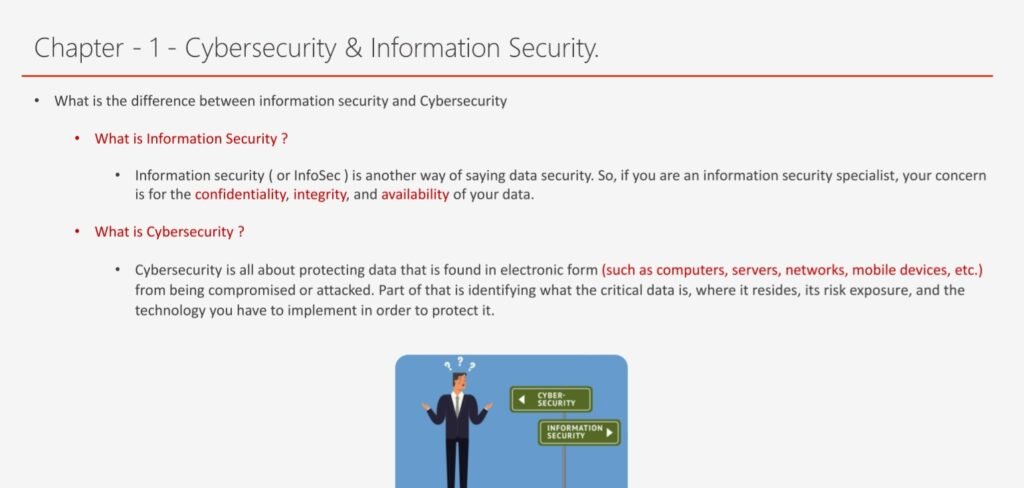
Information security and cybersecurity are two related but distinct fields that deal with the protection of data, systems, and networks from unauthorized access, use, disclosure, modification, or destruction. Information security focuses on the confidentiality, integrity, and availability of information, regardless of its format or medium. Cybersecurity focuses on the prevention, detection, and response to cyberattacks that target or exploit cyberspace, which includes the internet, computers, mobile devices, and other interconnected systems.
Both information security and cybersecurity are essential for any organization or individual that relies on information and technology for their operations, communication, and transactions. However, achieving and maintaining a high level of security is not an easy task, as it requires a comprehensive and systematic approach that involves policies, standards, procedures, technologies, tools, and practices. Moreover, the security landscape is constantly evolving and changing, as new threats, vulnerabilities, and challenges emerge every day.
To help you understand and implement the best practices and guidelines for information security and cybersecurity, we have prepared a PDF document that contains detailed and practical notes on various topics and domains of security. This PDF document is based on the latest standards and frameworks of security, such as ISO 27001, NIST SP 800-53, and CIS Controls. It is designed to help you learn and apply the security principles and concepts that are relevant and applicable to your context and needs. We will also give you an overview of the content and the key topics of the PDF document, and provide you with a link to download it for free.
Overview of the Notes
The Information Security and Cybersecurity Guidelines PDF is a 152-page document that contains concise and clear notes on 11 topics and domains of security. The notes are organized in a logical and easy-to-follow manner, and they include definitions, examples, diagrams, tables, and charts to illustrate the concepts and principles. The notes also highlight the important points and tips that you need to remember and apply for security.

The information security and cybersecurity guidelines PDF is not a substitute for the official standards and frameworks of security, but rather a supplement that can help you review and reinforce your knowledge and understanding of the security objectives and requirements. The PDF document is also not a guarantee that you will achieve or maintain a high level of security, but rather a tool that can assist you in your security planning and implementation.
The information security and cybersecurity guidelines PDF is updated regularly to reflect the changes and updates in the security standards and frameworks, as well as the security trends and best practices. The latest version of the PDF document is based on the 2021 edition of the security standards and frameworks.
The Content of the Notes
The information security and cybersecurity guidelines PDF covers 11 topics and domains of security, which are:
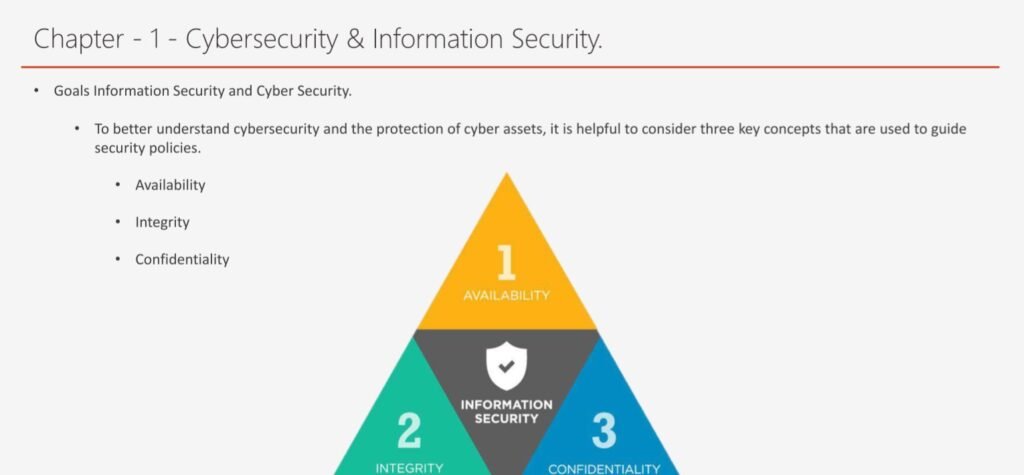
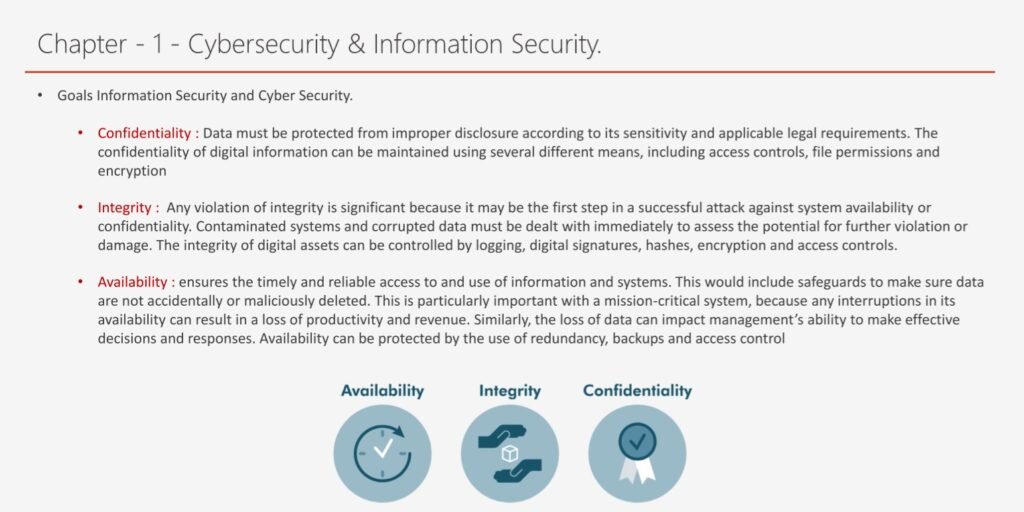
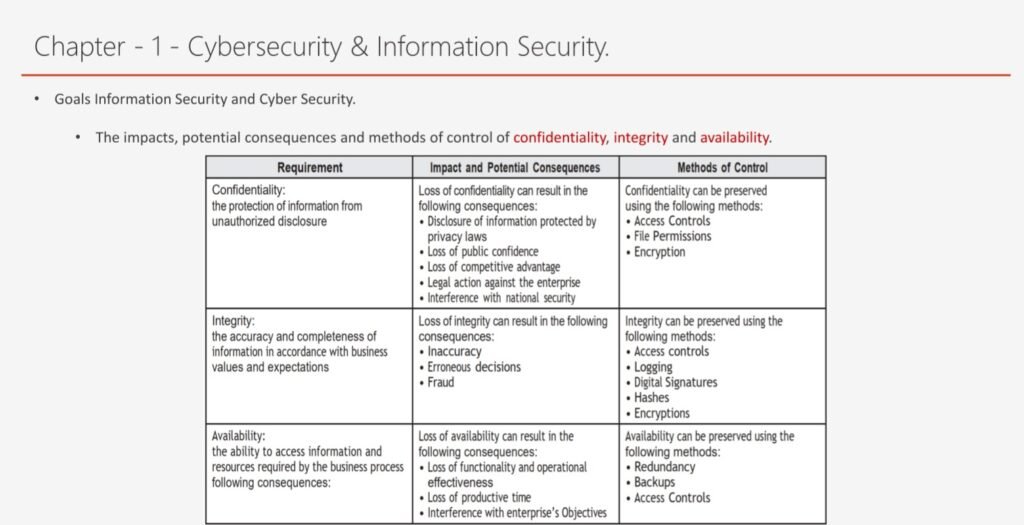
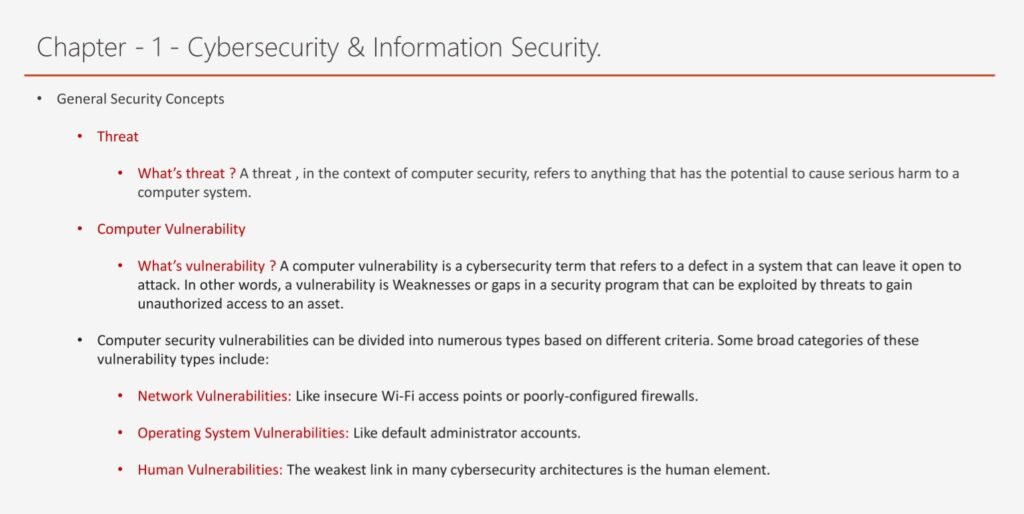
- Cybersecurity & Information Security: This topic introduces the basic concepts and definitions of cybersecurity and information security, and explains the differences and similarities between them. It also discusses the security objectives, principles, and challenges, and the security standards and frameworks that guide the security practices and processes.
- Cyber Security Threats: This topic describes the various types of cyber security threats that can affect the information and systems, such as malware, phishing, denial-of-service, ransomware, insider threats, and advanced persistent threats. It also explains the threat actors, their motivations, and their methods, and the threat landscape, trends, and sources.
- Access Controls: This topic covers the access control concepts and mechanisms that are used to regulate and restrict the access to the information and systems, such as identification, authentication, authorization, and accountability. It also discusses the access control models, such as discretionary, mandatory, and role-based, and the access control methods, such as passwords, tokens, biometrics, and multifactor.
- Security Operations: This topic covers the security operations concepts and processes that are used to monitor and manage the security of the information and systems, such as security policies, procedures, baselines, audits, reviews, and metrics. It also discusses the security operations functions, such as configuration management, change management, patch management, backup and recovery, and asset management.
- Risk Identification, Monitoring, and Analysis: This topic covers the risk management concepts and methodologies that are used to identify, assess, and treat the security risks that can affect the information and systems, such as risk appetite, risk tolerance, risk analysis, risk mitigation, and risk transfer. It also discusses the risk management tools and techniques, such as risk registers, risk matrices, risk assessments, and risk treatment plans.
- Incident Response and Recovery: This topic covers the incident response and recovery concepts and processes that are used to respond to and recover from the security incidents that affect the information and systems, such as incident detection, incident classification, incident containment, incident eradication, incident recovery, and incident closure. It also discusses the incident response and recovery tools and resources, such as incident response teams, incident response plans, incident response kits, and incident response reports.
- Networks and Communications Security: This topic covers the network and communications security concepts and technologies that are used to protect the network and communications infrastructure and services, such as network architecture, network devices, network protocols, network services, and network security devices. It also discusses the network and communications security threats and countermeasures, such as firewalls, intrusion detection and prevention systems, virtual private networks, encryption, and authentication.
- Systems and Application Security: This topic covers the system and application security concepts and technologies that are used to protect the system and application software and hardware, such as operating systems, databases, web servers, web applications, mobile applications, and cloud computing. It also discusses the system and application security threats and countermeasures, such as malware protection, vulnerability scanning, penetration testing, code review, and secure coding.
- Operational Security: This topic covers the operational security concepts and practices that are used to protect the physical and human aspects of the security, such as physical security, environmental security, personnel security, and awareness and training. It also discusses the operational security threats and countermeasures, such as locks, alarms, cameras, guards, badges, policies, and education.
- Security Best Practice: This topic covers the security best practice concepts and recommendations that are used to improve and enhance the security of the information and systems, such as security governance, security strategy, security culture, security maturity, and security benchmarking. It also discusses the security best practice sources and references, such as security standards, frameworks, guidelines, and checklists.
- Cryptography: This topic covers the cryptography concepts and techniques that are used to protect the confidentiality, integrity, and authenticity of the information and systems, such as encryption, decryption, hashing, digital signatures, and key management. It also discusses the cryptography standards and protocols, such as symmetric encryption, asymmetric encryption, hash functions, digital signature algorithms, and key exchange protocols.
Each topic has its own section in the PDF document, and each section has several subtopics that correspond to the security objectives and requirements. For example, the Cybersecurity & Information Security section has subtopics such as:
- Cybersecurity & Information Security Concepts
- Cybersecurity & Information Security Differences and Similarities
- Cybersecurity & Information Security Objectives
- Cybersecurity & Information Security Principles
- Cybersecurity & Information Security Challenges
- Cybersecurity & Information Security Standards and Frameworks
Each subtopic has a brief introduction, followed by the main points and details that you need to know and apply for security. The subtopics also include examples and diagrams to demonstrate the application and implementation of the concepts and principles.
Key Topics
The information security and cybersecurity guidelines PDF covers a lot of information and topics that are relevant and essential for security. However, some topics are more important and critical than others, and you should pay more attention and focus to them. Some of the key topics that you should not miss are:
- The security objectives and principles that guide the security practices and processes
- The security threats and vulnerabilities that can affect the information and systems
- The security controls and countermeasures that can prevent, detect, and respond to the security incidents
- The security operations and processes that can monitor and manage the security of the information and systems
- The risk management methodologies that can identify, assess, and treat the security risks
- The incident response and recovery processes that can restore the normal operations after a security incident
- The network and communications security technologies that can protect the network and communications infrastructure and services
- The system and application security technologies that can protect the system and application software and hardware
- The operational security practices that can protect the physical and human aspects of the security
- The security best practices that can improve and enhance the security of the information and systems
- The cryptography techniques that can protect the confidentiality, integrity, and authenticity of the information and systems
These key topics are not exhaustive, and you should still review and study all the topics and domains of security. However, these key topics are the ones that you should master and understand well, as they will help you achieve and maintain a high level of security.
Conclusion
The information security and cybersecurity guidelines PDF is a valuable and useful resource that can help you learn and apply the best practices and guidelines for security. It contains concise and clear notes on 11 topics and domains of security, and it covers the most important and relevant concepts and principles that you need to know. The PDF document is also updated and aligned with the latest standards and frameworks of security.
The information security and cybersecurity guidelines PDF is not a magic bullet that will guarantee your security, but rather a tool that can support and enhance your security planning and implementation. You should still use other sources and methods to learn and practice security, such as books, courses, videos, podcasts, webinars, and workshops. You should also plan and schedule your security time and strategy, and review and test your security knowledge and skills regularly.
Security is a continuous and dynamic process that requires constant attention and improvement. By using the information security and cybersecurity guidelines PDF
Download The Guide PDF:
Access The Others CS Lessons From Here

















