnerabilities and strengthen the security of their products.
- Disable Remote Management: Unless necessary, disable remote management features on your Wi-Fi router. These features can be an entry point for attackers to gain control over your network.
- Avoid Public Wi-Fi Networks: Public Wi-Fi networks, such as those found in coffee shops or airports, are often unsecured and prone to attacks. Whenever possible, use a virtual private network (VPN) to encrypt your data and ensure secure communication.
Nu Of Pages:
6 Pages
Download The Lesson PDF:
Access The Others CS Lessons From Here