The Internet of Things (IoT) has rapidly transformed the way we interact with the world, connecting devices and systems to enhance efficiency and convenience. However, as the IoT ecosystem expands, so does the concern for security vulnerabilities.
In this digital age, safeguarding the integrity and privacy of IoT devices is paramount. To address this critical need, we present “Introduction to IoT Security (PDF),” a comprehensive document aimed at providing insights into the fundamentals of securing IoT ecosystems.
Overview of Our Document:
“Introduction to IoT Security” is a valuable resource designed for individuals and organizations looking to understand the intricacies of securing IoT devices and networks.

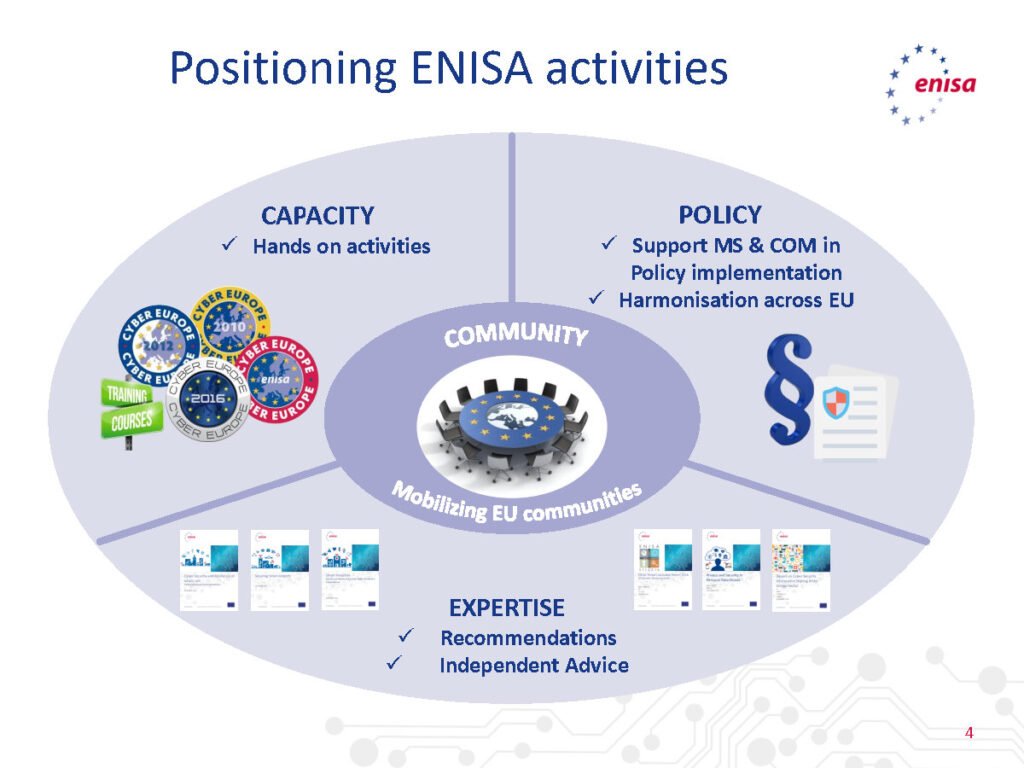

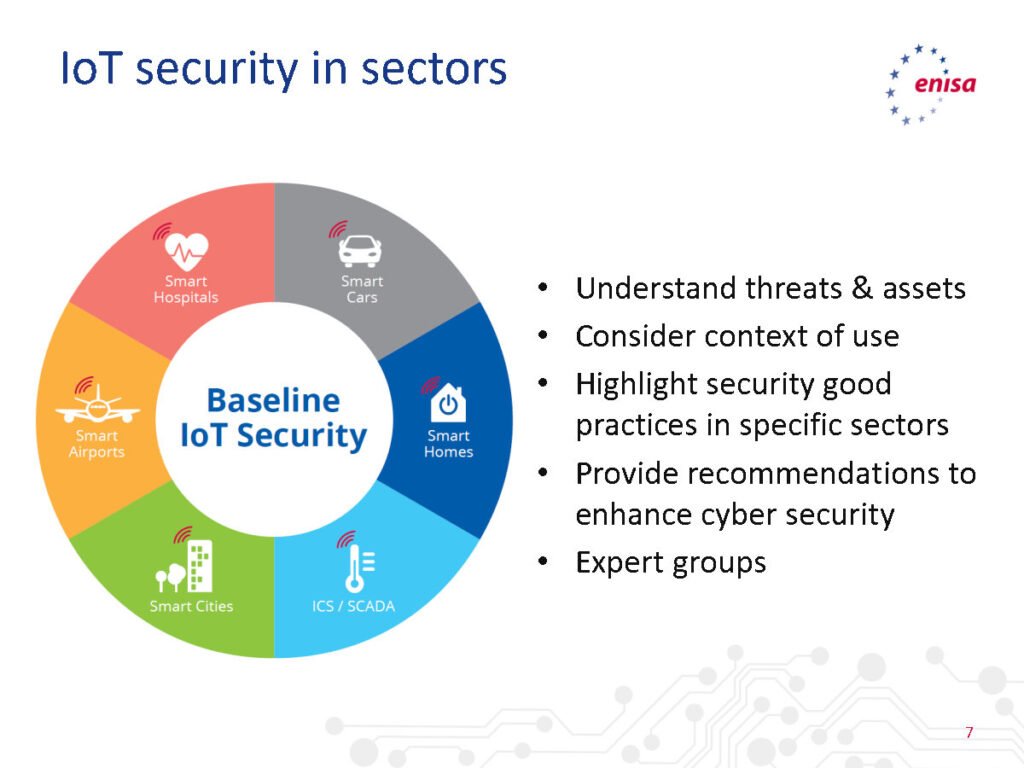

This document serves as a foundational guide, offering insights into the unique challenges posed by IoT security and providing practical measures to mitigate risks. Whether you are a developer, IoT enthusiast, or business owner integrating IoT into your operations, this guide is tailored to provide you with the knowledge needed to navigate the complex landscape of IoT security.
The Content of the Document:
The document is structured to cover key aspects of IoT security, ensuring a holistic understanding of the challenges and solutions. Here’s a breakdown of the essential content:
- Understanding IoT Security: Begin with an exploration of the unique security challenges posed by the IoT landscape. Delve into the complexities of securing interconnected devices, data transmission, and the diverse range of IoT applications.
- Key Threats in IoT Security: Identify and understand the common threats that IoT devices face, including unauthorized access, data breaches, device tampering, and denial-of-service attacks. Explore real-world examples to illustrate the potential consequences of security vulnerabilities.
- Security Best Practices for IoT Devices: Gain insights into the best practices for securing individual IoT devices. Explore principles such as secure bootstrapping, device authentication, and encryption to fortify the resilience of IoT endpoints.
- Network Security in IoT: Examine the critical role of network security in an IoT ecosystem. Learn about secure communication protocols, segmenting IoT networks, and implementing firewalls to protect data in transit.
- Data Security and Privacy: Understand the importance of safeguarding sensitive data generated by IoT devices. Explore encryption techniques, data anonymization, and privacy-by-design principles to uphold the confidentiality and privacy of user information.
- Regulatory Compliance in IoT Security: Navigate the regulatory landscape surrounding IoT security. Learn about industry standards and compliance frameworks that guide the implementation of robust security measures in accordance with legal and regulatory requirements.
Why This Document:
“Introduction to IoT Security” is a crucial document for several reasons:
- Rising Significance of IoT: As IoT continues to proliferate across industries, the need for understanding and implementing robust security measures becomes increasingly critical.
- Practical Guidance: The document provides practical guidance, offering actionable insights and best practices that can be applied to enhance the security posture of IoT ecosystems.
- Awareness and Preparedness: In a landscape where cybersecurity threats are evolving, this guide fosters awareness and preparedness, enabling individuals and organizations to proactively address IoT security challenges.
Conclusion:
As we embrace the transformative power of IoT, it is imperative to acknowledge and address the associated security risks. “Introduction to IoT Security” equips you with the foundational knowledge and practical measures needed to navigate the complexities of securing IoT devices and networks. By implementing the insights gained from this guide, you contribute to building a more secure and resilient IoT ecosystem.
Download From below Link:
To access “Introduction to IoT Security” and enhance your understanding of securing IoT environments, click on the link below:
Download Introduction to IoT Security (PDF)
Equip yourself with the knowledge and tools to safeguard IoT devices, protect data integrity, and contribute to a secure digital future. Happy reading and securing!