With the rapid advancement of technology and the increasing reliance on digital platforms, the need for robust cybersecurity measures has become more critical than ever. Cyberattacks are on the rise, and hackers are constantly finding new ways to exploit vulnerabilities in systems and networks. It is essential for individuals and organizations alike to stay informed about the latest threats and vulnerabilities to protect themselves effectively.
Our “Top 100 Vulnerabilities PDF” guide is meticulously curated to provide you with a comprehensive overview of the most significant vulnerabilities that pose a threat to the security of your digital assets. We have analyzed and compiled a list of vulnerabilities based on their severity, impact, and prevalence in real-world scenarios.
Overview Of This PDF
Each vulnerability in the guide is accompanied by a detailed explanation, including the potential risks it poses, the affected systems or software, and the recommended mitigation strategies. We have also included real-life examples and case studies to help you understand the practical implications of these vulnerabilities.
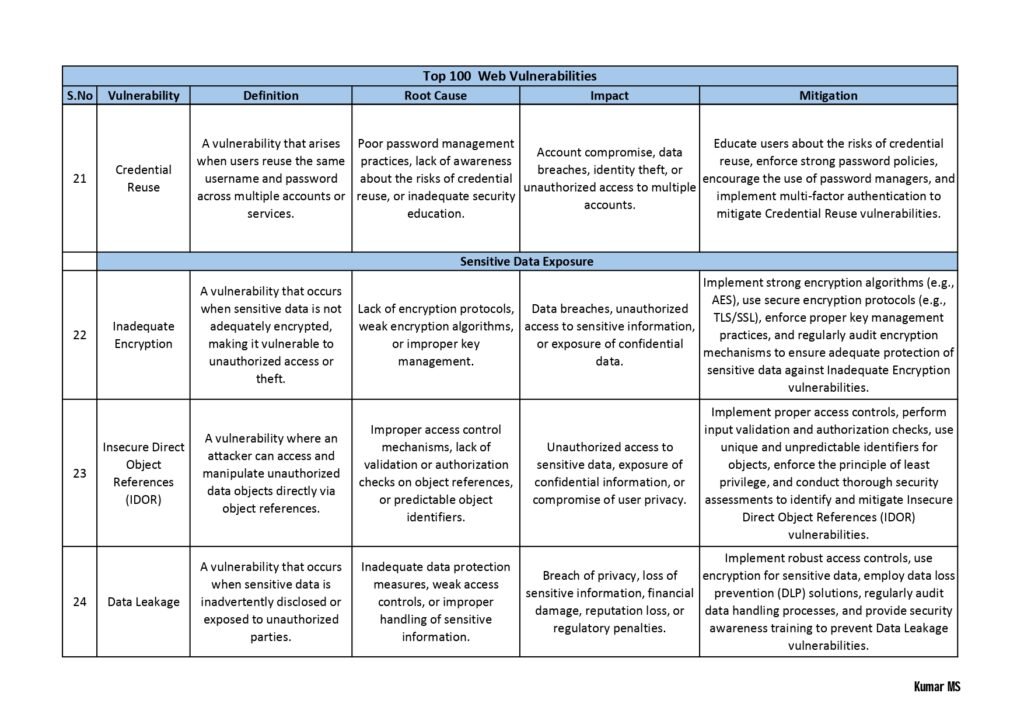
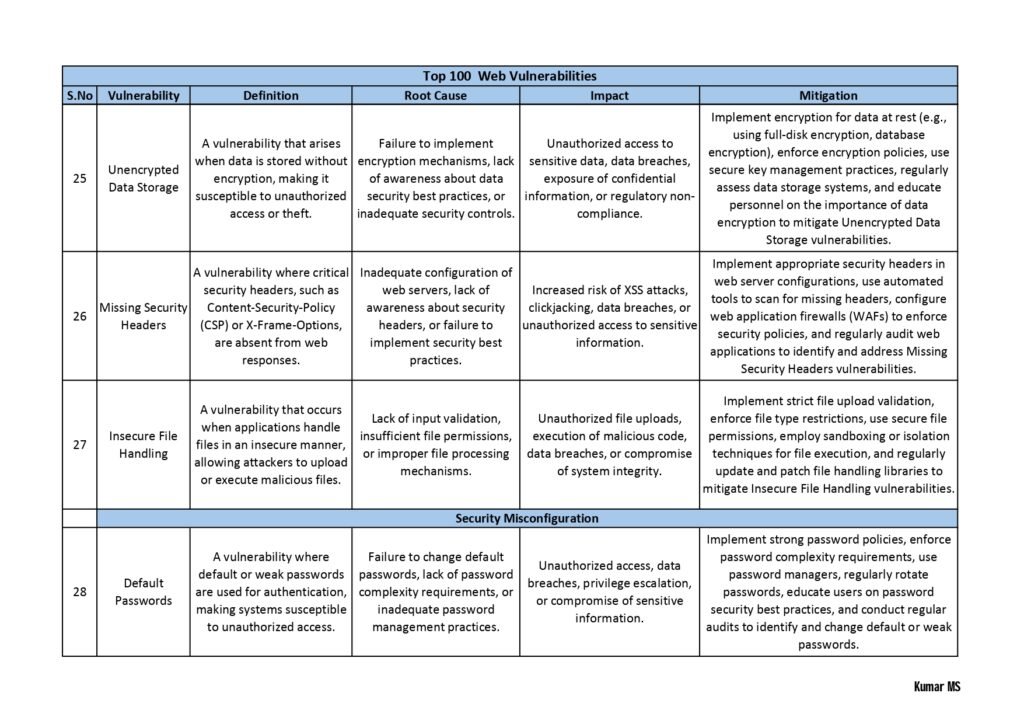
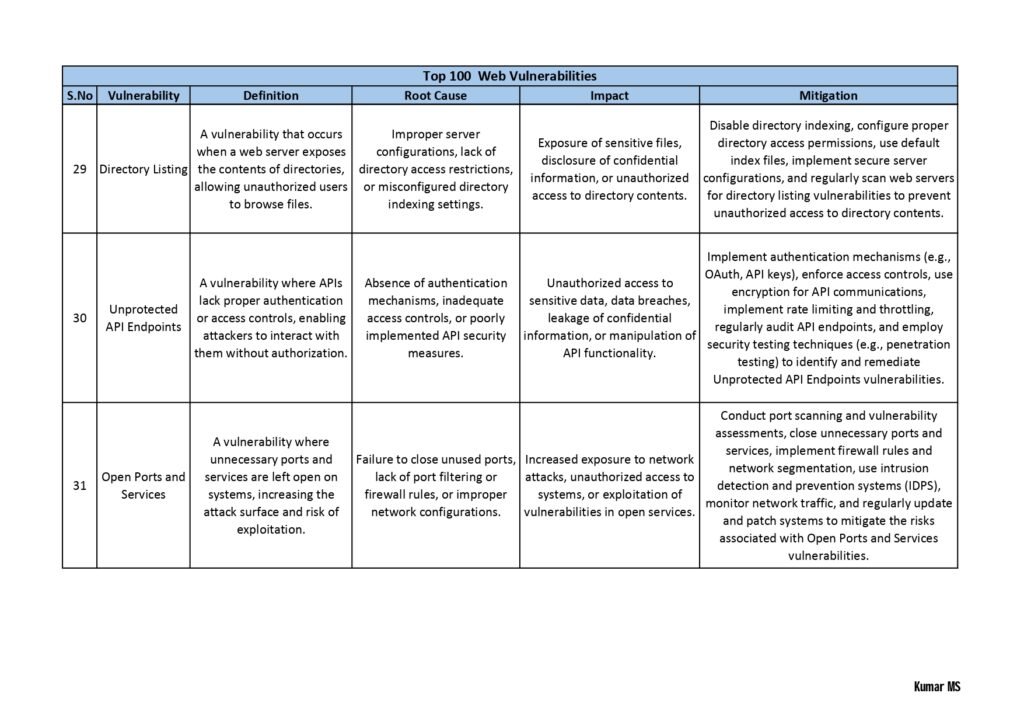
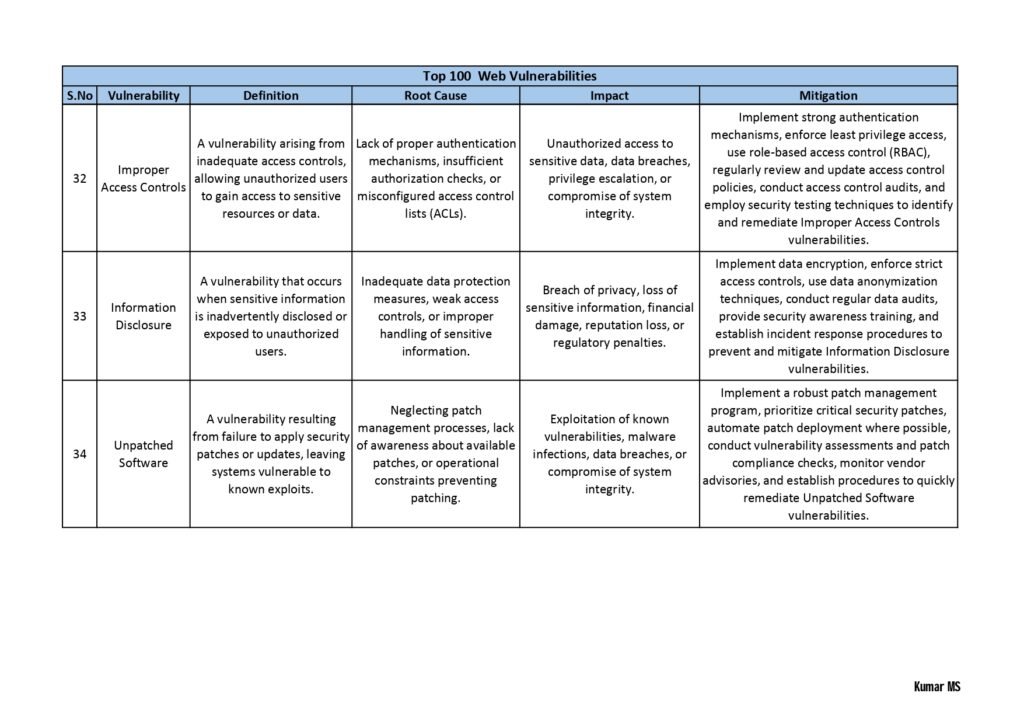
Whether you are a cybersecurity professional looking to enhance your knowledge or an individual who wants to safeguard their personal information, this guide will equip you with the necessary insights to make informed decisions and take proactive measures to protect yourself or your organization.
The Content of the Guide
The “Top 100 Vulnerabilities PDF” guide is divided into several sections, each focusing on a specific category of vulnerabilities. These categories include:
- Network Vulnerabilities
- Web Application Vulnerabilities
- Mobile Application Vulnerabilities
- Operating System Vulnerabilities
- Database Vulnerabilities
- Wireless Network Vulnerabilities
- Cloud Infrastructure Vulnerabilities
Each category delves deep into the vulnerabilities associated with the respective domain, providing detailed explanations, examples, and recommended countermeasures. By exploring these categories, you will gain a comprehensive understanding of the vulnerabilities that exist within various aspects of technology.
Now, let’s take a closer look at each of these categories to understand the specific vulnerabilities they cover:
- Network Vulnerabilities: This section focuses on vulnerabilities that can be exploited through network connections. It covers topics such as open ports, weak encryption protocols, misconfigured firewalls, and insecure remote access.
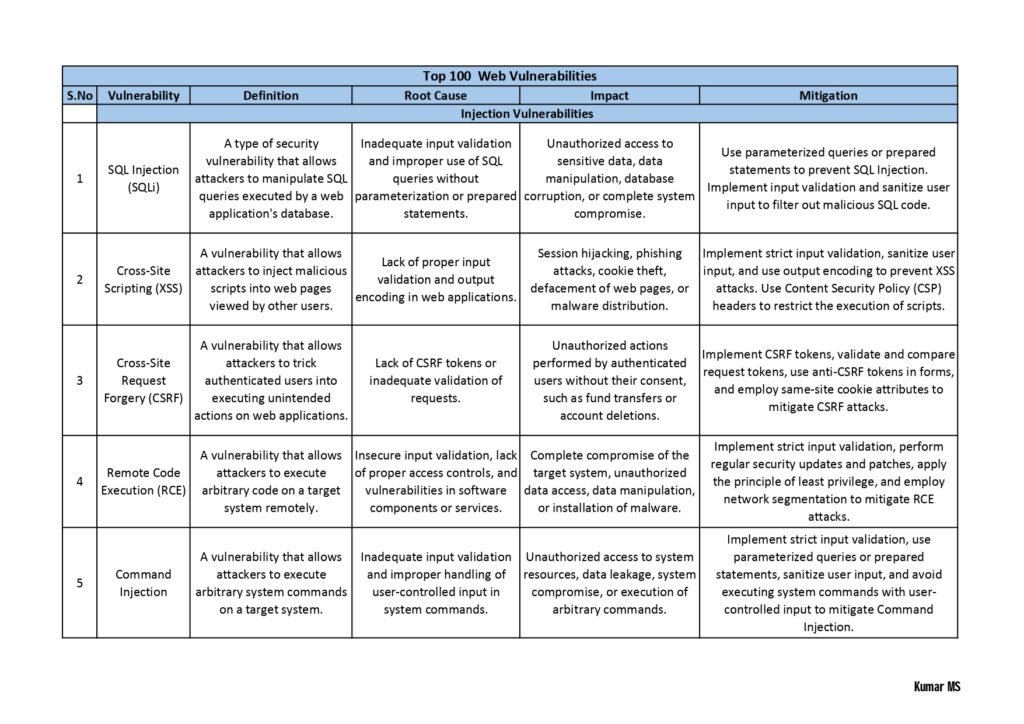
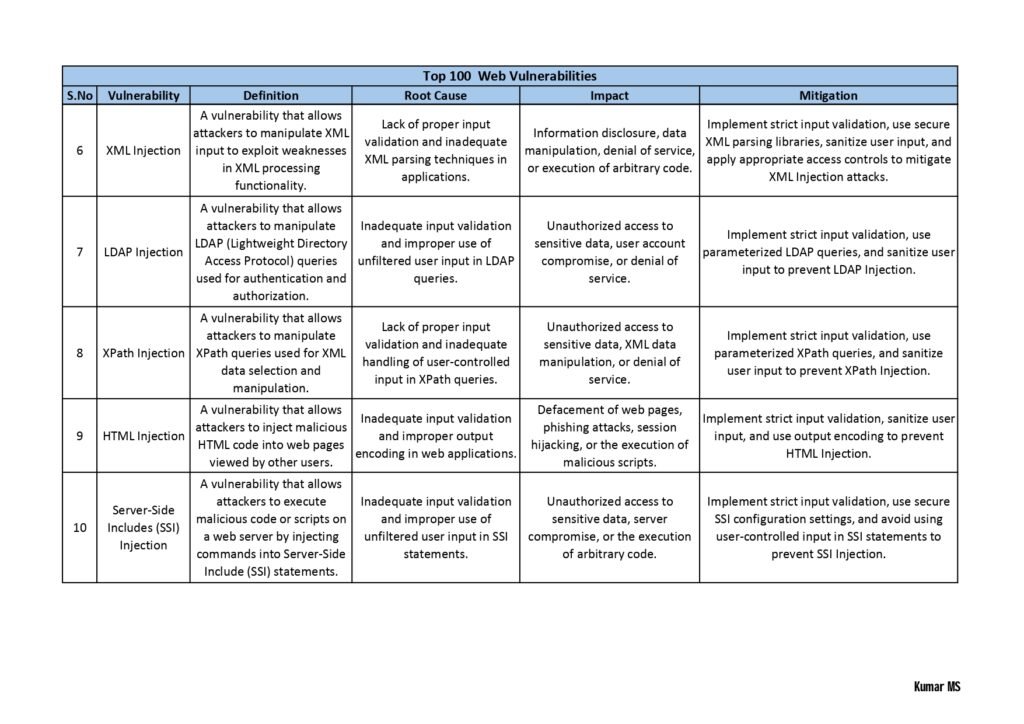
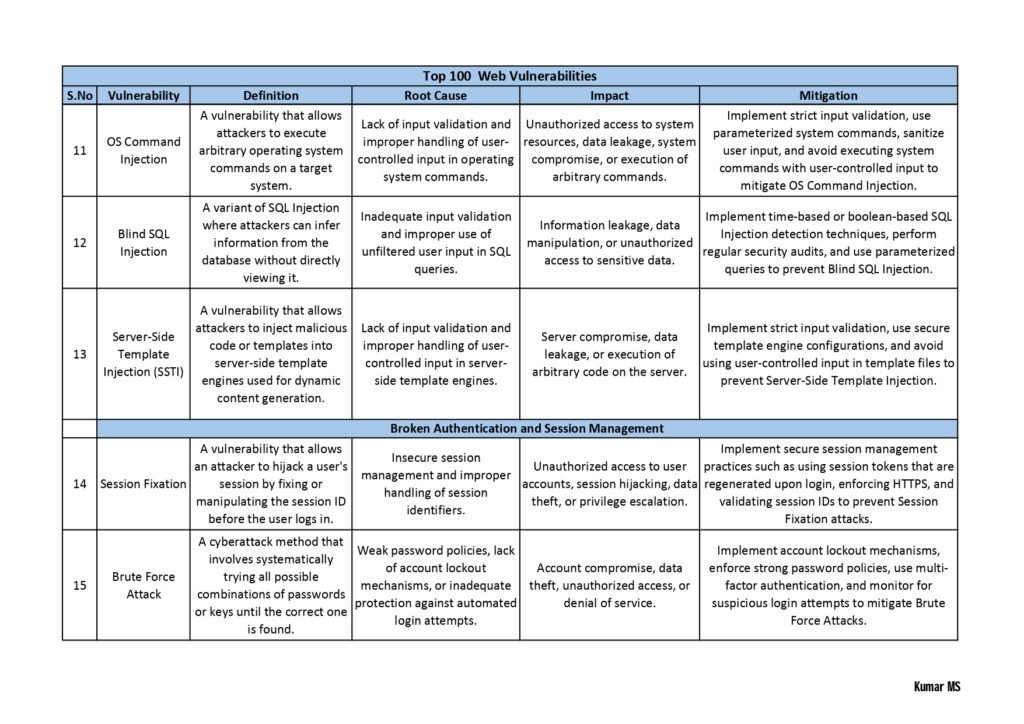
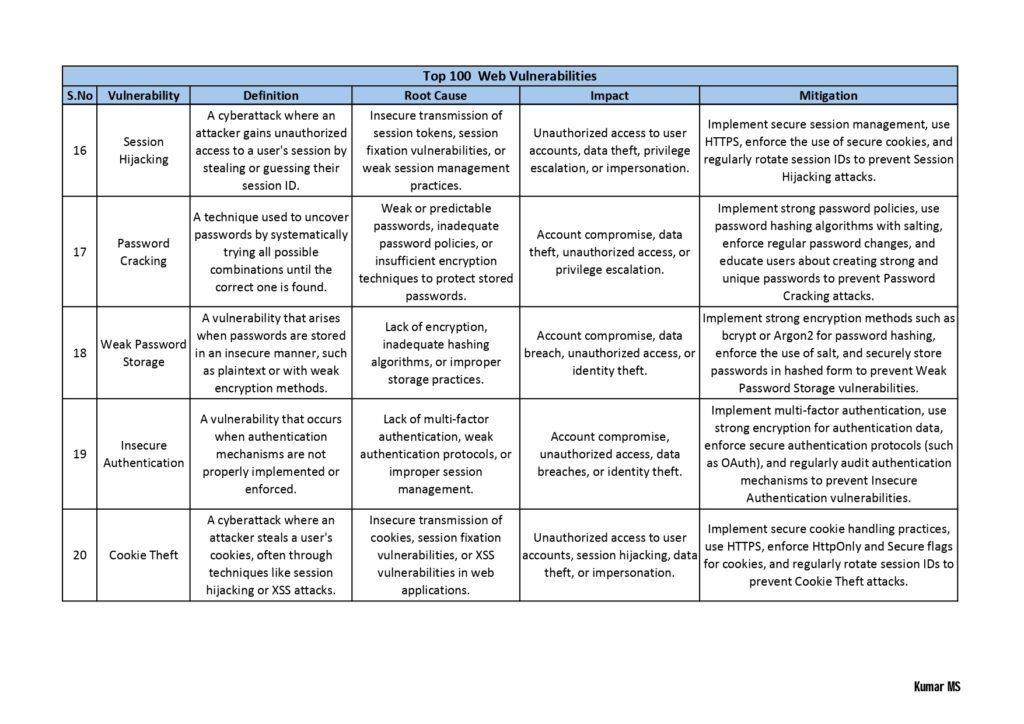
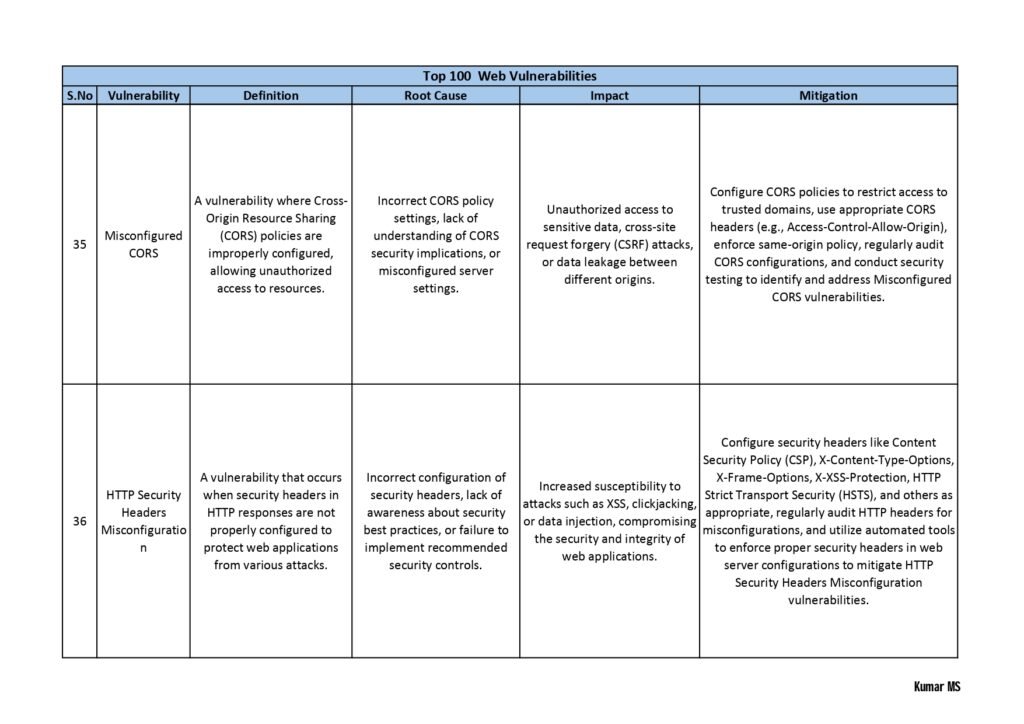
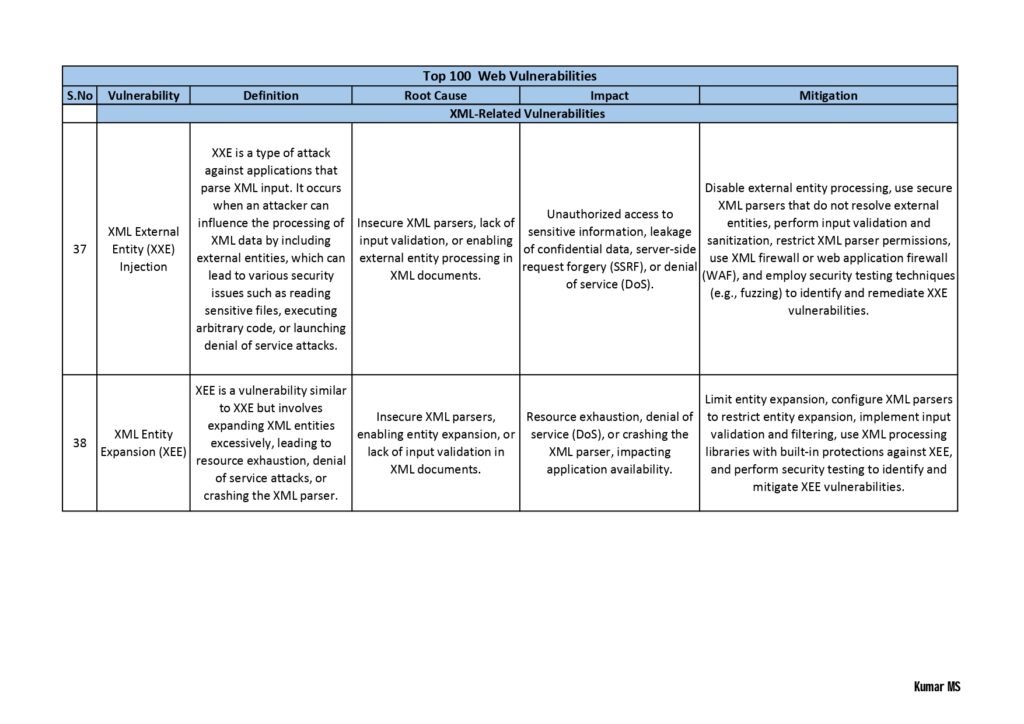
- Web Application Vulnerabilities: Here, the guide explores vulnerabilities that affect web applications, including cross-site scripting (XSS), SQL injection, insecure direct object references, and session hijacking. It provides real-world examples and guidance on how to mitigate these risks.
- Mobile Application Vulnerabilities: With the increasing popularity of mobile applications, this section addresses vulnerabilities specific to mobile platforms. It covers issues like insecure data storage, insufficient encryption, insecure communication channels, and insecure authentication mechanisms.
- Operating System Vulnerabilities:
This category focuses on vulnerabilities that affect operating systems, including both desktop and server environments. It discusses weaknesses such as outdated software, misconfigured permissions, privilege escalation, and insecure default configurations. - Database Vulnerabilities:
Databases are a crucial component of many applications, making them attractive targets for attackers. This section explores vulnerabilities related to database management systems, such as SQL injection, weak access controls, insecure data storage, and misconfigured database servers. - Wireless Network Vulnerabilities:
As wireless networks become ubiquitous, it is essential to understand the vulnerabilities associated with them. This part of the guide covers topics like weak encryption protocols, rogue access points, man-in-the-middle attacks, and wireless sniffing. - Cloud Infrastructure Vulnerabilities:
With the increasing adoption of cloud computing, securing cloud infrastructure is of utmost importance. This section discusses vulnerabilities like misconfigured security groups, weak access controls, data leakage, and insecure APIs.
By delving into each of these categories, the “Top 100 Vulnerabilities PDF” guide provides a comprehensive overview of the vulnerabilities that exist within various aspects of technology. It equips readers with the knowledge and understanding necessary to identify, assess, and mitigate these vulnerabilities effectively. Whether you are a cybersecurity professional, a developer, or an IT manager, this guide will serve as a valuable resource in securing your systems and applications.
Key Topics
Within the “Top 100 Vulnerabilities PDF” guide, you can expect to find in-depth coverage of key topics such as:
- Common network vulnerabilities and their potential impact
- Web application vulnerabilities, including cross-site scripting (XSS) and SQL injection
- Mobile application vulnerabilities, such as insecure data storage and insecure communication
- Operating system vulnerabilities, including privilege escalation and buffer overflow
- Database vulnerabilities, such as weak authentication and SQL injection
- Wireless network vulnerabilities, including weak encryption and rogue access points
- Cloud infrastructure vulnerabilities, such as misconfigurations and insecure APIs
- IoT vulnerabilities, including insecure firmware and default credentials
- Physical security vulnerabilities, such as unauthorized access and social engineering
- Human factor vulnerabilities, including phishing attacks and insider threats
Number of Guide (33 Pages)
The “Top 100 Vulnerabilities PDF” guide consists of 33 pages packed with valuable information about the vulnerabilities discussed earlier. Each page is filled with insights, examples, and actionable recommendations to help you understand and address these vulnerabilities effectively.
Download from Link
To access the “Top 100 Vulnerabilities PDF” guide, simply click on the following link: [From here].
Once downloaded, you can save it on your device or print it for offline reference. We highly recommend keeping this guide handy as a valuable resource for enhancing your knowledge and strengthening your cybersecurity defenses.

















