In today’s interconnected world, industrial control systems (ICS) and operational technology (OT) play a vital role in ensuring the smooth functioning of critical infrastructure. However, with the increasing digitization and connectivity of these systems, they have become vulnerable to cyber threats. As a result, the need for robust OT cyber security measures has become more important than ever.
Our comprehensive guide, “OT Cyber Security Competency Framework PDF,” aims to address this need by providing you with a step-by-step approach to understanding and implementing effective OT cyber security strategies. Whether you are an IT professional, an engineer, or a manager responsible for the security of your organization’s OT systems, this guide will equip you with the knowledge and skills necessary to protect your critical infrastructure from cyber attacks.
Overview of the Guide
The guide begins by providing an overview of the current threat landscape in the OT sector. It explores the various types of cyber threats that can target industrial control systems, such as malware, ransomware, and advanced persistent threats. By understanding the nature of these threats, you will be better prepared to identify and mitigate potential risks to your OT systems.

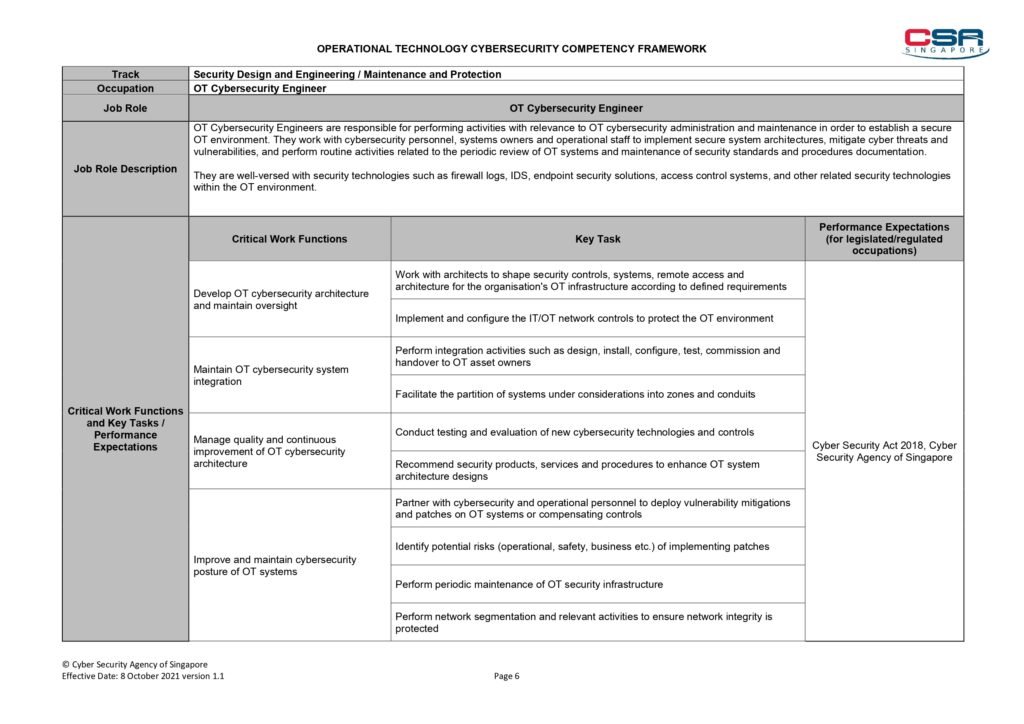
Next, the guide delves into the core principles of OT cyber security. It covers essential topics such as risk assessment, vulnerability management, incident response, and security awareness training. By following these principles, you will be able to establish a strong foundation for protecting your organization’s OT infrastructure.
The Content of the Guide
The “OT Cyber Security Competency Framework PDF” guide is divided into several sections, each focusing on a specific aspect of OT cyber security. These sections include:
- Introduction to OT Cyber Security
- Risk Assessment and Management
- Network Security and Segmentation
- Security Monitoring and Incident Response
- Secure Configuration and Patch Management
- Physical Security and Access Control
- Training and Awareness
- Emerging Threats and Future Trends
Each section provides in-depth insights, practical tips, and real-world examples to help you understand the key concepts and best practices in OT cyber security. The guide also includes interactive exercises and case studies to reinforce your learning and test your knowledge.
Key Topics
Within each section of the guide, there are several key topics that are covered in detail. Some of the key topics include:
- Understanding the unique challenges of OT cyber security
- Identifying and assessing OT cyber risks
- Implementing effective security controls in OT environments
- Detecting and responding to OT cyber incidents
- Developing a comprehensive OT cyber security strategy
- Evaluating and selecting OT cyber security solutions
- Building a culture of security awareness in OT organizations
- Ensuring regulatory compliance in OT systems
- Managing third-party risks in OT environments
- Conducting penetration testing and vulnerability assessments in OT networks
- Securing legacy systems and integrating new technologies in OT environments
Number of Guide (113 Pages)
The “OT Cyber Security Competency Framework PDF” guide is a comprehensive resource that spans 113 pages. Each page is filled with valuable insights, practical tips, and real-world examples to enhance your understanding of OT cyber security.
Download from Link
To access the “OT Cyber Security Competency Framework PDF” guide, please click on the following link: [From here].
We hope you find this guide informative and useful in your pursuit of OT cyber security excellence.

















