As technology continues to advance at an unprecedented pace, the need for robust cybersecurity measures has become more critical than ever before. With the increasing prevalence of cyber threats such as data breaches, identity theft, and malware attacks, it is essential for individuals and organizations to stay informed and proactive in their approach to online security.
In this guide, we will delve into various aspects of cybersecurity, starting with the fundamentals. We will explore the different types of cyber threats that exist in today’s digital landscape and examine the potential consequences of falling victim to these threats. Understanding the risks involved is crucial in developing a comprehensive cybersecurity strategy.
Next, we will discuss the importance of creating strong passwords and implementing multi-factor authentication to protect your online accounts. We will provide practical tips on how to create passwords that are difficult to crack and explain the benefits of using additional layers of security to verify your identity.



In addition to securing your online accounts, we will also address the importance of keeping your devices and software up to date. Outdated software can leave vulnerabilities that cybercriminals can exploit, so regular updates are essential to ensure that you have the latest security patches and bug fixes.
Furthermore, we will explore the concept of social engineering and how cybercriminals use psychological manipulation to trick individuals into revealing sensitive information. By understanding common social engineering techniques such as phishing and pretexting, you can better protect yourself and your organization from falling victim to these schemes.
Another crucial aspect of cybersecurity is data protection. We will discuss the importance of backing up your data regularly and implementing encryption measures to safeguard your sensitive information. Additionally, we will explore the concept of data privacy and the steps you can take to protect your personal information from being exploited.
Lastly, we will highlight the significance of cybersecurity awareness and education. By staying informed about the latest cyber threats and best practices, you can empower yourself and your organization to make informed decisions and take proactive measures to mitigate risks.
Throughout this guide, we will provide real-world examples and practical advice to help you apply the concepts discussed. Whether you are an individual or a business owner, investing time and effort into enhancing your cybersecurity is a worthwhile endeavor that can save you from potential financial and reputational damage.
So, let’s dive in and embark on this journey to strengthen your online security!
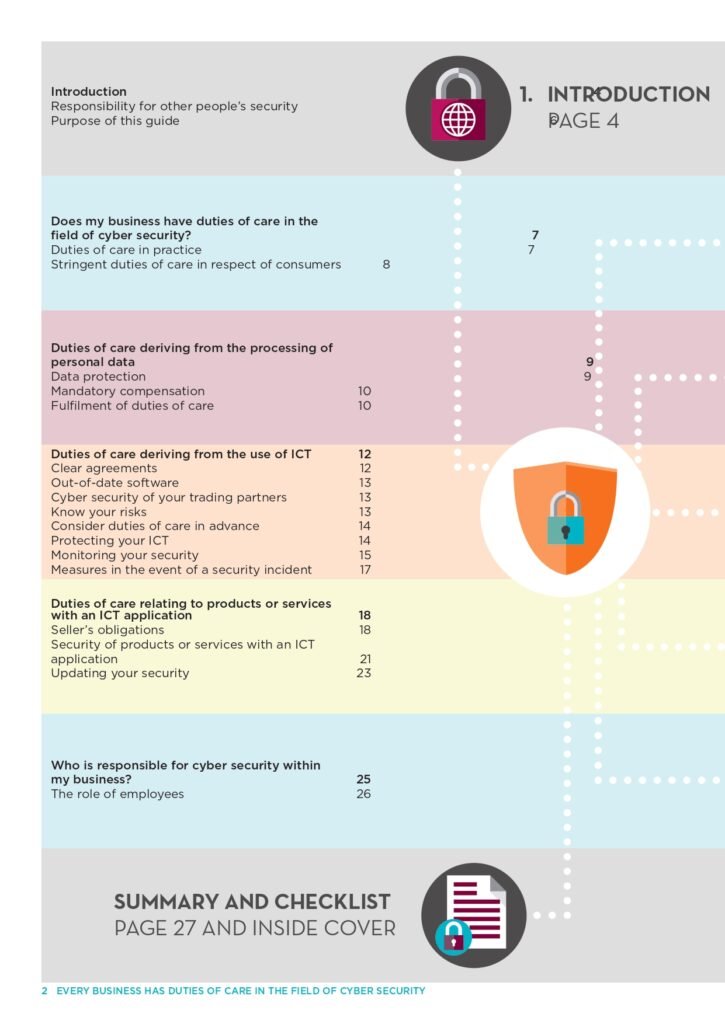
The Cyber Security Guide is divided into several sections, each focusing on a specific aspect of online security. The first section provides an introduction to the importance of cyber security in today’s digital age. It explains the various threats that individuals and organizations face, including malware, phishing attacks, and data breaches. By understanding these risks, readers will gain a better appreciation for the need to protect their personal and sensitive information.
The guide then delves into the fundamentals of cyber security, covering topics such as password management, encryption, and secure browsing. It offers practical tips and best practices for creating strong passwords, using password managers, and identifying secure websites for online transactions. Additionally, it explains the concept of encryption and how it can be used to safeguard sensitive data during transmission and storage.
As the guide progresses, it explores more advanced topics in cyber security, such as network security, wireless security, and mobile device security. It provides insights into securing home and office networks, including setting up firewalls, using virtual private networks (VPNs), and detecting and preventing unauthorized access. The guide also offers guidance on securing wireless networks, including tips for choosing strong Wi-Fi passwords and enabling encryption protocols.
With the increasing use of mobile devices, the guide recognizes the need for mobile security. It discusses the risks associated with mobile devices, such as malware infections and data leakage, and provides strategies for securing smartphones and tablets. This includes advice on installing reputable security apps, enabling device encryption, and being cautious of public Wi-Fi networks.
Furthermore, the Cyber Security Guide addresses the importance of social engineering awareness. It educates readers on common social engineering techniques, such as phishing and pretexting, and offers guidance on how to recognize and avoid falling victim to these scams. By understanding the tactics employed by cyber criminals, individuals can better protect themselves from becoming targets of social engineering attacks.
In addition to these topics, the guide also covers incident response and recovery, emphasizing the importance of having a plan in place to mitigate the impact of a cyber security incident. It provides guidance on how to detect and respond to security breaches, as well as steps to take in order to recover from an attack.
Overall, the Cyber Security Guide serves as a comprehensive resource for individuals and organizations looking to enhance their understanding of online security. Whether you are a beginner looking to learn the basics or an advanced user seeking more in-depth knowledge, this guide offers valuable insights and practical advice to help you stay safe and secure in the digital world.
The Content of the Guide
The Cyber Security Guide is divided into several sections, each focusing on a specific aspect of cybersecurity. The guide starts by introducing the importance of cybersecurity and the potential risks individuals and businesses face in today’s digital landscape. It then delves into various topics, providing comprehensive information and practical advice to help readers protect themselves and their digital assets.
The first section of the guide focuses on understanding common cyber threats and attack vectors. It explains the different types of threats individuals and businesses may encounter, such as malware, ransomware, and phishing attacks. The section provides real-life examples and case studies to illustrate the impact of these threats and offers guidance on how to identify and mitigate them.
Another important topic covered in the guide is the creation of strong and unique passwords. This section explains the importance of using complex passwords and provides tips on how to create and manage them effectively. It also discusses the use of password managers and two-factor authentication as additional layers of security.
Securing devices and networks is also a crucial aspect of cybersecurity, and the guide offers best practices for achieving this. It covers topics such as keeping software and firmware up to date, using secure Wi-Fi networks, and configuring firewalls and antivirus software. The section also addresses the growing trend of remote work and telecommuting, providing recommendations for secure practices in these environments.
In addition to protecting devices and networks, the guide emphasizes the importance of safeguarding sensitive information while browsing the internet. It provides insights into secure browsing habits, such as using HTTPS connections, avoiding suspicious websites, and being cautious with sharing personal information online.
Phishing scams are a prevalent threat, and the guide dedicates a section to help readers recognize and avoid falling victim to them. It explains the different techniques used by cybercriminals to trick individuals into revealing sensitive information and provides tips on how to spot and report phishing attempts.
For those who engage in online transactions and handle financial information, the guide offers guidance on how to secure these activities. It covers topics such as using secure payment methods, verifying the authenticity of websites, and monitoring financial accounts for suspicious activity.
The role of antivirus software and firewalls in cybersecurity is also explained in detail. The guide outlines the features and benefits of these security tools and provides recommendations for selecting and configuring them effectively.
Each section of the guide is designed to be informative and practical, providing detailed explanations, practical examples, and actionable steps that readers can take to enhance their cybersecurity posture. By following the advice and recommendations outlined in the guide, individuals and businesses can better protect themselves against cyber threats and minimize the risk of falling victim to cyberattacks.
Key Topics
Our Cyber Security Guide covers a wide range of key topics that are essential for anyone looking to improve their online security. In today’s digital age, where cyber threats are becoming increasingly sophisticated, it is crucial to stay informed and take proactive measures to protect your personal and financial information.
One of the key topics covered in the guide is understanding the importance of strong passwords. Many people underestimate the significance of using unique, complex passwords for each of their online accounts. We delve into the best practices for creating strong passwords that are difficult for hackers to crack.
Another important topic discussed in the guide is identifying and protecting against common cyber threats. With the rise of malware, ransomware, and phishing attacks, it is vital to be able to recognize the signs of these threats and take appropriate action to safeguard your devices and data. We provide practical tips and strategies to help you stay one step ahead of cybercriminals.
In addition, the guide offers valuable insights on securing your home network and Wi-Fi connection. With the increasing number of smart devices in our homes, it is crucial to ensure that our networks are properly protected against unauthorized access. We provide step-by-step instructions on how to set up a secure home network and maintain its integrity.
Protecting your personal and financial information online is another key topic covered in the guide. We discuss the importance of using secure websites for online transactions and provide guidance on how to spot potential red flags that indicate a website may not be trustworthy. Additionally, we explore the benefits of using virtual private networks (VPNs) to encrypt your internet connection and protect your privacy.
Recognizing and avoiding phishing scams and social engineering attacks is also a critical skill in today’s digital landscape. Cybercriminals often use deceptive tactics to trick individuals into revealing sensitive information or downloading malicious software. Our guide equips you with the knowledge to identify these scams and protect yourself from falling victim to them.
With the recent surge in remote work and telecommuting, implementing secure practices for remote work is more important than ever. We provide practical advice on how to secure your home office setup, use secure communication tools, and protect sensitive company information while working remotely.
Furthermore, the guide explains the role of antivirus software and firewalls in cybersecurity. These tools act as a first line of defense against malware and unauthorized access to your devices. We discuss the different types of antivirus software and firewalls available, as well as how to choose and configure them effectively.
Lastly, the guide offers best practices for secure online shopping and banking. As more and more transactions are conducted online, it is crucial to understand how to protect your financial information from cybercriminals. We provide tips on how to identify secure payment gateways, use secure online banking platforms, and protect yourself from identity theft.
By covering these key topics in our Cyber Security Guide, we aim to empower individuals with the knowledge and tools they need to navigate the digital world safely and confidently. With the right information and proactive measures, you can significantly reduce the risk of falling victim to cyber threats and protect your online presence.
Number of Guide (30 pages)
The Cyber Security Guide consists of 30 pages packed with valuable information and practical tips. Each page is carefully crafted to provide you with actionable insights that you can implement immediately to strengthen your cybersecurity defenses.
Download from Link
To access our Cyber Security Guide in PDF format, simply click on the following link: Download Cyber Security Guide. Once downloaded, you can save the guide to your device and refer to it whenever you need guidance on enhancing your online security.

















