Welcome to our website! In this post, we are excited to introduce you to our comprehensive guide on the best SOC analyst tools. Whether you are a seasoned professional or just starting out in the field of cybersecurity, this guide will provide you with valuable insights and recommendations to enhance your capabilities as a SOC analyst.


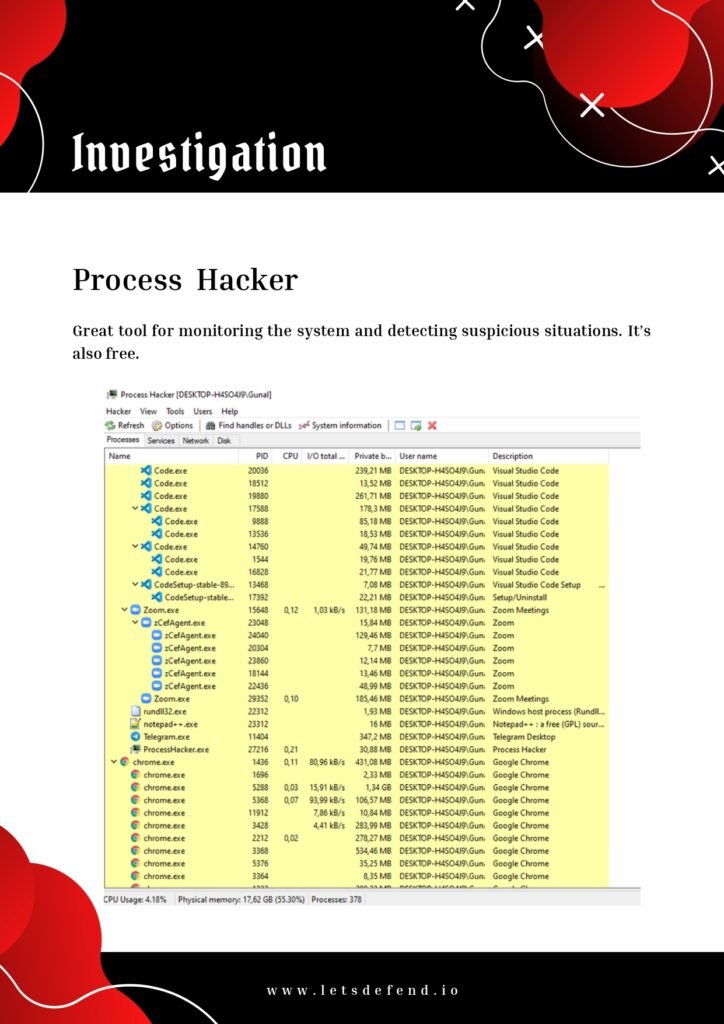
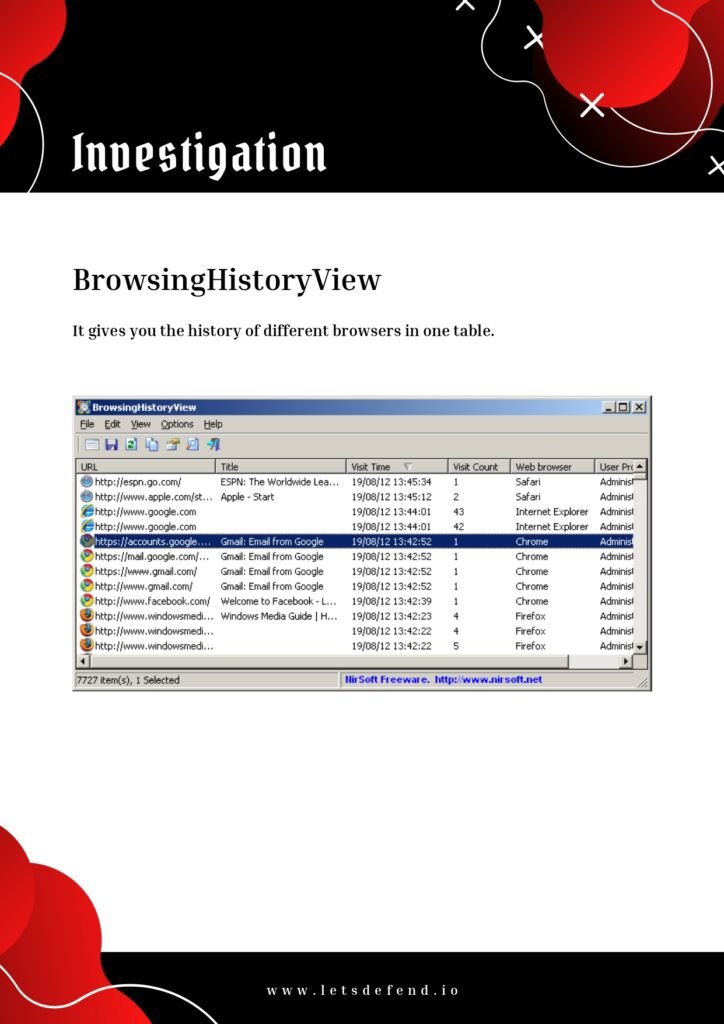
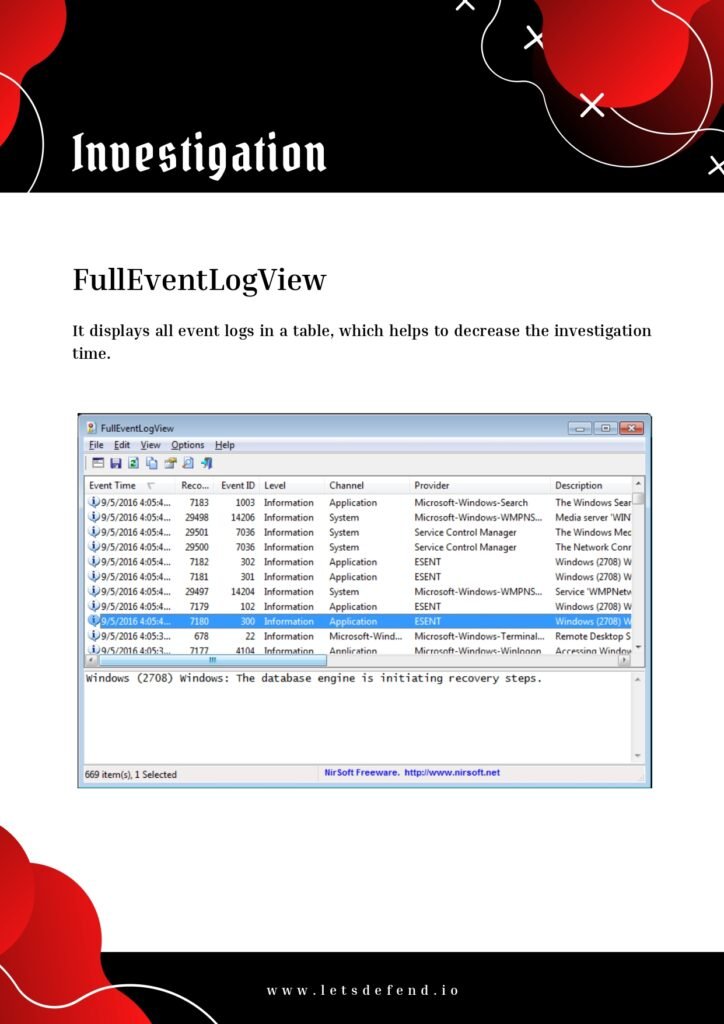

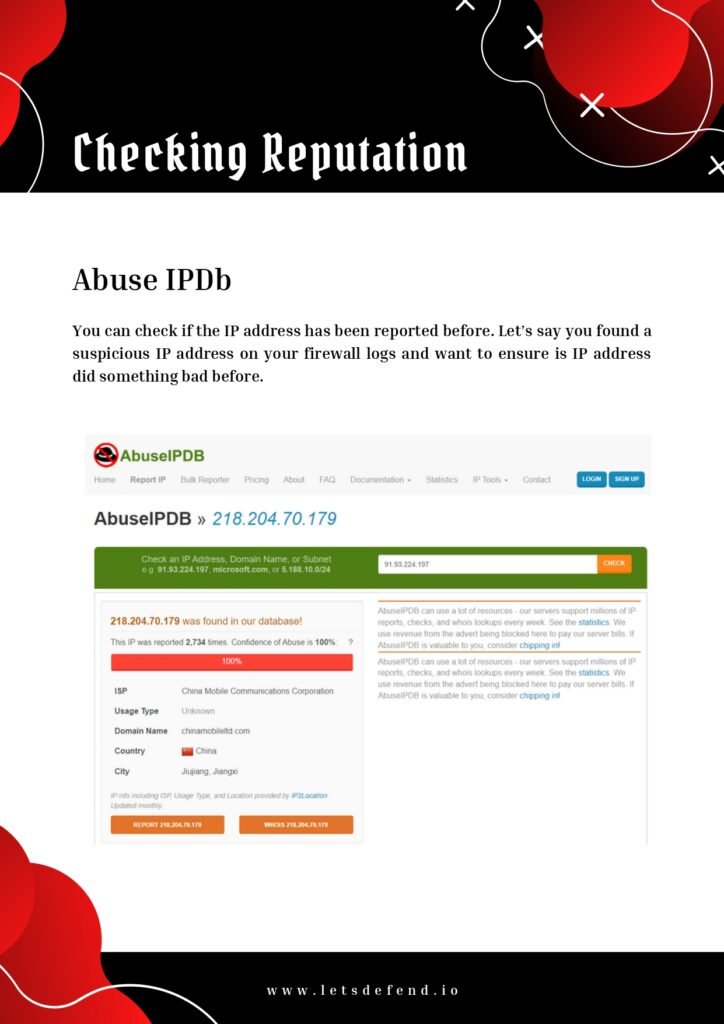


As the digital landscape continues to evolve, organizations face increasingly sophisticated cyber threats. The role of a SOC (Security Operations Center) analyst has become crucial in detecting, analyzing, and responding to these threats in real-time. SOC analysts are responsible for monitoring network traffic, analyzing security alerts, and mitigating potential risks to protect sensitive data and maintain the integrity of an organization’s systems.
However, the effectiveness of a SOC analyst heavily relies on the tools and technologies they have at their disposal. With the ever-growing number of cybersecurity solutions available in the market, it can be overwhelming to determine which tools are the most effective for your specific needs. That’s where our guide comes in.
In this comprehensive guide, we have meticulously researched and curated a list of the best SOC analyst tools that cover various aspects of the job. From threat intelligence platforms to SIEM (Security Information and Event Management) solutions, we have identified the tools that can empower SOC analysts to effectively detect, investigate, and respond to cyber threats.
Our guide not only provides an overview of each tool but also delves into their key features, benefits, and use cases. We understand that every organization has unique requirements, so we have included a range of tools that cater to different budgets, scalability needs, and technical expertise.
Additionally, we have taken into consideration the user experience and ease of implementation of these tools. We understand that SOC analysts often work under immense pressure, so we have selected tools that are intuitive, user-friendly, and can seamlessly integrate with existing security infrastructure.
Whether you are looking to enhance your threat intelligence capabilities, streamline incident response processes, or improve the overall efficiency of your SOC, our guide will provide you with the necessary information to make informed decisions.
So, whether you are a seasoned SOC analyst looking to upgrade your toolset or a newcomer to the field, we invite you to explore our comprehensive guide on the best SOC analyst tools. Equip yourself with the knowledge and resources you need to stay ahead of cyber threats and protect your organization’s critical assets.
Within this guide, we have carefully curated a list of the best SOC analyst tools that have been proven to be effective in real-world scenarios. We understand that SOC analysts play a critical role in safeguarding an organization’s digital assets, and the right tools can significantly enhance their capabilities.
Firstly, the guide provides an in-depth analysis of different types of tools that are commonly used by SOC analysts. These include network monitoring and analysis tools, endpoint detection and response (EDR) solutions, security information and event management (SIEM) platforms, threat intelligence platforms, and incident response orchestration tools. For each category, we have included a detailed explanation of the functionalities and features that analysts should consider when evaluating these tools.
Additionally, the guide offers insights into the key factors that organizations should consider when selecting SOC analyst tools. We delve into the importance of scalability, ease of use, integration capabilities, and vendor support. We also discuss the significance of automation and machine learning in SOC operations, and how these technologies can augment the capabilities of analysts.
Furthermore, the guide includes real-world case studies that highlight the practical application of the featured tools. These case studies provide a glimpse into how organizations have successfully utilized these tools to detect and respond to security incidents. By examining these real-life examples, SOC analysts can gain valuable insights into the potential benefits and challenges associated with implementing different tools.
To ensure that the guide remains up-to-date, we regularly update it with the latest information on emerging tools and technologies. We understand that the cybersecurity landscape is constantly evolving, and SOC analysts need to stay ahead of the curve to effectively combat new threats. Therefore, we strive to provide the most current and relevant information in our guide.
In conclusion, our “Best SOC Analyst Tools PDF” guide is a comprehensive resource that equips SOC analysts with the knowledge and tools they need to excel in their roles. By leveraging the insights and recommendations provided in this guide, analysts can enhance their ability to detect, investigate, and respond to security incidents, ultimately bolstering the overall security posture of their organizations.
The Content of the Guide
The guide is divided into several sections, each focusing on a specific aspect of SOC analyst tools. Here is a brief overview of the content you can expect to find:
- Introduction to SOC Analyst Tools: This section provides a high-level overview of the role of SOC analysts and the importance of having the right tools in place. It explains how SOC analysts play a critical role in monitoring and responding to security incidents, and how the right tools can enhance their effectiveness. The section also highlights the challenges faced by SOC analysts and the need for comprehensive toolsets to address these challenges.
- Key Features to Consider: In this section, we delve into the essential features that SOC analysts should look for when evaluating tools. We discuss topics such as log analysis, threat intelligence integration, and automation capabilities. We provide detailed explanations of each feature and explain why they are important for SOC analysts. Additionally, we offer tips on how to evaluate these features and make informed decisions based on the specific needs of your organization.
- Tool Categories: Here, we categorize SOC analyst tools into different types based on their functionalities. We cover areas such as SIEM (Security Information and Event Management), threat hunting, incident response, and more. For each category, we provide an overview of the tools available, their strengths and weaknesses, and the specific use cases they are best suited for. This section aims to help SOC analysts understand the different types of tools available and choose the ones that align with their organization’s security goals.
- Top Tools in Each Category: This section highlights some of the leading tools in each category. We provide an overview of their features, strengths, and weaknesses, helping you make informed decisions when selecting the right tool for your organization. We also include user reviews and ratings to give you a comprehensive view of each tool’s performance and user satisfaction. This section aims to simplify the tool selection process by presenting a curated list of top-performing tools in each category.
- Case Studies: To illustrate the practical application of SOC analyst tools, we present real-world case studies showcasing how organizations have successfully utilized these tools to detect and respond to security incidents. Each case study provides a detailed analysis of the incident, the tools used, and the outcomes achieved. By examining these case studies, SOC analysts can gain valuable insights into how different tools can be effectively deployed in various scenarios, ultimately enhancing their incident response capabilities.
- Best Practices: In this section, we share valuable insights and best practices for effectively implementing and optimizing SOC analyst tools within your organization. We cover topics such as tool integration, staff training, and ongoing monitoring. We provide step-by-step guidance on how to integrate different tools into your existing security infrastructure, train your SOC analysts to effectively use these tools, and establish processes for continuous monitoring and improvement. This section serves as a practical guide for SOC analysts to maximize the value of their toolsets and ensure their organizations are well-prepared to address evolving security threats.
- Future Trends: Finally, we discuss emerging trends and technologies that are shaping the future of SOC analyst tools. We explore topics such as artificial intelligence, machine learning, and cloud-based solutions, and how they are transforming the way SOC analysts operate. We provide insights into how these technologies can enhance threat detection and response capabilities, and offer recommendations on how SOC analysts can prepare for the future. By staying informed about the latest trends, SOC analysts can proactively adapt their toolsets and strategies to stay ahead of the evolving threat landscape.
Key Topics
Throughout the guide, we explore a range of key topics that are essential for SOC analysts to understand and master. Some of these topics include:
- Log analysis and correlation
- Threat intelligence integration
- Automated incident response
- Endpoint detection and response
- Network traffic analysis
- Vulnerability management
- Security orchestration and automation
- Cloud security
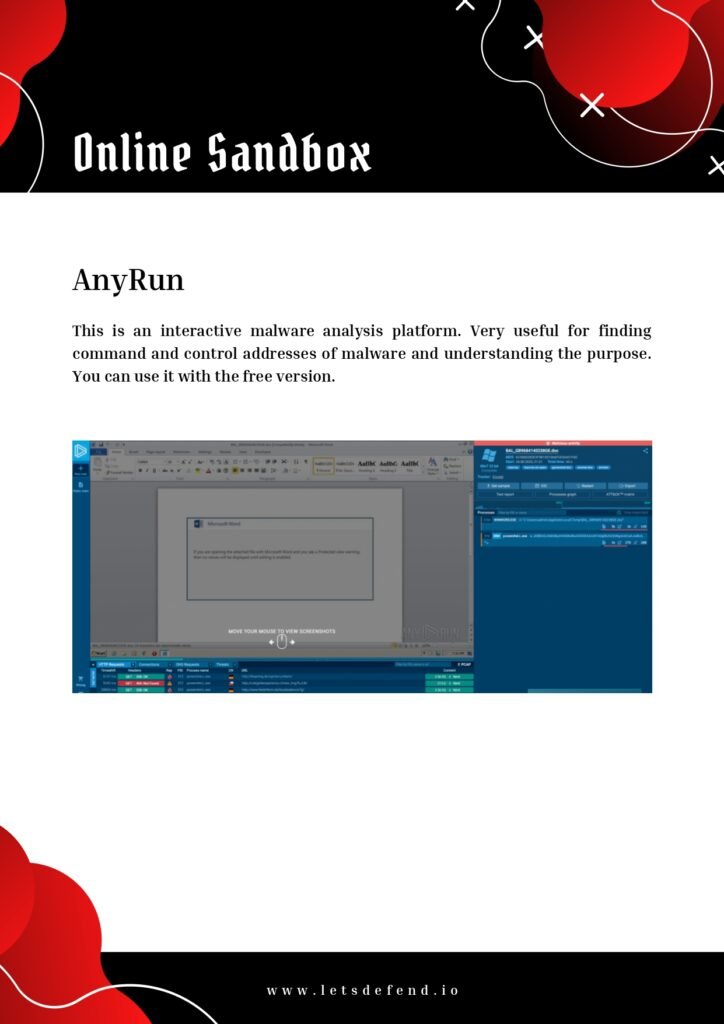
- Malware analysis
- Incident handling and escalation
- Forensics and investigation
- Security awareness training
- Security policy development
- Compliance and regulatory requirements
Log analysis and correlation is a fundamental skill for SOC analysts as it involves examining and interpreting log files from various sources such as firewalls, intrusion detection systems, and servers. By analyzing these logs, analysts can identify patterns, anomalies, and potential security incidents. This allows them to correlate events and gain a comprehensive understanding of the security posture of the organization.
Threat intelligence integration is another crucial topic covered in the guide. SOC analysts need to stay up-to-date with the latest threats and attack vectors to effectively detect and respond to potential incidents. By integrating threat intelligence feeds into their security systems, analysts can receive real-time information about emerging threats, malicious IP addresses, and indicators of compromise. This enables them to proactively defend against potential attacks and mitigate risks.
Automated incident response is a growing trend in the field of cybersecurity. With the increasing volume and complexity of security incidents, manual incident response processes are often inadequate. By implementing automated incident response tools and playbooks, SOC analysts can streamline their response efforts, reduce response times, and ensure consistent and effective incident handling. This topic covers the selection, implementation, and optimization of automated incident response systems.
Endpoint detection and response (EDR) is a critical component of modern security operations. EDR solutions provide visibility into endpoint activities, detect and respond to advanced threats, and enable proactive threat hunting. SOC analysts need to understand how to deploy and configure EDR systems, analyze endpoint telemetry data, and effectively respond to endpoint-based security incidents.
Network traffic analysis is another key topic explored in the guide. SOC analysts need to be able to monitor and analyze network traffic to detect and investigate potential security threats. By analyzing network packets, flow data, and log files, analysts can identify suspicious activities, detect network-based attacks, and identify compromised systems. This topic covers the use of network traffic analysis tools, techniques for traffic analysis, and the interpretation of network-based indicators of compromise.
Vulnerability management is an essential practice for maintaining a secure IT infrastructure. SOC analysts need to understand how to identify, assess, and remediate vulnerabilities in systems and applications. This topic covers vulnerability scanning tools, vulnerability assessment methodologies, and the coordination of vulnerability remediation efforts with system administrators and IT teams.
Security orchestration and automation is a critical skill for SOC analysts as it enables them to automate repetitive and time-consuming tasks, improve operational efficiency, and enhance incident response capabilities. This topic covers the use of security orchestration platforms, the development of automation workflows, and the integration of security tools and technologies.
In addition to these key topics, the guide also covers other important areas such as cloud security, malware analysis, incident handling and escalation, forensics and investigation, security awareness training, security policy development, and compliance and regulatory requirements. These topics provide SOC analysts with a comprehensive understanding of the various aspects of security operations and equip them with the necessary skills to effectively protect their organizations against cyber threats.
Download from Link
To access the “Best SOC Analyst Tools PDF” guide, please click on the following link: [download link here]. We hope you find this guide valuable and that it helps you enhance your capabilities as a SOC analyst.

















